



‘Social engineering’ means the application of psychological manipulation to change the behaviour of a particular target – in other words, what the con artist does online to help them steal.
Overt social engineering
“The depersonalised nature of internet communications in general is exploited by crooks aiming for a short con: small pay-offs, but lots of them, using and re-using tried-and-tested techniques based on social engineering”, says David Harley, ESET research fellow and director of malware intelligence.
The initial approach will involve a plausible story to gain your trust, but will often include an element of panic to persuade you to act quickly. The story itself will appeal to one of the basic human instincts. It will offer you money for nothing (greed); it will solicit humanitarian aid either for a friend in trouble or a suffering population (sympathy); or it will be threatening to persuade you to pay up or face the consequences (fear).
Current simple overt attacks include:
- Advance fee fraud – You pay a little now to get a lot more later, which never materialises. Examples include Nigerian frauds and foreign lottery wins
- Auction fraud – You bid for a bargain, pay the money, but never get the goods
- Counterfeit goods – Most commonly expensive watches and Viagra
- Disaster appeals – Fake requests follow all natural disasters
- Extortion – Pay up or suffer the consequences
- Financial fraud – Typical scams include Ponzi and pump-and-dump schemes
- Londoning – I’ve been mugged in London/Lagos/Belgrade: please send me the air fare home.
- Money laundering – You’re offered a job as a shipping or finance agent for a foreign company. You end up shipping stolen goods (cyber mule) or stolen money (money mule) abroad
Complex covert social engineering
Covert social engineering attacks do not openly ask for money; their purpose is to unknowingly steal your financial details. The principles remain the same: a plausible story to gain trust, followed by an appeal to basic emotions. The most common attack vectors are phishing, drive-by malware, false codecs and rogue software.
“Indiscriminate phishing”, explains Harley, “where deceptive emails are spammed/mass-mailed in the hope of tricking a percentage of users of the phished service into divulging sensitive data, usually exemplifies the re-use of malicious resources to attack high volumes of potential victims. Use of techniques [such] as dynamic DNS and bot herding”, he adds, “is intended to make it harder to track and close down malicious or compromised machines hosting those resources.”
| "In general, the user is easy to fool – and that’s why so many people get infected. Even if you know about security, and you know you have to be careful on the internet, no-one is safe when something is really targetted at you" |
| Luis Corrons, PandaLabs |
The social engineering aspect of drive-by downloading includes persuading people to visit a particular site that hackers have ‘poisoned’. They have compromised the web page with their own malware that infects the computer, via the browser, of any visitor to the infected page. This malware will then open a covert channel to the attacker who can subsequently install more sophisticated malware, likely to be spyware, a keylogger, a rootkit capable of turning your machine into a botnet zombie, or a combination of all three.
A more subtle variation uses the technique known as ‘search engine poisoning’. This will likely involve a specially crafted website that contains malware. As soon as an incident of international interest occurs, the attackers use search engine optimisation techniques to make this website appear high on search engine returns.
So, if there’s an earthquake or plane crash – or an ash cloud that gets your interest – use caution when searching in Google, Bing or Yahoo; there may be false links to a bad website. Having said this, search engines are typically very good at recognising this attack and removing the links.
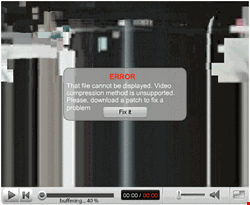
Another attack style includes the false codec. Pornography is the most common lure – but anything that has video content works. Nigel Hawthorn, vice president of EMEA marketing at Blue Coat, explains: “One of the ‘old standby’ malware vectors has recently added a bit of extra bling to increase its believability”, he says. “I’m referring to what I call ‘fake codec’ malware – a web page that presents you with what looks like a video player window, but then tells you that your computer needs a new video codec (or a Flash upgrade, or a new version of Windows Media Player, or whatever) in order to view the video.
| "Social networks are just magic for the bad guys. You’re out there giving the con man everything he needs to be able to con you" |
| Dave Marcus, McAfee |
Since the typical victim is in hot pursuit of a supposed pornographic video clip, the bad guys are counting on them not taking too long to think about the setup. But a little extra bling never hurts, so the latest version actually has some random ‘scrambled video’ bits flashing through the window for a second or two before it announces that you need a software upgrade to see the porn.”
Whether you get to see the video becomes irrelevant. What you do get is infected.
Rogue software is almost always fake anti-virus software. You are offered a free scan that will ‘locate’ fictitious malware on your computer. You may then be offered the full anti-virus package for just a few pounds – and, of course, your credit card details. Or you could be offered a free ‘repair’ tool, which may or may not fix the supposed infection but will also include hidden malware.
Targetted social engineering
Carl Leonard, Websense security research manager, EMEA, has published details of a social engineering attack current as this issue goes to press – a mass spamming email specifically aimed at human resource staff with an attached résumé and the request: “Please review my CV”.
The CV is disguised as a zip file and contains the Oficia bot. This in turn downloads and installs the rogue AV package known as Security Essentials 2010. “HR departments are used to receiving CVs over email, and this kind of malicious activity is indicative of the modern-day hacker”, Leonard says. “The broad-brush approach to seeding malware is now out of favour; fraudsters know they can infect more computers, and steal more data, if they use techniques that fit the target.”
These attacks show the beginning of a move away from undiscriminating mass malicious spam to a more targetted and direct form of social engineering. The key that unlocks targetted attacks is Web 2.0 in general, and social networking in particular. “Social networks are just magic for the bad guys”, says David Marcus, director of security research and communications at McAfee. “You’re out there giving the con man everything he needs to be able to con you.”
Graham Cluley, senior technology consultant with Sophos, also had some points to interject. “Take LinkedIn. One of the things you can do is get a company profile. This is effectively a corporate directory of that company – a list of everybody on LinkedIn that works for that company, with job title, and even those who have just joined the company.
“It is easy for a hacker to forge an email that appears to come from the head of HR to all new employees saying, ‘Welcome, congrats on joining our company. Click on this link to our company intranet and find out about all the wonderful advantages and opportunities’”. It would, of course, be a false website containing drive-by malware.
McAfee’s Marcus highlights opportunities for the con artist on Twitter. “People tag words in their tweets to say this is a subject I’m talking about”, and Twitter itself tells you the most popular subjects at any point. “There are 75 million people tweeting [about a particular subject] which is a magnificent piece of information for a social engineer, who can then send out into the ‘twittersphere’ a tweet tagged with the same subject and a shortened link. You can guarantee that many people who are following that word will click that link.”
| "The depersonalised nature of internet communications in general is, at the moment, most exploited by crooks aiming for a short con" |
| David Harley, ESET |
Facebook has been a scammers’ phishing pool for some time. Ed Rowley, product Manager at M86 Security, gives an example: “A Facebook scam originating from the Pushdo botnet in October 2009 showed two aims – to steal users’ Facebook account credentials and to distribute the Zbot (Zeus Bot) Trojan. This particular phishing scam diverts the user to the fake Facebook login page, allowing cybercriminals to phish the person’s Facebook account (first hit). Then, to add insult to injury, the user is taken to a page that informs them that they need to download the ‘Facebook update tool’, which is the Zbot trojan (second hit).”
But this is just the beginning. The full details of the attack against Google earlier this year are still unknown; but it is believed that the attackers researched the targets on social networks before sending them forged emails.
That can be done by just about anyone: you find the right target within the right company on LinkedIn, and then you learn about their personal interests on Facebook. “The weak link in this is always the user”, says Luis Corrons, technical director at PandaLabs, “and in general the user is easy to fool – that’s why so many people get infected. Even if you know about security, and you know you have to be careful on the internet, no-one is safe when something is really targetting you.”
Defending against social engineering
“The best definition of social engineering is hacking the human brain”, says Marcus. “In a thousand years’ time”, adds Cluley, “we will still have social engineering attacks – they might be delivered by 3D holograms, but they will still be social engineering because we cannot upgrade and patch human brains”. The problem is that social engineering is not a technology problem, so it has no absolute technology solution.
“Education, education, education”, says Marcus. He doesn’t want people to be paranoid but believes that ‘suspicion’ should be the keyword to everything we do on the internet. “You cannot effectively get off the grid anymore”, he warns. “Your information is out there, and if you’re telling people about your interests on social networks, you’re inviting the bad guys to lure you with more than everything they need to be successful.”
Harley advocates using your own social engineering techniques: change users’ bad habits into good habits by “countering malicious social engineering with constructive social engineering through education”.
But in the final analysis we need to remember the concerns put forth by Panda’s Luis Corrons: “I’m not really optimistic – there is no way to be 100% safe – you can be pretty safe, but you cannot guarantee security. OK, you’ve got your anti-virus and it’s up to date, but they will know which anti-virus you’re using and they will test their trojan against your anti-virus to see if it is detected before they attack you with it. They will have studied your movements and know your weak points.”