When it comes to securing the enterprise, we pay close attention to those obvious infrastructure security assets in the guise of Firewalls, IPS, and IDS systems, along with the assurance that we have delivered against the organisations governance and compliance regime. It may even be that we have resorted to utilising the external resources of an MSSP [Managed Security Service Provider] to accommodate our internal/external security testing requirements, not to mention management of generated logs.
And on top of this, we may even enjoy the oversight of a QSA [Qualified Security Assessor] to look-on the activities from the higher ground of PCI-DSS hill, just to assure we are compliant and secure. The problem is however, time and dirty hands has proven that, notwithstanding such efforts which may have been invested into, the most surprising revelation of all can be, compliance and governance do not necessarily equal security - In other words, according to this approach, an organisation can be both insecure and compliant at the same time.
Known Problems
So to scope this article out, please allow me to introduce a number of areas of known insecurity which can be overlooked, misunderstood, or simply ignored. And in context with this, I am focusing the subject of securing those complimentary [auxiliary] assets which reside in the corporate space, as indirect supportive technologies which support sensitive operations, data-at-rest, and data-in-transit.
Securing those Vital URL’s: There are multiples of organisations I can think of who have failed to secure business-important URL’s - URL’s which, if left exposed, could see their operations compromised. Say a result of a mirrored site which reveals the TLD of that brand. For example, where the brand owner owns the .com domain in the UK, but has failed to secure the .co.uk; or given we are now trading in Europe, we commit a well know school-boy error of failing to recognise the importance of the well-established .eu extension.
This of course may not have been considered to be an issue for many carless organisation - that is, until such time as the unsecured asset is procured by another party, and parked, or set into operation. In fact, consider an attacker, or criminal utilising a very simple tool such as HTTrack [https://www.httrack.com/] to acquire all, or some of the targeted site content. Then post applying some changes, deploy with some miscreant intention. The question is, would this be of concern? [See Fig 1 below].
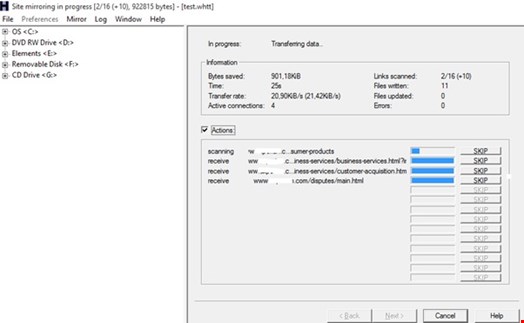
In a number of cases that I have encountered, the area of managing multi-domain profiles for some reason, can impose management challenges ranging from low levels of governance being applied to brand associated domain space.
For example, with one TLD being residing under a .com, with others under a .co.uk, through to disjointed ownership and administration around such multiple domain assets, which has seen a number of organisation actually lose temporary control of their critical domain assets when they forgot to renew! And lastly of course, DNS Domain Management of such disparate environments, can be left exposed to dysfunctional management that drops the ball into the hands of the potential attackers.
Something else that can manifest out of domain management confusions is leaving the zone transfer feature enabled. This enablement can potentially allow other interested parties to transfer out, what amounts to internal sources of intelligence which on most occasions, should remain protected and inaccessible to unauthorised users. However, even when such exposures are located, a challenge may still exist when trying to educate the exposed parties as to the associated security implications of such an unwise configuration.
For instance, such an exposure can provide an unauthorised onlooker with a view of internal assets, which could then assist with discovery of internal targets, or jump-off-points to mount secondary level internal attacks. And when such interesting internal assets are discovered, say in the form of a server storing/processing business information, or critical information objects, this imposition could then in turn lead on to provide the platform to accommodate an actual direct, or indirect compromise.
Hard-Coded Objects and Web-Side Code
In relation to one particular case where a zone transfer was in place, notwithstanding the corporate failure to understand the implication of the easy zone transfer, the situation got worse.
Because of poor-security practices being applied by the company’s internal developers, they also failed to appreciate the fact that, by simply using a web-browser to interface the targeted server directory, it was possible to download scripts which contained hard coded user id’s and the associated account password – and all this from a seemingly secure, firewalled domain which was at that time considered compliant with a number of desired security standards.
Notwithstanding that organisations have delivered tokenisation, and the associated PCI-DSS compliant zones into their areas of sensitive operations, achieving that PCI tick-in-the-box, all is not always well. For instance, when it comes to those external (ancillary) supporting systems in the form of Web Servers, it is here where such sensitive data in the guise of transactional credit card information can also exist in the clear - in organisations which are supposedly protecting the PCI-DSS data assets, whilst at the same time potentially allowing all who have access. This can also include those supportive third parties to view, and maybe even abuse their authorised access rights.
Thus whilst it may be a case that the internal known systems are secured to meet the said security expectations, it is the unknown unknowns of operability which can be extant to potentially exposing card data.
Potential Exploitation
Getting back to that common exposure which is far too often discovered to exist, even on the sites of the most prestigious of organisation. Yes, this is the world of ‘OSINT’ [Open Source Intelligence] which for some reason suffers from its implicit danger, at best being misunderstood, and again, at worst being ignored.
Sadly, where such toleration of this adverse circumstance of exposures do exist, conjoined with say a modicum of data leakage, poor quality standards around document management and cleansing procedures, you can really start to see the subliminal creation of isolated of cross-company high-value intelligence seepage.
Add to this the external dissemination of company documentation in the form of uncleansed meta-carrying documents, and possibly the association of carless use of social networking, you can imagine the potentials for exploitation stating to creep in. And whilst the ignorant-publisher may be unaware of the intrinsic value of such objects, they may be assured that these offerings will be well received by the awaiting criminal public.
For example an extraction obtained from an open source exposure acquired from a well-known bank which had been aware of their, shall we say leakages, for over two years still continue to bleed intelligence from their public net-face. To put this into context, in this particular case, imagine how useful it would be to an interested adversary who discovers that such a target as this are unintentionally disclosing multiples of sensitive user email addresses with .gov.gsi extension, along with their associated names and other valued intelligence, in some cases also including their personal extension numbers.
Moreover, when it comes to the joining of more than one entity in the form of acquisition and mergers, it is in such circumstances when the security cracks can really start to show. In such situations as these it is not uncommon to see the chenobol effect take a grip, with somebody asserting that someone else has responsibility for a mind-the-gap issue, which can often see some, or even all of the above falling into a black hole of security confusion. And then add to this the implications where multiples of third party providers who are in existence, and you are seeing the early signs of the perfect black storm approaching over the newly conjoined corporate horizon.
Exploiting Assets
As boring as all this may look, the end result is of course the desired level of all-encompassing security attention we are seeking apply - focusing beyond the corporate arena of compliance.
Here we need to apply our imagination, and consider the prospective landscape of the unknown exposures related to data-flows, and/or those ancillary areas which do not necessarily reside under an obvious security banners. We need to use our imagination and skill to interpret the transactional paths which could be, or are being leveraged to compromise some of those vulnerable unintentional exposed areas, exposing valuable corporate assets, and clients to the prospect of direct, or indirect abuse of the cyber-criminal.
In order to deal with the new breed of disease arriving in the form of the skilled criminal miscreant, we need more than a general practitioner to engage the logical tumour. In this new age, we need specialist Cyber Surgeons who can recognise the symptoms of the condition, with the ability to delve deeper than the obvious indications of superficial rash, and to get deep down and cyberlogical to understand the root cause symptoms, in order to dispense a chip-full of mitigating medication.
