A long-running malware operation known as SystemBC has been linked to more than 10,000 infected IP addresses worldwide, including systems associated with sensitive government infrastructure.
According to new research by Silent Push, the findings reinforce concerns about the malware's continued use as an early-stage tool in intrusion campaigns that frequently precede ransomware deployment.
First publicly documented in 2019, SystemBC, also known as Coroxy or DroxiDat, is a multi-platform proxy malware that turns compromised systems into SOCKS5 relays. These relays allow threat actors to route malicious traffic through victim machines, masking their own infrastructure while maintaining persistent access to internal networks.
In some cases, SystemBC infections have also been observed deploying additional malware, expanding the scope of compromise.
Silent Push analysts said they began systematically tracking SystemBC activity in 2025 after repeatedly observing its presence ahead of ransomware incidents.
To improve visibility, the team developed a SystemBC-specific tracking fingerprint, enabling the identification of infections and supporting infrastructure at scale. Using this approach, researchers uncovered over 10,000 unique infected IP addresses tied to activity stretching back to 2019.
Read more on botnet infrastructure: Chinese Botnet Bypasses MFA in Microsoft 365 Attacks
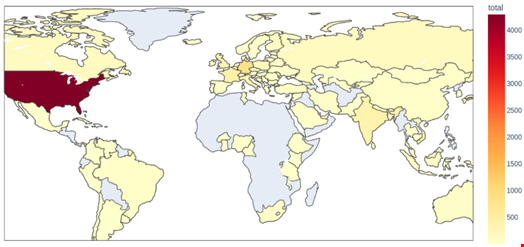
Global Spread and Persistent Threat
The infections were globally distributed, with the highest concentration in the US. Germany, France, Singapore and India followed.
Many of the affected systems were hosted within data centre environments rather than residential networks, a factor that helps explain why infections often persist for weeks or months.
One of the most notable discoveries was a previously undocumented SystemBC variant written in Perl. Designed to target Linux systems, the variant had no detections across 62 antivirus engines at the time of analysis.
The research also revealed that SystemBC command-and-control (C2) infrastructure frequently relies on abuse-tolerant, bulletproof hosting providers, including environments linked to BTHoster and AS213790 (also known as BTCloud).
Within a single hosting cluster, analysts identified more than 10,340 victim IP addresses, with infections lasting an average of 38 days and some persisting for more than 100 days.
The dataset included compromised IP addresses used to host official government websites in Burkina Faso and Vietnam. These systems were not only victims but were also leveraged as part of the proxy network, increasing the potential impact of the compromise.
To defend against similar threats, Silent Push recommended proactive monitoring, warning that SystemBC activity often appears early in intrusion chains and frequently precedes ransomware deployment.
