What happens when you offer up money to anyone who can drive traffic to your website? Hackers, scammers, spammers and fraudsters come to your aid. That’s the case with online movie site zml.com, which offers 30% of each sale and 5% of rebills paid via anonymous means to anyone who refers paying customers to the site. And zml.com is just one of many.
In general, it works like this: a person signs up as an affiliate and is given a code. If someone goes to the website with the proper code embedded in the URL, then a cookie is set and if that person later buys something on the site, the affiliate gets a piece of the transaction. Outside of the shadows this means others are encouraged to setup ads or to refer friends to the site. But on bigger scales, this can be big money, so the established cyber criminal community gets in on the action – not always by breaking the law, but certainly using shady means to drive customers to these websites.
Among the techniques being used by these shadow affiliates are blackhat SEO, fake blogs, spam campaigns and more. These will frequently redirect through servers managed by the shadow affiliate and, in eSoft’s investigations, frequently used for other purposes such as malware distribution and phishing campaigns.
Windows Live Spaces is again being abused with a slew of fake blog pages covering hundreds of popular movies available for download. The download links redirect the user to a number of different movie sites that offer high paying affiliate programs.
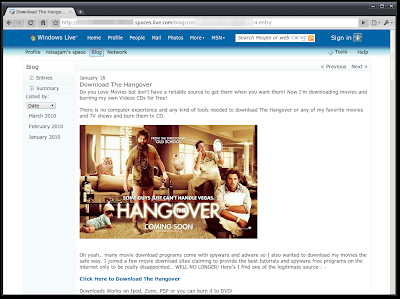
Example 1
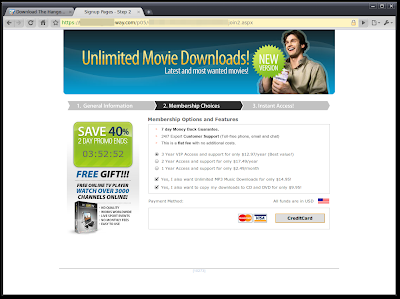
The blockbuster movie The Hangover is the sole blog post in the blog shown above and includes a promo image and full description of the movie with links to download. After a series of redirects to ensure the scammer gets paid, the user is brought to moviedownloads-pro.com. In order to download for free, the user must sign up for a yearly subscription with a credit card and our blog spammer gets a cut.
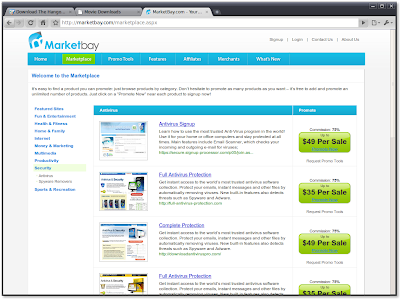
After signing up, the user is emailed a link to download software which we suspect to be questionable although we did not give up our credit card info to find out. The affiliate network in this case is Marketbay, which is also home to some other very shady software including 14 different bogus anti-virus products.
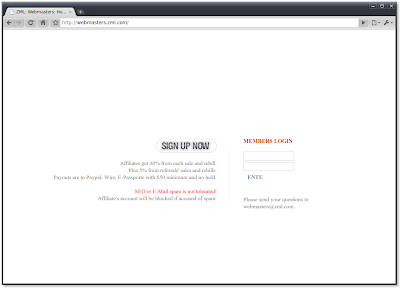
Example 2
In another example, the eSoft Threat Prevention Team found the intermediary sites used by a shadow affiliate were hosted on the same site used in a ring of fraudulent "OEM Software" distribution sites we blogged about last year. These links lead to zml.com, whose affiliate signup page contains the warning, "SEO or E-Mail spam is not tolerated!" However, after sharing information of abuse with zml.com five days before the posting of this blog, we have yet to see the affiliate removed or to receive any response from zml.com. In all likelihood, it is simply more profitable to turn a blind eye.
Using Windows Live Blogs to disguise URLs can be an effective way to get around some Spam and Web filters. eSoft reported on a similar tactic used to push pharma-fraud sites just a few months back. While this is nothing new, it goes to show that cybercriminals will continue these types of campaigns so long as they continue to be effective and profitable.
eSoft currently categorizes a number of these affiliates’ sites as Phishing & Fraud due to their use in Blackhat SEO campaigns and others are categorized as Online Ads or Spammed URLs depending on the methods being used to drive users to the links.