In April, Infosecurity talked to Shawn Davis, adjunct industry professor at the Department of Information Technology and Management at the Illinois Institute of Technology’s School of Applied Technology, about some research he had conducted regarding what employers are looking for in new applicants.
The full results are available via Shawn’s original blog, but we focused on one particular element which was his findings on “Infosec most needed skills for students.”
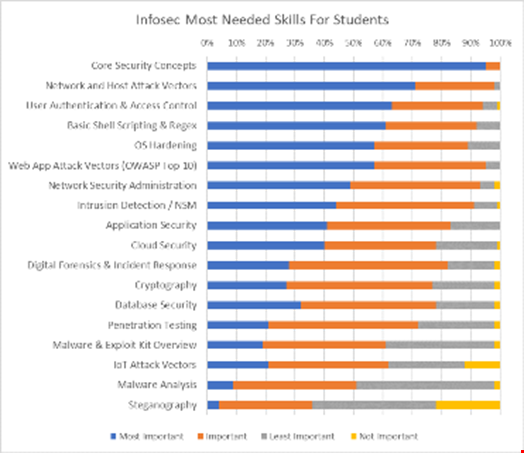
In particular, several skills were deemed “not important” by respondents. These included: steganography, IoT attack vectors and penetration testing. Is this because they are not being taught in schools and candidates would learn in the workplace?
Davis said that at IIT, where he teaches, graduate level courses on steganography and ethical hacking are offered, but a course on IoT Security was not currently offered.
“Many schools do not teach these advanced topics and therefore most employers are not looking for entry-level help in these areas,” he explained. “Depending on the workplace, new hires may eventually learn these skills on the job. Government agencies are most likely to have an interest in steganography, some specialty companies focus on IoT security, and many larger companies have red teams.”
Davis said that sometimes security professionals who work in companies that don't provide these opportunities end up learning them on their own by taking a specialty course.
On the theme of IoT attack vectors, this was one of those deemed not important. Is this because of IoT hype, or because there is no viable evidence of such attacks that it needs to be considered as a key skill?
Davis added that IoT is a real attack vector, as shown by the 2016 internet disruption due to the DDOS attack on DNS provider Dyn by IoT devices infected with the Mirai malware.
“Unfortunately, many manufacturers of IoT devices have not been focused on securing these devices and many companies that buy them don't possess the knowledge to test the devices at the hardware level,” he said. “I feel a greater focus will be put on this area though and research company Gartner last month forecasted worldwide spending on IoT security will increase by 28% over last year and reach $1.5bn by 2018.”
So are we in a time where skills like network admin and steganography are not considered to be as important to the new cybersecurity professional?
He said that many new security professionals start out as analysts and then move on to network security administration, and as a result steganography may not be considered as important at the corporate level.
“This is more of a research area by the government and specialized government contractors looking to detect and reveal covert communications from terrorist organizations or other nation states.”
Finally, only a few percent rated digital forensics and incident response, cryptography, intrusion detection and user authentication as not important, but these are arguably some of the most important factors in cybersecurity today – is there a reason for these even appearing?
He said: “I feel most of these entries only appeared in the survey as ‘not important’ due to industry professionals realizing that most recent hires will learn these skills on the job later as mentioned prior. I am not sure why a few people chose ‘User Authentication & Access Control’ as not being important though as that is a vital skill for new hires.”
Every company has different needs and of those surveyed, there was only a small number who picked these sections of cybersecurity, but perhaps this does prove that there will be the capability to offer training on the job, and applicants need only know those 'core security concepts'.
