The SolarWinds breach of 2020 was widely considered the biggest cyber-attack in history. Just three months later, the Microsoft Exchange hack took its place. Both had far-reaching consequences that affected not only SolarWinds and Microsoft, but also their customers, partners, and vendors. The shift toward large-scale hacks on software vendors should serve as a warning to businesses of all sizes: hackers do not need to hack your business directly to breach your business.
Stalking the Supply Chain
Your supply chain is not a secret. From your website to your social media accounts, the inner workings of your business are in the public arena—open to exploitation from cyber-criminals. In 2018, for example, the US Justice Department announced its migration to Office 365 (now Microsoft 365).
The announcement painted the Justice Department in a positive light, ahead of many of its peers in the slow but gradual shift from on-premise, sprawling government infrastructure to the cloud. In public relations, this is called a win. To cyber-criminals who were watching, it was the tip that would help them orchestrate attacks specifically for Microsoft 365.
Similar to press announcements, businesses regularly advertize the names of their customers and partners on their websites, whether in the form of brand logos or case studies. Known as “social proof,” it’s effective marketing. It also unwittingly reveals the supply chain and puts a target on those businesses.
While the SolarWinds hack was a sophisticated operation with, according to some reports, at least 1000 engineers on the payroll, it was likely made possible by a simple mistake: an easily guessable password that hackers used to enter SolarWinds’ environment. If a cyber-criminal is not lucky enough to guess a password, there are other, equally simple ways of infiltrating a business’ IT environment.
Phishing, one of the easiest methods of breaching password credentials, remains a formidable threat, despite significant investments in cybersecurity awareness training. According to the FBI’s most recent IC3 report, reports of phishing doubled in the US in 2020, with more than 240,000 victim claims. While email security solutions have come a long way in developing technology capable of blocking sophisticated phishing attacks, there is a critical flaw in email that gives cyber-criminals the upper hand.
Discovery
A mail exchange (MX) record reveals the email servers a business uses to accept and deliver email. Amazingly, this information is publicly available on the internet and accessible via a simple MX record query. The below image shows an MX query for Home Depot and Au Bon Pain. The redacted text is the domain name of the email security vendor protecting the businesses’ email.
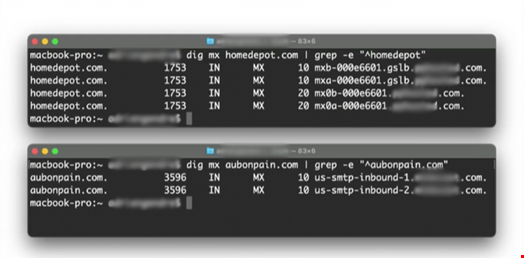
With this information, cyber-criminals can execute phishing and spear phishing campaigns designed to bypass the email security solutions revealed in the MX records. Hackers are familiar with the technologies that stand in their way, and they develop reverse engineering techniques to win the battle against email filters.
The Emergence of Microsoft as a Lucrative Target
Beginning in 2018, Microsoft surpassed PayPal as the most impersonated brand in phishing attacks. The emergence of Microsoft as a phishers’ favorite target coincided with a global shift from consumer to corporate phishing. While hacking a PayPal account ensures a quick and easy payout, hacking a Microsoft 365 account provides long-term opportunities with higher value.
Given the choice between a PayPal account, which might provide a few hours’ worth of spending money, or a Microsoft account, which offers email addresses, contact lists and access to a treasure trove of sensitive files, the choice for cyber-criminals is clear. The Microsoft Exchange hack is further proof that Microsoft is the premier target for supply chain attacks. While the hack hit on-premise Exchange Servers, thanks to a security flaw, Microsoft Exchange Online is not immune.
Microsoft 365 currently has 258 million corporate users, with more than 650,000 businesses in the US alone hosting their most sensitive data in SharePoint, OneDrive, and numerous other Microsoft 365 applications. The platform represents a single target that opens the door to millions of businesses and allows lateral attacks from within, including phishing, spear phishing and malware attacks on a business’s customers and vendors.
The Supply Chain Challenge for MSPs
For MSPs, Microsoft 365 adoption has been a boon, and the COVID-19 pandemic provided a further boost in business opportunities from Microsoft 365. Like SolarWinds, however, MSPs are targeted because of their unique access to the IT environments of a multitude of businesses, including government agencies.
With so many MSPs managing Microsoft 365 for clients, it’s critical that they protect Microsoft 365 with an email security solution that is integrated with Microsoft 365 via API, sitting inside Microsoft’s architecture, rather than on the outside like a gateway or cloud solution. This architectural structure has a number of advantages, including making the solution invisible to hackers in an MX record query and allowing for internal email scanning, which can thwart lateral phishing and ransomware attacks within Microsoft 365.
