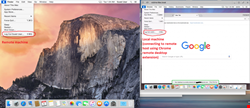
Security analysts at Check Point Research have flagged a bug to Google relating to its Chrome Remote Desktop extension (RDP). The flaw, which affects macOS users and machines, allows a “Guest User” to log-in as Guest and yet receive an active session of another user (such as an administrator) without entering a password.
Chrome Remote Desktop is an extension to the Chrome browser that allows users to remotely access another computer through Chrome browser or a Chromebook. It is fully cross-platform and supports macOS versions from OS X 10.6 (2009) and above, all from the Chrome browser on virtually any device.
The researchers, Ofer Caspi and Benjamin Berger, flagged the bug to Google on February 15 2018. Google responded that from a CRD perspective, the login screen is not a security boundary. However, Caspi and Berger disagree and believe users should be alert.
According to the blog post, on macOS, it is possible to let other people use your Mac temporarily as guest users without adding them as individual users. To exploit the bug, once a Guest user connects to a remote desktop machine, the machine should have at least one active user in session (such as someone logged in and locked the screen/screen saver after x time).
