A new twitter spam campaign is making rounds, infecting users with rogue anti-virus malware. The spam mail attempts to convince the user that someone was trying to steal their Twitter account information, and to download a “secure module” to protect their account.
The email that begins the attack looks like authentic communications from Twitter with a link ostensibly to twitter.com.
However, the link provided by the attacker does not actually link back to Twitter, but to a Google Groups page where the malware is currently hosted. The use of Google Groups to distribute malware has been a continuing trend since eSoft first blogged about it last month.
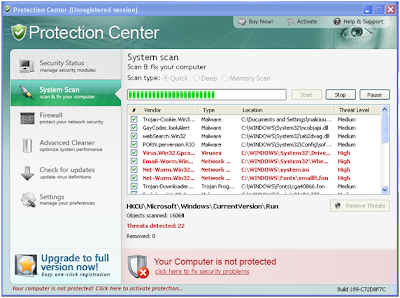
Virus Total shows a moderate detection rate of 21 out of 41 anti-virus companies that currently detect this threat. For users whose anti-virus software does not detect the threat, a download will result in an infection with the rogue anti-virus malware. The malware launches a “Protection Center,” which runs a fake anti-virus scan ostensibly revealing the machine is infected by a slew of viruses. The user must activate the software to remove the bogus infections, handing their credit card info over to cyber criminals.
eSoft is flagging these infected Google Groups pages as Compromised.