As the exploit market begins to diversify, it has seen the introduction of new threats, the most recent being the inclusion of a relative new comer in TrickLoader and an older threat known as TrickBot. Arbor Networks identified the bot in 2014, with the insights identifying the types of attacks it was capable of.
In 2016 it saw an emergence with code reuse and rebranding as Quantloader thanks in part to the distribution capabilities of multiple Exploit Kits, now including RIG. Using Recorded Future to help us track the recent discussions it has also seen our partners at ForcePoint track the bot as it underwent a brandname change, but continued the use of the code initially used in Madness Bot.
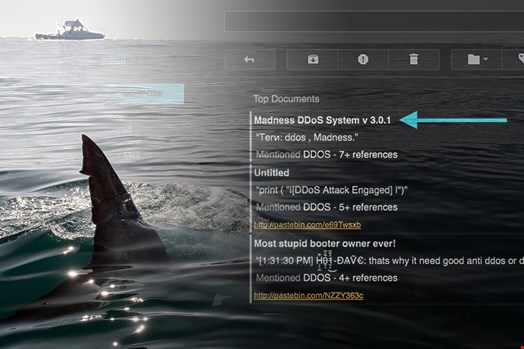
The bot still modifies local firewall rules and uses the netsh command to add additional rules for the bot as well as using CACLS to modify permissions on files.
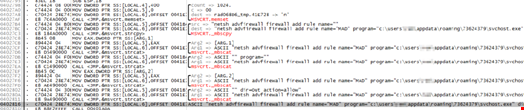
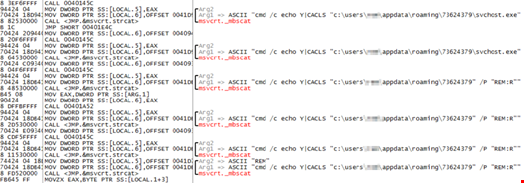
Every business includes unique selling points to ensure a competitive advantage, in this case it’s the delivery via an Exploit Kit, in particular RIG. This was observed by us in the week commencing 28/11/2016 and saw the malware delivered via compromised sites which used the .top domains to help deliver the threat.
In addition to the Quant/Madness delivery, we also observed and mitigated RIG EK drop TrickLoader which saw it’s codebase also lifted from the Dyreza bot which we identified in 2015 using compromised routers in part of the bots TTP’s.
Indicators of Compromise Taken from Emerging Threats
Madness/Quantloader C&C
195.161.62.222
URI
GET / ba/index.php
RIG EK Landing Page
Unspecified.mtw.ru /194.87.238.156
SHA-1: 4b8ac2ae5ae8a4fff43b88893ee202ffc4c5ac16
Indicators of Compromise: Trickloader
RIG Page(s)
70.39.115.202
hxxp://um8ycv.v9rg6k.top/
Trick URL: 78.47.139.102
Possible Dyreza SSL Cert address (Fake State)
207.35.75.110
SHA-1: abeb1660ddda663d0495a5d214e2f6a9fac6cb80
How to Defend?
In today’s threat landscape, organizations can no longer afford to be complacent when it comes to security. It needs to be top of the boardroom agenda. By implementing an effective security education program alongside a strong threat intelligence system and incident response plan, an organization can combat today’s cyber-criminal networks and protect their data assets.
Read more about Fujitsu’s ‘Secure Thinking’ offerings here.
