In the rush to use technology to counter security threats, organizations often ignore their deep-rooted cultural issues. The Business Model for Information Security (BMIS), which was created by Dr. Laree Kiely and Ms. Terry Benzel at USC and later was acquired by ISACA, is a way of thinking about information security in a holistic way.
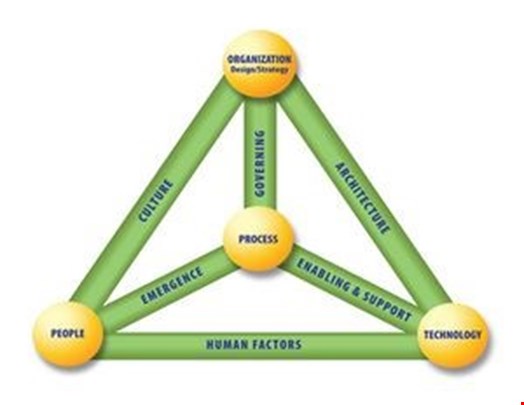
The Culture Dynamic Interconnection between people and their organizations on the BMIS model is one of the most ignored areas in modern cybersecurity, compared with the relatively more mature technology and process areas.
It would help organizations that have culture in their blind spots if third-party organizations offered off-the-shelf culture assessments, which provide insight into the prevailing culture of its teams and leaders as it applies to information security. This would be analogous to organizations inviting a third party to do audits, risk assessments, or penetration-test exercises.
One might think that assessments of the cultural and competence fit of teams and leadership as they apply to cybersecurity are best made internally, ideally as part of performance evaluations. However, someone outside of the organization can assess teams and management personnel more objectively for their cultural fit and their motivation to support the cybersecurity program free of internal prejudices and alliances.
Cultural missteps
Signs of a dysfunctional culture may not show up on normal security assessments, but can have major consequences for a company. A critical patch that takes six months to be applied, resulting in a data breach, might be related to senior management’s earlier criticism of personnel the last time they applied a patch and caused a minor disruption.
A network manager reluctantly following the orders of his powerful superior, i.e., the founder of the company, to falsify disaster recovery test results might indicate a culture reluctant to challenge authority.
Geert Hofstede, a Dutch social psychologist, formulated the concept of “power distance index” to measure the level of deference that lower-level people show to their superiors. Cultures, whether organizations or nationalities, with lower power distances exhibit higher levels of individuality, which means people are more likely to question their superiors and point out mistakes.
Crew resource management (CRM) is an example of an industry’s reaction to culture playing a role in airplane disasters. Jane Ford, Robert Henderson, and David O’Hare found that flight attendants’ attitudes toward safety significantly improved after CRM training.
Before organizations can come up with a version of a CRM-like response to the effect of culture on information security, they need a way to measure it and compare with the industry at large.
Culture Score
Third-party organizations that assess cybersecurity could add one more service to their list of offerings by arranging for qualitative and quantitative assessments of an organization’s culture as it applies to cybersecurity. Chalene Yauch and Harold Steudel compared and contrasted the approaches in their paper entitled Complementary Use of Qualitative and Quantitative Cultural Assessment Methods; further, they recommended a mixed-methods approach of both qualitative and quantitative techniques. Qualitative assessment of culture would take the form of document reviews, participants’ observations, and group interviews.
Further, a quantitative cultural assessment could use something like the organizational culture inventory (OCI) (Cooke & Lafferty, 1987), which is a cultural assessment tool from The Human Synergistics/Center for Applied Research that was designed to provide a snapshot of an organization’s culture by measuring 12 sets of behavioral norms. The primary advantage of the qualitative approach to cultural assessment is the ability to probe for underlying values, beliefs, and assumptions, but it can be time-consuming.
The quantitative (survey) approach offers numerical data that can serve as a culture score, which can form the basis for comparisons between organizations or groups. On the surface, it seems difficult to measure organizational culture, especially for outsiders, but Geert Hofstede et al. (YEAR), in their paper entitled “Measuring Organizational Cultures: A Qualitative and Quantitative Study across Twenty Cases” demonstrated that techniques exist that can at least make a complicated field, such as culture, somewhat accessible.
The unpatched server, the ignored multi-factor authentication recommendation, and the backup and recovery system with a secret all have a story to tell about the missteps made internally that have more to do with culture than process or technology.
Small- to medium-sized organizations typically do not have the resources to invest in the techniques required for the cultural assessment of an organization. A culture score that can be compared with similar organizations with similar sizes in similar industries could be provided as part of a service offered by a third-party entity.
Such a score would provide one more weapon in the information security officer’s arsenal for addressing the cybersecurity challenges within an organization.
