
How big can Bitcoin get? That’s the question asked by many right now, as the value of a single Bitcoin breaks the $1000 (£612) mark and the bubble keeps expanding. Cyber criminals are amongst those keen to exploit the rise of the virtual currency.
It’s no surprise then that November saw some epic Bitcoin heists. Bitcoin Internet Payment Services (BIPS), a Denmark-based organization, said it was hit by a massive distributed denial of service (DDoS) attack before its systems were compromised and 1,295 BTC stolen, now worth well over $1 million. Two other exchanges, inputs.io and GBL, have reported losses amounting to millions of dollars of Bitcoin each.
Individuals have been hit hard over the years too. Back in June 2011, one user, an early adopter known as ‘allinvain’, claimed they had been robbed of 25,000 BTC. More have continued to suffer. Many say Bitcoin provides anonymity, as transactions are done using cryptographic public and private keys. But it’s clear that like any currency, it can be stolen and without too much difficulty.
Where Demand is Strong, So is Supply
As with almost every digital crime, many Bitcoin thefts, especially at the individual level, are being powered by tools selling like mad on the many dark web marketplaces. On my trips around the underground forums, and from what my contacts working them say, it’s clear the demand for this kind of malware is strong. Supply is solid too. Yet the cost is startlingly low. Indeed, many are just being handed for free as simple GUI tools.
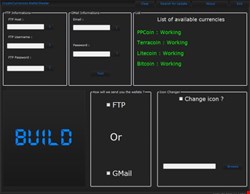
They are fairly crude things, from what can be gleaned from the forum posts and GUI images posted by the dealers, two of which you can see in image 1 and image 2. They traditionally steal the wallet.dat file from any system infected with the concomitant malware. Some say they work on all Windows systems. Most claim to avoid all anti-virus systems.
Many appear to be written in C++ and require the user run an FTP server and actually get malware on people’s computers, usually done with some basic social engineering. The front end build only requires the user to add their FTP or email details, depending on where they want the Bitcoin wallet to be delivered.
There are two “flavours” of Bitcoin Stealer, according to one source operating on the forums. They are either standalone software, or are “modularised” and integrated with existing malware, like prevalent banking Trojan Zeus.
$600 Buys You a Bitcoin Miner
Whilst Bitcoin stealers are either super cheap or free, Bitcoin miners are selling for significant sums. That’s largely because of their complexity. One spotted by my source was selling for $600 a copy, or around 0.6 Bitcoin now, providing an x86 rootkit capability to hide from detection systems and a custom version of the BFGMiner, a regularly updated and legitimate mining tool. Only five copies were on offer, providing the full source code of the miner bot.
That miner is injected into a target system’s memory. Once that’s done, the hacker can monitor and alter the bot’s operations via a control panel. They also have the ability to “set the intensity of the GPU mining threads”, according to the seller’s post. It works alongside other miners, illegally installed on unsuspecting user machines, creating an HTTP-based botnet, as they seek to solve the tricky mathematical problems needed to unlock new Bitcoins together, sucking up victims’ compute power.
Miners have been growing in prevalence for some time. Earlier this year, F-Secure reported the perennially pesky Zero Access botnet was mining to the tune of $2 million a month. That will be a far higher figure now. Such success is making investment in miner add-ons for botnets or dedicated bots far more interesting for dark web crooks.
Branson Accepts Bitcoin
All of this activity on the underground is being fuelled by mainstream acceptance of the crypto-currency. Sir Richard Branson and his Virgin Galactic operation to send people into space is now accepting Bitcoin. Meanwhile, a US Senate committee exploring the potential and risk from Bitcoin heard from the FBI that virtual currencies offered “legitimate financial services”.
Dark web sellers are upping their adoption of the currency too, since the demise of Liberty Reserve. “If in the beginning it was mainly web currencies such as Perfect Money, we are now seeing more and more vendors accept Bitcoin too”, a source told me. The ransomware Cryptolocker even had to reduce its ransom fee down from 2 BTC to 0.5 BTC thanks to the growing value of Bitcoin.
Silk Road has also returned, helping blow up the Bitcoin bubble even more. There have been few interesting posts from an infosec perspective over the last month. In the digital goods section, far smaller than the narcotics section, I’ve spied a number of bot offerings, largely focused on social media. Amidst the rafts of porn and, bizarrely, all series of Seinfeld, are some Facebook like and Twitter follower botnets, and little else. But Silk Road was never a hub for digital criminals anyway, and that doesn’t look likely to change.
Regardless, as Bitcoin sees a boom in terms of value, the illegal market for finding ways to exploit it is kicking off in a big way too.