In the old days, identity and access management (IAM) was a mainly internal affair, with employees accessing applications safely behind a firewall. OK, perhaps there was the odd remote user, but they tunneled in using a VPN and, for all intents and purposes, they were brought inside the firewall. Those days are long gone.
Today the applications can be anywhere and the users can come from anywhere. Quocirca research (Masters of Machines II, June 2015) shows almost 75% of organizations are now using cloud-based software-as-a-service (SaaS) applications, with a similar number using infrastructure or platform-as-a-service (IaaS/PaaS) to deploy applications that run in third party data centers. The users, as another recent Quocirca research report shows (Getting to Know You, June 2015), can be anywhere too.
As well as the rise in employees working remotely, applications are now opened up to outsiders. Whether it’s to manage supply chains through sharing applications with partners and suppliers, manage distribution online, or transact directly with consumers, almost all organizations are interacting with external users beyond their firewall.
Furthermore, this is not a small-scale opening up to a discrete set of users; the numbers involved are big. The average European enterprise is dealing with almost a quarter of a million registered external users. For organizations that are dealing with consumers, such as financial services and transport organizations, the numbers are even higher. Dealing with this complete reconfiguration of the way IT applications are managed and accessed has required a re-think of IAM.
The Getting to Know You research shows that only 20% of organizations think their current IAM systems are fit for purpose. IAM covers a range of capabilities including user provisioning, compliance reporting and single-sign-on. There is also an increasing requirement for federated identity management, which is the bringing together of identities from multiple sources and application of a common policy. For the majority, the primary source of identity for employees remains Microsoft Active Directory but this is now supplemented by a range of other sources for external users. These include partner directories, government databases, lists from telco service providers, member lists of professional bodies and, especially when it comes to consumers, social media.
The trouble is that many IAM systems were designed to deal with the old way of doing things. They were often purchased as part of software stack from a vendor like Oracle, CA or IBM. Many organizations are now struggling to adapt these legacy IAM systems for the new use cases. As with any legacy system, wholesale replacement is often impractical if not impossible. The result is that new IAM suppliers are being introduced and integrated with the old.
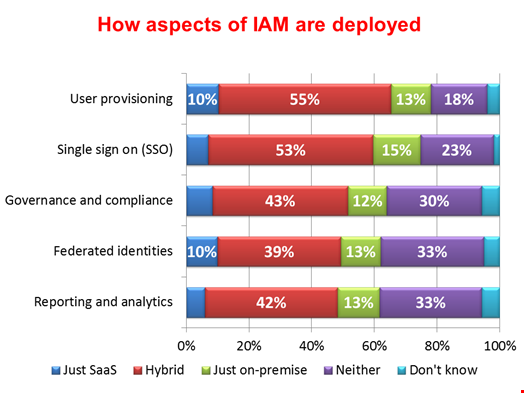
The average organization has at least two IAM suppliers; the number is higher when stack-based IAM is being adapted to deal with external users. The second IAM system is likely to be a SaaS system, designed for provisioning users from a wide range of identity sources to other cloud applications. IAM systems are becoming hybridized: legacy IAM for internal users and some older relationships (such as those with contractors), integrated with cloud-based management for remote workers and users from partners, business customers and consumers. Thirty-nine percent of the respondents to the Getting to Know You research are taking a hybrid approach to federating identities and 53% are doing so for single sign-on, a particularly effective way of handling access to cloud-based resources for internal and external users. Both numbers rise for consumer-facing organizations.
A small number of organizations, around 10%, have moved entirely over to a SaaS-based IAM system such as Ping Identity’s PingOne, Intermedia’s AppID (from its SaaS ID acquisition), Okta, OneLogin or Symplified. Traditional stack-IAM vendors are updating their products; for example, CA SiteMinder, Symantec’s SAM and IBM via its 2014 acquisition of Lighthouse Security. Other cloud service providers, such as Salesforce, have entered the IAM market, in its case by working with the open source provider ForgeRock.
The last decade has seen a revolution in the IAM market. The old guard will attempt to keep up with the up-starts. However, it seems that simply being an incumbent IAM supplier is not enough, so in order to keep up there is likely to be more acquisition and consolidation.