In the past couple of weeks, we have seen more news reports about ransomware hits, but with an alleged new twist – the ransom was reportedly paid.
Traditionally, industry advice has been to warn against paying an attacker’s ransom, as by doing so you’re funding future crime, both on and offline. However, as evidenced in some recent news, both Garmin and Blackbaud have reportedly paid a ransom of around $10m to attackers after being hit by suspected ransomware – although, at the time of writing, neither company has officially confirmed if this is indeed the case.
Nonetheless, the reports have resulted in the debate about whether or not to pay a ransom being re-opened. In a recent Twitter poll, Infosecurity asked Twitter users: Is it ever acceptable to pay the ransom if you are hit by ransomware? The results were not as conclusive as one may have expected, with 47.8% said no, whilst 26.8% said yes and 25.4% opting for “it depends.”
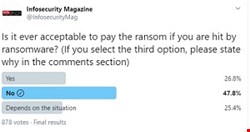
The “it depends” answers revolved around the issue of backups, with some respondents arguing that, if an organization/user has a retention-based offsite backup, then paying the ransom should be avoided. However, if that is not the case and it is essential that the data is retrieved, the consensus was that paying the ransom may be the only option open to the victim(s).
As part of a recent webinar hosted by HP and moderated by Ed Amoroso, founder and CEO of TAG Cyber, Infosecurity asked the question of whether it was ever appropriate to pay a ransom. Charles Blauner, partner and CISO in residence at Team8, said that this can “encourage bad behavior” as victims can get insurance to cover it, and recoup the money. “It is not encouraging the right behavior and it should be about risk management and not paying risk off,” he said.
Blauner also veered towards the “it depends” option, saying if there is a choice of paying a ransom or declaring bankruptcy, “as a CEO, the responsible thing to your shareholders and employees and customers is to pay the ransom. It is not a healthy place to be where a ransomware attack takes a major corporate entity and brings it to its knees, there has been some failure in the design from a resiliency factor, or something that should have helped mitigate the risk of an attack, and there are smaller entities that are not going to be able to deal with that and are going to be stuck.”
The panel also covered the financial factors in the case of the Baltimore ransomware attack, where “the attackers asked for $76,000 and they said no [to paying] and it ended up costing them $18m to rebuild the network.” Kris Lovejoy, EY global cybersecurity leader and former CISO of IBM, said this is now a factor that insurers are considering, adding “insurers are recommending paying the ransomware, and many of the questions I get are ‘how am I supposed to buy Bitcoin if I need to pay these guys off?’ So I do think rational human decisions based on financial dynamics are being made in coordination with the insurance companies to make this recommendation.”
“Paying the ransom isn’t necessarily going to end your troubles”
In an email to Infosecurity, Ian Pratt, global head of security (personal systems) at HP Inc, acknowledged that high profile ransomware incidents have increased, but this trend predates the COVID-19 pandemic.
“E-crime actors with significant and well-established malware operations including TrickBot, QakBot, Dridex and ransomware-as-a-service gangs have been some of the most active during the pandemic,” he said. “These threat actors are primarily motivated by financial gain and that has not changed. Ransomware attacks have proven to be very lucrative, so it’s highly likely this activity will continue to grow through the second half of 2020.”
He also claimed those demanding ransoms are not the same as those who gained entry, as often there is a whole criminal supply chain of different actors contributing specialist skills – finding vulnerabilities, building exploits or payloads, crafting the lure, distribution, etc. “This means that paying the ransom isn’t necessarily going to end your troubles,” he said. “As criminals play the long game, aiming to extract as much money as possible from a victim, CISOs need to find ways to maintain the integrity of their networks. That starts with the endpoint. These devices are on the front line of every organization.”
He also said that with a mostly remote working employee base now, attacks can become more disruptive and damaging “so you can see why the pay or don’t pay debate has come to the fore” as incident response efforts are slowed down and it can cost more, since it becomes harder for security teams to investigate and do remediation work.
“Most organizations simply don’t have the capability to intervene and reimage machines remotely,” Pratt concluded. “Moreover, most devices aren’t equipped to autonomously recover or defend themselves. Device choices are ultimately security choices – choices that determine your resilience. That’s why we design from the hardware up to ensure business continuity is anchored in the bones of our devices.”
Unfortunately, in these times when budgets are reduced and the resources required to overcome most forms of cyber-attack become even more stretched, we still see more cases of ransoms being paid and whilst it depends on the situation, it may be an easier way out of danger.
