In recent times, there has been a big push by the security and privacy communities to encourage websites to adopt HTTPS. This is certainly a step in the right direction to preserve privacy of sensitive communication and as a result, improve security posture overall.
However, often there are times where we see the industry pushing a message without explaining the caveats. This causes confusion and damage to end-users in spite of them following what they think are recommended best practices.
HTTPS/SSL is a prime example of such phenomenon. We’ve seen over and over again security practitioners recommending people to “look for the green lock” or “look for https” in the browser when opening a link. The caveat often not mentioned is that anyone can create a site with SSL certificate and that it does not guarantee anything about the site’s content.
Someone who doesn’t necessarily understand the nitty gritty of SSL certificates would believe any website with a “green lock” is safe to visit, but this cannot be further from the truth.
We know that there are several free SSL certificate providers like Let’s Encrypt, SSL for Free and Wosign that have made it very easy for anyone to obtain a certificate. Unfortunately, this also includes bad actors who use them to conduct phishing attacks.
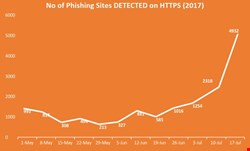
We monitor phishing attacks perpetrated through HTTPS websites and found that nearly 10% of all phishing links are now hosted on such “secure” sites. This trend has been increasing and in the month of July 2017, we saw a large spike in such sites.
These sites are either newly registered and have one of the free SSL certificates, or are hijacked websites with phishing pages injected on them. The takedown of these sites depends on the hosting provider and there are several providers who are prompt in taking down phishing sites within hours of abuse report. Some others do not facilitate takedowns until days after the complaint.
The hijacked pages are slightly tricky to take down as it requires cooperation with the site owner which may or may not be fast enough depending on the owner.
So we have to wonder why such attacks are increasing in volume? The simple reason is because hackers are now seeing a higher success rate for users falling for them. Thanks to the conditioning users have been receiving from publications and security experts, they now fall for phishing via https sites more than ever.
It is clear from the data and trends we see that https sites, in fact, do not mean much in telling whether a site’s content is safe. What it does mean is that the connection between client and server are encrypted and free from eavesdropping. These two are completely different things and should never be mixed together while describing benefits of HTTPS/SSL.
In order to demonstrate this, we created a website that leverages one of the popular phishing techniques that hackers are using nowadays called Homograph attack. The domain xn--gmil-6q5a.com in the browser address bar appears to be gmail.com but if you look closely, you can see that something is off. The domain has unicode characters from a non-English language using an encoding known as Punycode.
Since we created the site, there is no malicious content on there and is safe to visit, but if it were created by a hacker, they would change the content of the site to exact copy of what gmail.com looks like and people would fall for it.
This example demonstrates one of the more sophisticated attacks but in reality, people fall for much simpler phishing attacks as they only look at the “green lock” or “https://” and that combined with a convincing site content is enough to trick them. In our proof-of-concept, registering the domain on GoDaddy, getting SSL certificate from Let’s Encrypt and hosting on AWS took less than five minutes.
As security experts, we are used to evaluating a piece of technology critically and find ways to get around it. We think the same way of thinking can also be applied while recommending something more widely to people.
It is great to bring everyone on board to a good technology but the caveats also need to be clearly communicated in a simple language. It might be easy to give instructions to users in the form of “look for this” or “do that” but that leads to bigger issues if the caveats are removed from user education.

