The year is 2020 and the terrorist organization known as ISIS just targeted a major city in the US - bringing their emergency services to the breaking point, forcing their transport systems to shut down, and leaving the city in complete darkness.
This attack, orchestrated by the terrorist organization, was due to a series of cascading events and some of the most complex cyber-terror attacks that the world has ever seen.
Thankfully, these events did not occur today, nor have events like them ever occurred in global history. They are, however, a scenario written by Kyle R. Brady, a researcher at Pennsylvania State University, and are designed to help other researchers respond to and mitigate complex cyber-terror attacks.
To date, we haven’t seen cyber-terror attacks meet the capability of physical terror attacks. That being the case, however, this type of hypothesized research shows us that these types of attacks are possible and could occur in the near future.
To understand how we can protect ourselves from these types of attacks we must first look at the history of ideological cybercrime (cybercrime motivated by political, religious, or moral beliefs - primarily cyber-terrorism and hacktivism).
A History of Ideological Cybercrime
Over the past 25 years, the ideological cybercrime landscape has changed exponentially, with the below diagram highlighting some of the key historic events.
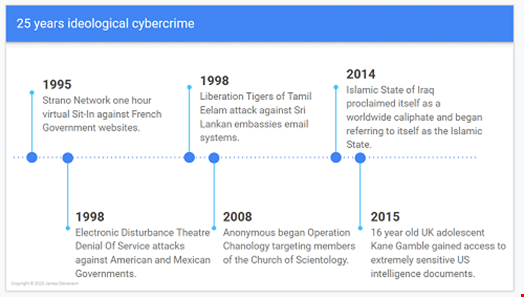
From virtual sit-ins and denial of service attacks, to terrorist organizations adopting cyber capability and hacktivists targeting US government officials, it can be seen that the scope and impact of ideological cyber-crime has greatly increased over time. This timeline is, however, missing the last five years as well as any indication of what’s next.
Looking back at Brady’s scenario, as well as the fact that these cybercrime activities have been increasing in impact over the last few years confirms that not only are more severe and damaging cyber-attacks possible but also likely. With this in mind, what can be done to protect against these types of attacks?
Predicting Cybercrime
Blue and red teaming, anti-malware tools, and data science approaches all function as effective means of cyber-attack prevention, however, what if we could predict and stop these attacks before they occur?
When building predictive technologies for detecting hacktivism and cyber terrorism, inspiration can be taken from other predictive techniques. Predictive policing, for example, is an approach for predicting terrestrial crime via either identifying a specific individual’s likelihood of re-offending or by identifying location hotspots where crime may occur.
While there are many drawbacks of predictive policing and machine learning approaches, as a whole, many police forces have stated that they have seen drastic changes in the policing landscape after implementing such technologies.
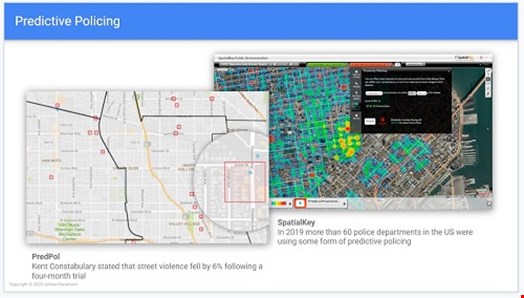
As predictive policing approaches primarily focus on terrestrial crime they aren’t overtly applicable when attempting to predict cybercrime, such as cyber terrorism and hacktivism. That being the case, when predicting cybercrime, new approaches need to be adopted.
Inspiration can be taken from psychology personality prediction techniques, such as Behavioural Residue and Digital Footprinting. Both of these models state that unconsciously people leave a trail behind themselves daily.
Behavioural residue identifies characteristics from one's choice of clothing, to how messy their desk is, to what books they’re reading. On the other hand, digital footprinting identifies virtual characteristics, from: likes on Facebook, to re-shares on Twitter, and choice of profile picture.
All of these characteristics can be used to identify an individual as well as to identify their personality. With this in mind we can take components from these approaches, as well as taking components from predictive policing to implement a predictive approach applicable to predicting ideological based cybercrime.
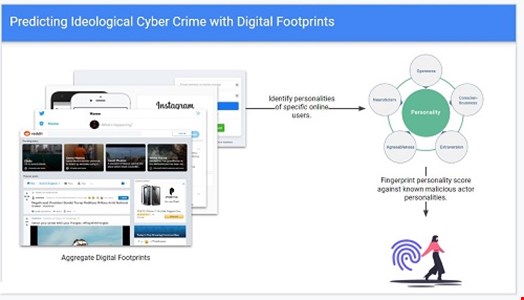
The below diagram details this process.
- Information is aggregated from a specific subject of interest’s (SoI) online presence (IRC channels, forums, social media, etc)
- Their personality fingerprint is identified from these digital footprints
- This personality fingerprint is compared with fingerprints from known malicious actors, to identify if the SoI shares any characteristics and in turn is likely to commit cybercrime
All things considered, for now, these types of predictive technologies don’t exist. However, as hacktivism and cyber terrorism becomes more impactful and far-reaching in society so do these defences and predictive measures also need to innovate.
Thanks for reading this article, I hope you enjoyed it. My name’s James, and I’m a researcher at the University Of Bristol. I’m currently amid a PhD looking at approaches for predicting ideologically motivated cybercrime. If you have 5 to 10 minutes and a Twitter, Instagram, or Reddit account it would be great if you could complete this questionnaire to help with the research. https://universityofbristol.eu.qualtrics.com/jfe/form/SV_d0tCAiDu6rdT62p
