With human aspects of cybersecurity increasingly recognized as a core part of organizational security management, it is crucial that information security leadership colleagues understand how secure employee behavior is shaped and promoted.
A recent literature review of cybersecurity behaviors in the workplace was created by academics at Royal Holloway, University of London, exploring drivers for cybersecurity behaviors in organizations.
What are workplace cybersecurity behaviors?
Through surveying academic literature, one can classify cybersecurity behaviors within organizations into five broad themes which interact with one another. The first key theme, security culture, acts like an umbrella concept and interrelates with the subsequent four sets of behaviors: inter-personal group dynamics; ‘compliance’ with security policy; communication; phishing/email behavior; and password behavior.
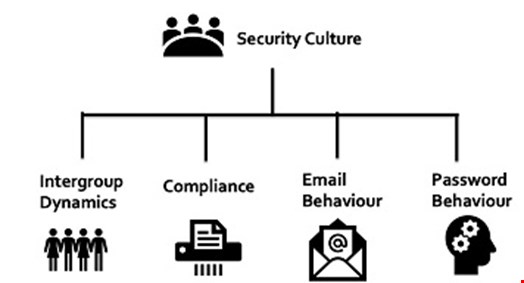
The research paper explores the existing evidence on how each factor influence behaviors around cybersecurity. It highlights areas of consensus (for example, the importance of top-down leadership in improving a security culture) and instances where there is little agreement (for example, whether punishing employees is an effective mechanism behavioral change).
Recommendations for organizations targeting behavioral change include requirements for engaged senior management colleagues, needs-based education and awareness training, and for security policies to take into account employee motivations as well as awareness relating to cybersecurity activities.
What don’t we know? Limitations of current research on cybersecurity behaviors
A major output of the evidence review highlighted how much work there is to do to determine an informed consensus.
There is a lack of agreement across every behavioral theme examined, even on well-recognized workplace practices. For example, there is no academic agreement on whether sanctions operate as an effective disincentive for employee behaviors, nor is there an agreement on the best way to motivate employees to follow a certain set of behavioral patterns (in an environment where many, but not all, researchers argue that scaring the user is counterproductive).
Research is also very limited on how changing regulatory landscapes are relevant to the organization’s approach to security, with regulations such as GDPR raising the stakes when it comes to the cost of security breaches.
Employees are not homogenous and any research that attempts to treat colleagues as a set is limited by its assumptions. An individual’s susceptibility to phishing, for example, has been shown to be linked to their time at the company, their experience level, whether they are aware and motivated by cybersecurity education campaigns.
Attributes such as gender and emotions towards the employer (including loyalty) have also been cited as distinguishing factors (though in the case of gender, published papers contradict each other, with no consensus forthcoming). Furthermore, employees are not likely to act the same within different organizational settings and between industries.
Research projects are often one-off exercises and not repeated which weakens their claims. A key strength to a research finding is its reproducibility; whether another research is able to replicate the findings using techniques from the original experiment.
When it comes to cybersecurity and behavioral change, it appears the area of study is new enough that emerging research is not aiming to replicate previous research. This makes it difficult to build up an evidence base and drives a need for more behavioral change projects looking specifically at cybersecurity.
Opportunities for future research
In order to better understand how to foster behavioral change in cybersecurity workplace practices, experiments must be repeated so their findings can be verified. Not only that, but experiments should be able to shed light on behavioral differences between types of employees or between different organizational environments, adding nuance and depth to research findings.
Valuable research would benefit from bringing together diverse approaches to best understand behaviors and practices, for example drawing insights from psychology, managerial sciences and information security rather than approaching the issue from disparate viewpoints.
Organizations should also consider gathering input from employees to include them in security design processes, moving towards human-centered security solutions that are likely to minimize employee frustrations with misaligned policies. There would be a significant benefit to additional research into needs-based security education training, and the theories behind behavioral change when it comes to cybersecurity.
Above all, greater engagement and reflection on theory and the nature of human behavioral change would be useful to help best design behavioral nudging programs in a workplace.
The full report is open-access and available to download here.
Amy Ertan is a PhD researcher at the Centre for Doctoral Training in Cyber Security at Royal Holloway, University of London. Amy’s research looks at the socio-technical security consequences of emerging technologies. She is a UK-Brazil Data Protection Fellow at ITS Rio, where she researches options for regulating artificial intelligence-enabled technology. Amy is also a CREST registered cyber threat intelligence analyst and has previously worked within the finance industry.
