As DDoS attacks grow in prevalence and size, Dan Raywood explores whether protection is keeping pace with a threat that has already trapped some of the biggest targets across the globe
The distributed denial of service (DDoS) attack is a modern capability to silence an opponent. If that opponent is a government, a business, a journalist or even a rival, the provision is there to stop the other entity from existing, even just for a short while.
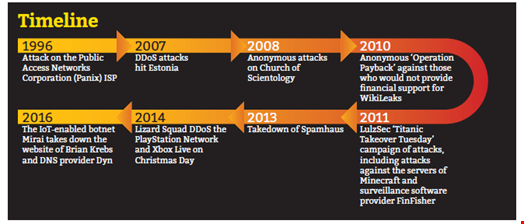
From the beginnings of DDoS, with the 1996 attack on the Public Access Networks Corporation (Panix) ISP, the 2007 DDoS attacks that hit Estonia and the Anonymous campaigns against those who would not provide financial support to Julian Assange and WikiLeaks, DDoS is a weapon of choice for the modern activist who chooses to silence those who do not support the same cause.
For some time, the DDoS attack was about megabytes of traffic. The turning point was the attack on Spamhaus in 2013, which reportedly measured 300 Gbps. Described as the “attack that almost broke the internet” by CloudFlare, it changed the face of DDoS to what we know now in terms of size and capability. Now, according to Akamai’s Fourth Quarter, 2016 State of the Internet Report, attacks greater than 100 Gbps increased 140% year-on-year from Q4 2015.
It also reported that the largest DDoS attack in Q4 2016, which peaked at 517 Gbps, came from Spike, a traditional botnet that has been around for more than two years. Add to this the attack on DNS provider Dyn in September that was measured at 1.2 Tbps, and the attack a day earlier on the website of security journalist Brian Krebs which was measured at 620 Gbps.
Putting aside the Spamhaus attack, which was an anomaly for its time, the sudden rise in size of DDoS attacks has come as a surprise. Krebs claimed that the attack that took his website offline was “according to Akamai, nearly double the size of the largest attack they’d seen previously, and was among the biggest assaults the internet has ever witnessed.”
In the case of the attack on Dyn, this was a Name Server DDoS attack, where attackers focused on name servers to prevent web addresses from resolving. According to Igal Zeifman, security evangelist at Imperva for the Incapsula product line, this is accomplished by using DNS floods against servers, or by attacking the network infrastructure of DNS service providers. He claims that the “significant increase in attack sizes over the past 18 months” has seen them swell to half a terabit per second.
Are We Keeping Up?
If attacks have suddenly increased, is the protection keeping pace? Neustar’s Barrett Lyon, who previously founded ‘always-on’ DDoS protection vendor Prolexic, says the problem is not with technology, as that generally remains the same, but more about how high you can push the defenses.
Speaking to Infosecurity, Sean Newman, director of product management for Corero Network Security, explains that DDoS has been driven by amplification attacks from when attackers realized that they could abuse the protocols that make the internet work, and turn a small amount of traffic into a large amount of traffic.
“Apart from Mirai, pretty much all of the big attacks have been driven by amplification and reflection techniques, which were using and abusing protocols like DNS, or NTP”, he says.
Newman said that DDoS attacks abusing network time protocol (NTP) can deliver an attack up to 1000-times of the traffic being sent to the target, if the attacker can find an open server with that sort of capability. “We still see DNS get used and it is a 50+ multiplier, but nothing like with NTP.”
Asked whether he feels there has been a sudden increase in the size of attacks and if the capability has always been there, he says he is not convinced that there has been an increase in capacity, but just that DDoS “came back into fashion.
“Over time bandwidth has gone up so you need more power for the attack in the first place,” he argues. “Go back 20 years and computers were much less powerful, so it would be hard to generate enough power.”
“DDoS attacks are more frequent and more damaging each year”
Protection is Key
Claudio Neiva, Gartner security and privacy research director, says that “DDoS attacks are more frequent and more damaging each year” and protecting against these attacks, without breaking the budget, is critical to your website's performance and reliability.
Pointing out that an average attack can range from four to 10 Gbps, and last anything from 15 minutes to a whole day, Neiva adds that if the attacker is making a political point the attack can be more sustained. In terms of protection, it’s important to think about what makes sense to be protected in your environment. “Prices can go from $2500 a month, or $14,000 a month, but it depends on the size of your bandwidth.”
In the case of a volumetric attack, Neiva explains that the attacker is intending to fill up ‘your internet pipe’; this will mean that you cannot use your intrusion prevention technology or firewall, or even a dedicated anti-DDoS appliance “as the attack comes from the outside and there is no way to control it.” A scrubbing center can offer a lot of bandwidth while a dedicated appliance comes as a service.
The second option is an ‘always on’ technology, where you do not have to call the provider to redirect the traffic as it will pass through the service center all of the time. The drawback here is that it does cost a lot more.
“On demand means that you need a good communication plan to find out who is responsible for making the call to either do a redirection with the push of a button or a call”, Neiva said. This is enabled by either redirecting through DNS, or via a BGP routing protocol, but you need Slash24 on the website.
BGP helps with routing the internet, Neiva explains, but like Slash24, it allows you to own the IP address independent of the ISP, and it is possible to redirect traffic to another place.
However, the biggest failing, Neiva adds, is when people struggle to decide when to redirect traffic and often wait until it is too late, so it is important to plan which is the best way.
Another option is to use your ISP who could offer a ‘clean pipe’ service, a premium service with specialty scrubbing services dedicated to DDoS. However, contracts are often for minutes, and a certain number of mitigations and attacks cannot be higher than 100 Gbps. “I don’t like the idea of negotiating a contact linked to the size of the attack as you don’t have the ability to negotiate with the attacker”, says Neiva.
The Best Option
Neiva recommends a combination of a dedicated on-premise DDoS appliance and a cloud-based service as it will not always be a volumetric attack, but many will be based on floods and are not filling up the pipe, but can be noisy enough to stop your IPS from working.
Garry Sidaway, SVP security strategy and alliance at NTT Security, says that most businesses are failing to realize the potential impact of DDoS attacks, which is why they are not budgeting for them or implementing the right controls and response plans to stop them.
“Recent high-profile incidents like the attacks on US company Dyn and [Brian] Krebs, will help push it up the corporate security agenda,” he says. “Yet increasingly these will be driven by extortion, with ransom-based attacks becoming more common and companies prepared to pay off cyber-criminals to avoid customer attrition and financial loss.”
According to Maxine Holt, principal analyst at the Information Security Forum, the key is preparation, and to include DDoS attacks when profiling threats to your organization, implementing the necessary level of protection. “Organize your infrastructure so that critical services are separated. This means that DDoS attacks shouldn’t affect other critical services.”
Preparation and having the right technology fit for your business is one thing, but ensuring it works is another. Eoin Keary, founder and CEO of cloud-based MSSP Edgescan, says he has found that many DDoS protection services are broken and not tested frequently enough.
Keary adds that despite spikes in traffic at unusual times, organizations do not see them and are often not aware it is going on until someone complains. “Often the DDoS protection kicks in too late, as if it kicks in at 300 Mbps, the servers are out of business when you get to 100 Mbps.”
The need for protection “can be less or more depending on what it is protecting”, Keary explains, and from the companies he has worked with, three out of five have DDoS protection, but only one in those three have it working.
Where there is no DDoS protection, Keary points out that many organizations rely on their ISP, but it is increasingly hard to block as the source of the attack is a moving target.
DDoS prevention is not an under-served part of the industry, and as has been uncovered in this article, there are plentiful options to protect yourself. However, as the size of attacks normalizes at a high level and protection services remain expensive and untested (meaning that businesses are unaware of when things are going awry) maybe the information security industry needs a better solution.
With a 20-year history, and 17 years between the attacks on Panix and Spamhaus which both involved email filtering targets, DDoS has rapidy matured and as the attacks on Dyn and Krebs showed, anyone can be a victim, and if you are the chosen target, even the best protection may not save you if you are unprepared.