Cyber-risk truly is business risk. Business are actively digitizing, and meanwhile governments are putting in place policies to promote digitalization and smart-city projects. Certainly, this helps citizens and enterprises to adopt technology advancement; on the downside, the continuous increase in cyberattacks, in both frequency and sophistication, pose significant challenges for people that must defend their organization’s data and systems from threats.
Most enterprises have outsourced their important IT security management tasks to MSSP (managed security service providers), and even fewer retain their internal SOC (security operations centers). These businesses generally started their journey only with security device monitoring management services (such as managed firewall services) and slowly added security event monitoring using SIEM solution components. Additionally, the growing threat landscape and difficulty in hiring security cybersecurity professionals with the needed expertise makes it more difficult for enterprises to understand the tools, techniques and tactics used by adversaries.
Need for Cyber-Threat Information Sharing
In recent years, the need for cyber threat intelligence has become better understood by governments and organizations. NIST encourages greater sharing of cyber-threat information among organizations.
In today’s large security product and service industry, solutions such as firewalls, endpoint protection and managed security services (MSSP) are enhanced by threat intelligence capabilities. The threat intelligence cycle has key steps, as depicted in the figure below.
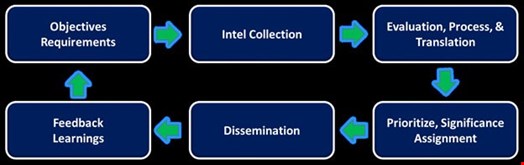
According to Gartner, “Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications and action-oriented advice about an existing or emerging menace or hazard to assets. This intelligence can be used to inform decisions regarding the subject’s response to that menace or hazard.”
Cyber Threat Intelligence Feeds For Security Operations
In most cases, enterprises need to detect the threat quickly and avoid wasting time investigating false negative alerts, thereby remediating the vulnerabilities and mitigating the attack vector efficiently. These are typical questions that the security operation center will have:
- Has our sensitive information been leaked?
- What threat actors could be targeting my organization’s capabilities in the coming months?
- Who are my top adversaries? Are they credible?
- Can I be advised of their activity within a short period of time of it occurring? Which underground sites do they frequent? Who is known to be associated with these adversaries?
- Is a connection to this Internet Protocol (IP) address bad? Who owns the IP? To which internet service provider (ISP) is this IP address connected? What other IP addresses are registered by this company?
- Is this URL dangerous? Who registered the domain? Have they registered others? If yes, which ones? Which types of threats were served from this website? Is other malicious activity linked to this URL?
- Which vulnerabilities in my environment are actively being exploited “in the wild”? Who are the threat actors selling or using these vulnerabilities? Which malware and other threats are leveraging these vulnerabilities? What types of organizations are being attacked via these threats?
- Is this “Zero Day” attack rumor true?
- What do the bad guys know about my organization and its staff? Are they selling access to my systems or my intellectual property?
When cyber-threat intelligence feeds can provide answers to the above questions, it allows security teams to more efficiently address threats.
Use Cases of Security Telemetry Enrichment with Cyber-Threat Intelligence
Taking a use-case-centric view is still the ideal and pragmatic way for the SOC to start a journey with cyber-threat intelligence and improve the overall security program. A few use cases/examples include:
- SIEM tool integration is useful for maintaining threat watch lists with existing logs flowing in from existing SIEMs. Threat intelligence data is overlapped on top of existing logs to detect threats by matching indicators of compromise (IOCs), such as IP addresses, file hash and domain names (examples: IBM XForce Threat Intelligence, EclecticIQ’s Fusion Center, Anomali).
- Threat intelligence has been a boon for IDP (intrusion detection and protection) in recent years, and many clients report improved detection and blocking capabilities for a range of threats simply by enabling the intelligence subscription for their IDP systems (examples: Trend Micro’s Reputation Digital Vaccine for its TippingPoint IDP, Palo Alto Network’s MindMeld).
- Phishing is a pernicious and prevalent threat that remains an effective way to gain access to organizations’ resources. Threat intelligence can help identify elements of phishing campaigns to speed up detection/response actions and help with proactive measures, such as prevention/prediction (examples: Proofpoint, ThreatConnect).
- Vulnerability management prioritization has moved away from thinking about vulnerability severity. Instead, the No. 1 priority is on “which of your vulnerabilities are being exploited in the wild.” Threat intelligence gives organizations the ability to determine which vulnerabilities present the biggest risks (examples: Kenna Security, Recorded Future).
- Surface, “Deep” and “Dark” Web Monitoring customers can use threat intelligence services to get prior warning of threats and better understand how the threats work and where they’re being seen. This helps them to perform brand monitoring (examples: ZeroFOX, Kela Targeted Threat Intelligence, SpyCloud).
There are many cyber-threat intelligence service providers in the market, and the number appears to be growing. Not all services that are marketed as threat intelligence actually provide that type of content, so it is important to understand what problem customers are trying to solve. While both commercial-based premium services and open-source feeds exist in the market today, security operations need to validate the solutions that help them to acquire, aggregate and act upon the threat intelligence that they need.
