The Media Trust has discovered a recent malvertising campaign involving Apple Pay that is part of a large-scale phishing and redirect campaign targeting iPhone users visiting premium newspapers and magazines.
In today’s blog post, Michael Bittner, digital security and operations manager at The Media Trust wrote that the campaign was discovered when the security team helped “a winner of several Pulitzer Prizes and one of the largest daily newspapers in the West Coast, thwart a large-scale phishing and redirect campaign targeting iPhone users visiting premium newspapers and magazines.”
Disguised as a legitimate ad, the malware, dubbed PayLeak, delivers those newspaper or magazine visitors who click on the ad to a malicious domain registered in China. Upon arriving, the malware then checks to see whether the visitor’s device is in motion or at rest, upright or lying down and whether it is an Android or iPhone. In addition to determining whether the browser platform in use is Linux x86_64, Win32 or MacIntel, the malware also confirms whether there is malware detection technology running on the device.
When those conditions are detected, Android users are redirected to a fraudulent phishing site that falsely claims that they have won an Amazon gift card. The iPhone users, however, receive two successive popups. The first one is an alert that the device itself needs updating, followed by an additional notice that the Apple Pay app needs updating.
The popup messages are highly sophisticated, particularly the Apple Pay credit card information screen, which is convincingly identical in appearance to that of the Apple Pay, where users enter their credit card details.
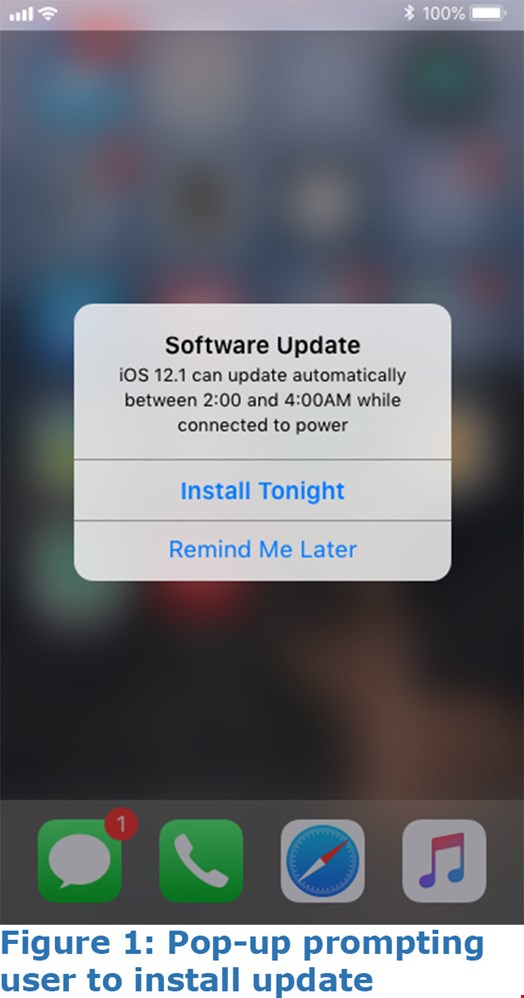
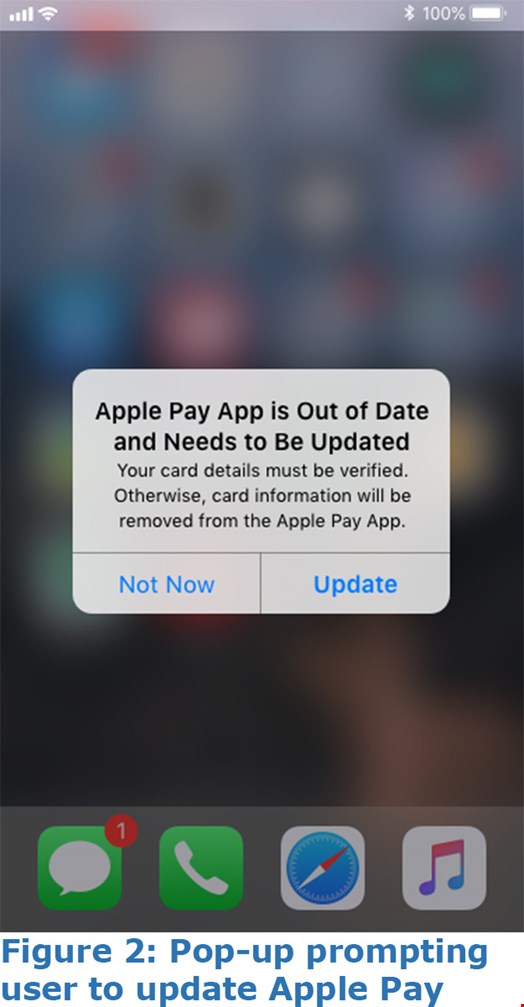
Unsuspecting users then share their credit card information, while the malware logs additional device information, iOS version and IP, then sends that data to a malicious command-and-control server. According to Bittner, this information can potentially be used for a future man-in-the-middle attacks.
“Targeted sites with weaker security measures, such as those that do not monitor their digital environments for unauthorized code, could risk leaking their users’ sensitive information and leave the latter exposed,” Bittner warned.
