
Equipped with a virtual Wi-Fi feature, the newly launched Microsoft Windows 7 operating system now makes it easy for users to turn their laptops and netbooks into a soft access point. This soft access point can be configured on the built-in Wi-Fi adapter or on an external Wi-Fi adapter plugged into a Windows 7 machine. Free software applications from the web, such as the one provided by Connectify, offer an easy-to-use interface to configure such access points, with various options.
A soft access point configured on a Windows 7 machine functions almost similar to a physical Wi-Fi access point to which other Wi-Fi devices can connect to as Wi-Fi clients. Also, it allows users to share a particular network accessible on the laptop with connected Wi-Fi clients.
A soft access point running on a user’s Windows 7 machine enables the creation of a Wi-Fi personal area network (PAN), which is easy to setup, easy to carry, and managed by the user. Thus, a Windows 7 user is no longer required to carry a physical access point device and the optional power charger cord for this device to setup a Wi-Fi PAN. In addition, users are relieved from accessing and going through the complex configuration screens of a typical physical access point device.
Although a traditional Wi-Fi ad-hoc mode is also available for users to set up their Wi-Fi PAN without the need for a physical access point, the virtual Wi-Fi capabilities of Windows 7 has advantages over this mode due to two basic facts. First, it allows a Wi-Fi adapter to run the soft access point (to setup Wi-Fi PAN) and simultaneously work as Wi-Fi client to access a particular Wi-Fi network. Second, the soft access point enables central management/monitoring of configured Wi-Fi PAN, as in case of coporate Wi-Fi networks.
Wi-Fi users should be excited about this feature. Evidence of this excitement is the fact that Connectify recently became one of top networking software downloads.
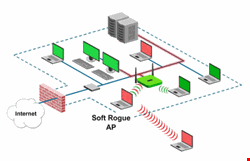
However, such an easy method for setting up an access point using the virtual Wi-Fi capability of Windows 7 has inflated the exposure of enterprise Wi-Fi security risks, which is already a nightmare for many network administrators. The additional risk surfaces when a soft access point is running on an employee’s end point (which is upgraded to Windows 7) or on a guest Windows 7 machine.
There can be number of reasons for running these soft access points, some of which are identified below:
- Providing network access to Wi-Fi devices, such as smart phones, owned by an employee or guest but restricted from network access
- Sharing/exchange of data with colleagues or Wi-Fi devices, such as smart phones, etc.
- Malicious intent of an employee or guest
- Providing network access to Wi-Fi users experiencing weak/no Wi-Fi network signal
- Providing access to network segments for Wi-Fi users who cannot access this segment through Wi-Fi, either due to unavailability or lack of authorization to access the network segment
- Providing access to an unauthorized network for organizational Wi-Fi users or various Wi-Fi devices
However, such an active soft access point inside an organization’s premises can put IT infrastructure at risk in following ways:
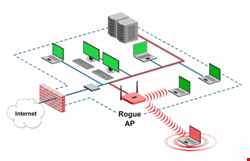
Unauthorized Access to Network: This could potentially happen when a Windows 7 machine inside the premises has access to the network (which is usually the case for an employee or visitor’s machine) and shares this network through a soft access point running on it. In such a scenario, the soft access point is just like a traditional rogue access point.
Traditionally, a rogue access point is considered to be any unauthorized physical access point device plugged into a LAN port on a network. However, a rogue in the form of a Windows 7 soft access point does not require any physical access to a LAN port. Also, it will be immune to wired side techniques (as applicable for traditional rogues) for detection and blocking. As many of us already know, a corporate Wi-Fi rogue provides a gateway for malicious users to hack into a network and execute their malicious intent. This malicious intent can range from disruption of network service to theft of confidential data.
Connecting to Unauthorized Networks: With a soft access point running on a Windows 7 machine, an employee can easily share some unauthorized network access with fellow employee’s inside an organization’s premises. Access to such an unauthorized network is possible using adapters for technologies, such as WiMax, 2G, 3G, etc., or a possible Wi-Fi association with a neighboring or malicious Wi-Fi network. Organizational end points that have access to unauthorized networks in this way do not follow restricted network access policies and can be subjected to possible affliction due to the installation of malware, trojans, on so on.
Solutions
Considering the increased interest in upgrading to Windows 7 and anticipated widespread adoption of Windows 7 by users around the globe, it is important for an administrator to actively detect and block any soft access point running on a Windows 7 machine connecting to an organization's network. This is easily achievable for the administrator if their organization has already deployed a well-built and updated WIPS (wireless intrusion prevention system) on the premises.
Also, protection can be achieved by installing a wireless security agent on end points that disables operation of a soft access point. However, you can never be sure whether a guest Windows 7 machine has such a security agent installed and running.
Ajay Kumar Gupta is the acting tech lead, engineering, at AirTight Networks, a global provider of enterprise Wi-Fi security and performance management products. He is a frequent contributor to some leading security magazines and AirTight’s blog.