Ransomware attacks have seen a sharp rise this year and hospitals have been particularly vulnerable since the start of COVID-19. According to the Microsoft Digital Defense Report 2020, hackers are rapidly increasing both the sophistication and frequency of cyber-attacks, with ransomware being the most common security breach method. The report mirrors findings from new research by Check Point which revealed that ransomware attacks doubled in Q3 2020 in the US, with healthcare being the most targeted industry.
The recent threat led the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI) and the US Department of Health and Human Services (HHS) to issue a joint advisory warning hospitals and healthcare providers about “an increased and imminent cybercrime threat.” The alert details malware used to carry out ransomware attacks and ways to mitigate them.
The impact of the ransomware attacks is already being felt across the healthcare industry. Examples of healthcare providers added to the tally of ransomware victims this year include:
- Sonoma Valley Hospital suffered a ransomware attack that impacted all of the hospital’s computer systems. In response to the attack, the hospital quickly stopped the incident by taking its electronic systems offline and didn’t pay any ransom
- Ascend Clinical was breached after an attacker deployed a successful phishing scheme that led to a ransomware attack. As a result, the data of over 77,000 individuals was compromised. It was unclear whether the ransom was paid or not
How Ransomware Attacks Work
Ransomware is a type of malicious software that encrypts files and demands payment for a key to decrypt the data. The aforementioned advisory explicitly warns hospitals about Ryuk ransomware, which works as follows:
- Attackers deliver Trickbot or Emotet Trojans via phishing emails to trick users into clicking on malicious file attachments. The Trojans then drop ransomware into the infiltrated system
- Once dropped, Ryuk uses AES-256 to encrypt files and an RSA public key to encrypt the AES key. Ryuk then attempts to delete all backup files and Volume Shadow, preventing the victim from recovering encrypted files without the decryption key
- Attackers then attempt to shut down or uninstall any security software that could keep the ransomware from running. A RyukReadMe file placed on the infected system provides email through which the victim can contact the attacker. Once the contact is made, the ransom amount is revealed along with the instructions on how to pay
When a ransomware attack is successful, the damage to patient care, IT resources and recovery costs to a healthcare system that is already strained by COVID-19 could be devastating.
Defending Against Ransomware Attacks
The Joint Cybersecurity Advisory provides a list of recommendations for organizations to implement to prepare for the new wave of ransomware attacks. If you are not sure where to start, here are a few steps you can take to shore up your defenses:
Ban Weak and Compromised Passwords
Trickbot often attempts to propagate through an environment using lists of common or compromised passwords. To guard against these types of attacks, you need to ban compromised passwords from being used in your environment. You can do so by using a password deny list which should include a list of commonly used and stolen passwords. Some people build their own password deny lists using leaked passwords from previous breaches. Others simply use a Breached Password Protection service that is continuously updated.
Enforce Stronger Password Policies
To further mitigate risks, the Joint Cybersecurity Advisory urges healthcare organizations to “regularly change passwords to network systems and accounts and avoid reusing passwords for different accounts.” However, keep in mind that enforcing periodic password expiration can have a negative effect as it encourages users to take shortcuts, such as incrementing a number at the end of their password, or recycling a previous password. Instead of requiring all users to change their passwords at the same interval, length-based aging allows more granular control by forcing expiry less frequently for users who create stronger passwords.
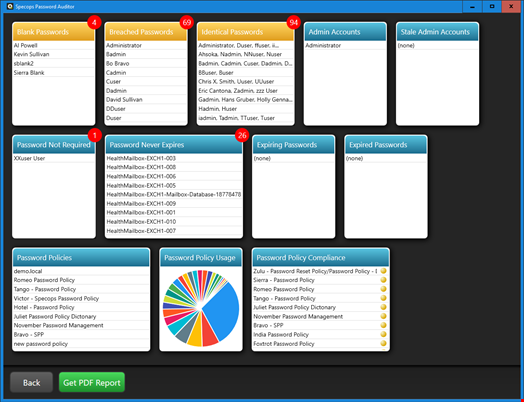
To find out how many passwords are reused for different accounts in your Active Directory, you can run a scan using this free password auditing tool. With a quick scan, the tool detects accounts using identical passwords or compromised passwords, accounts that are expiring soon or have expired, accounts that don’t require passwords and other vulnerabilities. The tool also provides a full view of the administrator accounts in an organization’s domain, including stale admin accounts. This helps organizations follow the recommendation from the advisory to audit user accounts with administrative privileges.
Implement Multi-Factor Authentication (MFA)
MFA is effective in defending against various forms of cyber-attacks because it decreases reliance on passwords. Even if a password is strong and is not a leaked password easily available to attackers, enforcing MFA – for privileged users at a minimum – can provide additional protection.
MFA requires the user to verify their identity with multiple forms of authentication, which could include one-time-passcode (OTP) apps (e.g. Microsoft Authenticator), federated authentication via third party identity providers (e.g. Google), as well as higher trust methods (e.g. biometric authentication). This layered approach fortifies your organization against various types of attacks during a user login or a password reset attempt.
Provide Employee Cybersecurity Training
Ransomware typically targets end users with phishing emails that contain malware-laced attachments to gain initial access to the victim’s network. As hackers continue to exploit interest in COVID-19, there has been a 667% increase in phishing attacks. Besides blocking the email before it can be delivered, it is important to provide security awareness training programs that help users identify threats such as phishing and social engineering attempts, as well as the steps to take when something seems suspicious. The program should be completed by all new employees, and followed-up with updated training on a regular basis.
Don’t Let Your Guard Down
It is important to understand that cyber-attacks are inevitable because nefarious agents are always finding new ways to exploit vulnerabilities. Strong password policies along with MFA can significantly improve security. By combining technical controls with employee training, your organization will stay steps ahead of cyber-criminals.

