In the week when the insider threat reared its head once again with the release of the Panama Papers, a recent webinar aimed to identify the five stages of the insider threat - including what makes a person do it, and what you as a business can do to spot the signs and prevent an incident from occurring.
Hosted by Infosecurity Magazine and sponsored by Infinigate, their senior technical consultant Chris Payne admitted that businesses are still concerned as it has not gone away. “What is more prevalent is that it has always been there too, but it is just that our attention has been shifted to external threats,” he said. “It is just a natural behavior in humans really.”
In the opening poll, 37% of respondents expected that one to 24% of employees openly admit to stealing data when leaving an organization. Payne cited a Symantec survey which found that 50% admitted to having stolen data when moving between jobs, while 56% did not realize that this was a crime; “a statistic that is scary in itself” he said as it is not people that you would expect to do that sort of thing. “It lends itself to teach us that people will need educating around this as people don’t realize what they are doing is wrong.
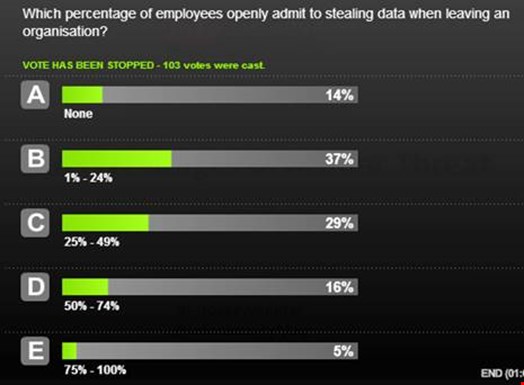
“But also it shows that there is an unhealthy culture in our industry as well if 56% of people don’t realize that this is a problem, as usually the people who are employing them are accepting that stolen data and accepting that they are doing something wrong as well.”
The four types of insider threat were identified as those who are: malicious; accidental; malfunction which takes advantage of something going wrong; and duped users who are being leveraged by a third party.
The webinar identified the five stages of the insider threat, a theme which was explored by all three of the webinar's presenters. Payne began with the tipping point, where employees are not deliberately malicious but where something pushes a person into acting that way.
The second point is recon – where an external attacker would spend time identifying a weakness, while for an insider it can be shorter. This leads to exploitation that depends upon the privilege level, or simply collecting access to carry out the action. The fourth stage is the payload and the actual theft, or a malicious activity such as sabotage, which is something organizations are worried about. The final and fifth is the clean-up stage which can be the determination of attribution.
Payne said that these are the most common stages in an insider threat scenario. Sam Temple, managing director of Jumpsec, said that the typical indicators is that once someone has decided that they are going to commit an act, the typical path that they take is to look at network shares and information they can take, and also dragging files on to USBs and databases they have saved.
Jay Abbott, managing director of JustASC said that a typical insider takes the path of least resistance. “We overlook being security professionals, being technical experts and being people interested in the subject matter is that if you were to forget everything you know and forget everything you think you know and assume the role of the standard user, the easiest way to walk out of an organization is with the access you’ve been granted – you’ve probably already got a high level of access to a lot of information.”
Temple said that a lot of insider threat incidents begin with indicators of compromise, and to be well-placed to respond to an incident you have got to be in a good place to pick these things up. “There is always a possibility of picking up on something before it happens, so looking at the technical indicators of compromise, with a view to insider threat, look at mysterious file redirects or traffic changes or changes to permission structures or behavioral changes,” he said.
“If you can determine what normal looks like, you will be able to better spot an anomaly. If we can pick them up early and act on them at this stage, then an organization can address these problems and do it privately.”
Temple was also keen to point out the benefits of training and security awareness, as people “are your frontline of defence”.
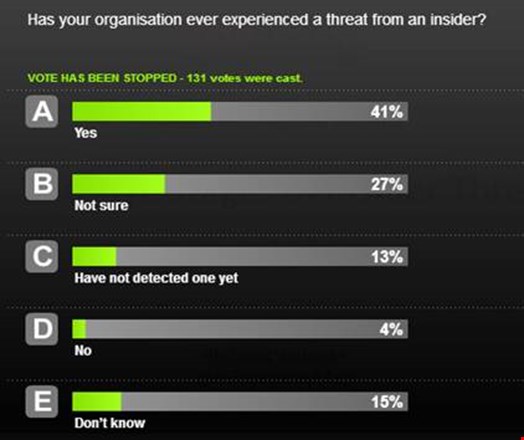
The audience were asked in a second audience poll, and according to 131 votes 41% had experienced a threat from an insider, while 27% admitted to not being sure, while only 4% said no. Payne said that as a topical subject, it is good to talk about this as there is a need to understand the threat more, while Temple said that detection is not straight-forward and often you feel the impact before the incident.
Looking at the concept of the insider threat, Abbott said that this was something invented by the security industry, and the CEO has no comprehension of this as they do not run their business on mis-trust. “I ask everyone listening to search their souls and ask themselves if they didn’t take some documents with them from the last job they left, and I expect very few would honestly say that they did not copy one or two documents that they didn’t consider to be their own intellectual property, or their own investment in time and energy throughout their position. It is such a rife thing to do across any industry.”
Abbott also talked about the benefits of monitoring and detection, as aside from logging everything, being able to detect behavioral changes will help in detecting, as you cannot underestimate how difficult it is to detect patterns. Asked by the audience about monitoring and logging, Abbott said that a disgruntled insider looking to steal data in a company analyzing and spotting anomalies, there is a possibility you could spot a behavioral change. “But you would have to have so many variables lined up in your favor for that to work that it is really playing the odds. It is not impossible, but it takes an awful lot of effort to get to that point.”
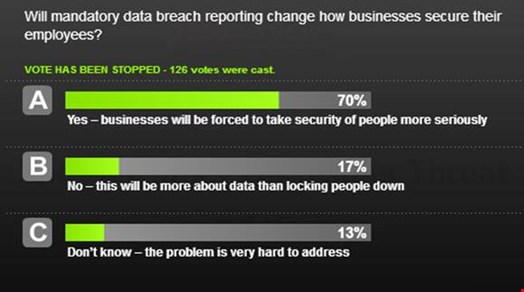
In the final vote, the audience were asked if mandatory data breach reporting will change how businesses secure their employees: in total 70% said they would, 17% said no. Payne said he was glad to see this be the case, as reporting can be lax and in the Panama Papers case, extremely sensitive information was released. “It is a shame that we have to rely on legislation to get organisations to be serious about their data, but the fact that is likely for something to happen is a good thing for everybody, both us as professionals and consumers.”
This live webinar was broadcast on Infosecurity Magazine’s Webinar Channel 7 April, and is now available on demand - https://www.infosecurity-magazine.com/webinars/the-five-stages-of-insider-threat/
About Infinigate:
"Infinigate was founded in 1996 as the first Distributor of internet technology solutions in Europe. Since 2002 Infinigate’s sole focus has been on the distribution of sustainable IT security solutions to protect and defend IT networks, data and applications. As a true Value Added Distributor, Infinigate concentrates on and supports innovative, best of breed security solutions that require a level of expertise and knowledge. Infinigate offers a complete service to its partners and vendors to complement its product portfolio with dedicated technical, marketing, sales and professional services. Following acquisitions in Scandinavia and the UK, the Infinigate Group today has operations in 8 European countries including Germany, France, Switzerland, Austria, Sweden, Norway, Denmark and the United Kingdom. It covers 70% of the Western European IT Market establishing itself as a leading European Value Added Distributor for IT Security. Find out more: www.infinigate.co.uk"

