During COVID-19 lockdown, we’ve mostly been forced to change the way we work and live, and, as a result, have become more reliant on online services to fulfil our needs.
Where once we would simply walk or drive to a local supermarket, we may have switched to online orders. Where we would previously have eaten out at a nearby restaurant, now many of us are more reliant on takeaway services and deliveries of beverages. If we were regular exercisers before COVID-19 lockdowns, we have taken to ordering work out equipment for our homes and gardens.
Altogether, our digital footprints probably got a lot larger whilst we were encouraged to stay home and stop the spread of the virus. Therefore, the question is, in the period of the COVID-19 pandemic, have we created more accounts and spread our details wider across the internet?
In a series of recent polls hosted on Twitter, Infosecurity sought to determine the answer to this question. In our first poll, we asked how many new accounts users had created in lockdown.
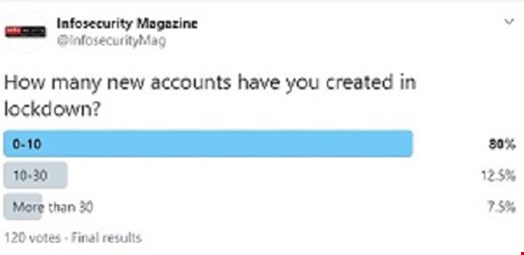
The majority of respondents opted for the first option of zero to 10, and we have to consider that some of that sample would have chosen that option for no new accounts created. In early July, research from Digital Shadows determined there were 15 billion credentials available on cyber-criminal marketplaces.
Asked if it was fair to assume that many people have had to create new accounts for digital services, Kacey Clark, threat researcher at Digital Shadows, told Infosecurity “the limitations of life in a pandemic significantly affect all facets of our lives,” and for many, online shopping and banking has been the norm for years, but it’s a brand new experience for others.
“Many new users are likely unaware of basic online safety methods such as the use of password managers, properly vetting unfamiliar email correspondences and being critical of when and where to enter sensitive information or banking details,” Clark said.
“Without knowing proper methods for setting up unique and complex passwords for each account, it is highly likely that new users are at risk of account takeover and abuse. Password reuse in particular puts people at risk of falling victim to credential stuffing attacks.”
Our second question poll focused on the issues that surround creating a unique and secure password, and asked the straightforward question of whether this is something that is regularly done for every new account.
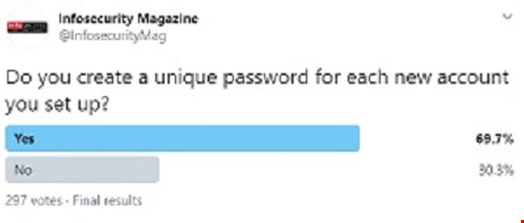
You would presume that everyone who follows Infosecurity on Twitter would vote on the positive side wouldn’t you? Is this indicative of a “throwaway” culture of creating one-off passwords for an account for a single use? Clark said it was “not surprising that a third of the poll respondents did not create a new and unique password for each account” as, depending on the type of account, it is possible that users assessed the potential impact of account takeover and assigned a unique or basic/throwaway password accordingly.
Clark added: “In an ideal world, users should create a unique, complex password for each account, regardless of the potential impact of a compromise.”
In our third poll, we asked followers if they make a habit of regularly deleting old and unused accounts, which play a significant role in the growth of digital footprints.
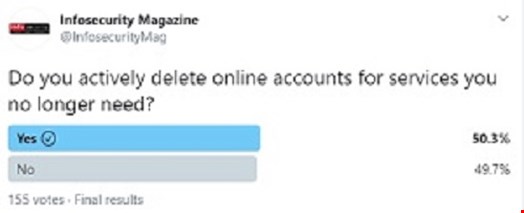
This was the closest result we had of the three polls, and hopefully reminded some of the adage of: what is created online stays online. Infosecurity asked Clark if it comes as any surprise that there are so many credentials available when people create a password for an account, but then leave it unused? They said: “Unused or forgotten accounts can enable account takeover; however, it is not the driving factor. Most account takeover incidents involve weak or repeated passwords across multiple accounts, misconfigured or unsecured back-end infrastructure, and phishing websites.”
However, Clark did go on to say that old or unused accounts can pose a problem, as the more accounts a user has, the larger their attack surface is. “If a user stopped using their email account years ago, and attackers successfully gained access, they can leverage that account to conduct phishing attacks and compromise additional users.”
Clark agreed that while deactivating unused accounts is ideal, it does not appear to be a priority for the average user. While customer data is protected under GDPR, attackers can still carry out successful credential stuffing or brute-force attacks on user accounts; some of the burden remains with the user to use proper password hygiene.
Of course, the debates about password creation and reuse have been going on for years, and the need to replace them with something more secure and user-friendly whilst also practical for deployment and management remains.
One solution proposed is to create a new username/email account for each new account created. While this may seem quite a laborious way to ensure you create secure logins, does that provide better control over your data and ensure you know which accounts are more vulnerable?
Clark said: “In theory, creating a new username/email account for each new account created does provide better control over your data. If one account is compromised, pivoting to other accounts can be more challenging for attackers. Additionally, if you start receiving spam mail on the email address that you used to create only one account, it is easier to identify a potential compromise and where it originated.”
However, the more active accounts a user has, the larger their attack surface is, Clark said, and in principle “this method is likely too time consuming and inconvenient for the average user.”
With the original research showing how widespread the problem of breached credentials can be, hopefully our own polls have shown some of the reasons why this happens. If even the most informed practitioners in our industry do not manage their password creation and digital footprint, how can the general public be expected to follow?
For further discussion on these results, listen to the latest edition of IntoSecurity, the Infosecurity podcast, available to listen here.
