How do we separate the wheat from the chaff or, more properly, determine fitness to deploy? When is a company Enterprise-ready? Does reality match the claim?
Given the continuing hype around ‘cyber’ and the apparent global market opportunity, is it any wonder there are so many startups trying to get attention? There is no question that innovation is required; the proverbial sword-versus-shield cyber ‘arms’ race is self-evident.
If you’ve been to almost any Infosec event in recent years, the explosion of startups bursting onto the scene with their (point) solution to a cyber problem has been very evident. I was fortunate to attend the 2017 RSA Conference in San Francisco, having been to Infosecurity Europe for many years, and was struck by the thousands of vendors, many offering duplicate capabilities, clamoring for customers.
I’ve since interacted with investors, large and small, looking for the so-called unicorn startup and marveled at their willingness to take a punt with very little to go on. There must be a better way to do this.
AJ’s Mature Rating for Cyber Startups
Most recently, I’ve worked with CyLon in London as their CISO-in-Residence, supporting their ninth Cohort of seven startups through the growth program and I am looking forward to doing the same with their tenth Cohort in September 2019.
My role is primarily to provide each startup with a CISO’s perspective on their approach, offering, solution and sales pitch. It was, I think, a mutually beneficial experience as it has given me deeper insight into the challenges and opportunities facing a startup while each company was able to refine their messaging and better understand the perspective of an example client.
Following a side-bar discussion with one of the mentors supporting CyLon, I sketched out this high-level view of a ‘Maturity Rating for Cyber Startups’ to help both them and prospective customers determine where their product might be on the path to being enterprise-ready.
I have primarily focused on the assurance aspects of the features/benefits/risks conundrum as this was a comparatively weak area for many of the startups. This is not levelled as a criticism, more a marker as to their stage of development.
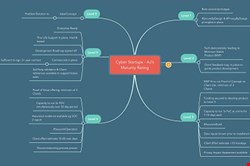
Clearly, other CISOs and prospective customers will have their own requirements and thoughts on the subject. The intent of the model is to guide the startups into thinking about the due diligence associated with a sale that most will have to navigate in some manner before they are able to connect their Minimum Viable Product or Proof-of-Concept into an enterprise environment.
Depending on the client’s need and risk appetite, the decision as to whether to buy into a startup’s product vision will vary and is not just determined by price. Other factors play their part, including, for example, whether the client has worked with startups previously.
What was clear to me was that startups have a clear view of the problem they are trying to solve but not necessarily a solid value proposition that takes into account the client’s own business case to secure funding for any purchase. After all, CISOs usually have to ask someone else in their business for the money; they might need to step through varying procurement and legal processes, and they will have to assign internal resources to enable the project to proceed. The larger the enterprise, the more tortuous and involved this business approval process is likely to be.
Equally, the chances are that larger enterprises have done this before and are perhaps more likely to take a punt with a startup, particularly if the sum involved is comparatively small in the context of their existing cyber spend or if their need is great.
One factor I suggested that many of the startups had not considered was the advantage to a CISO of working with a startup early in their development. By doing so, he or she can influence the product development roadmap to meet their own needs sooner and easier than is possible with a larger or more established vendor with multiple clients. This can be a win-win situation for both and should not be overlooked.
Another factor I found myself emphasizing is the skepticism of the more seasoned CISOs: they have been promised so many silver bullets and have witnessed the hype cycle around Product X, Y & Z first-hand over the years, so the startup needs to be frank about their product’s state of development and should expect to be asked to prove any and all sales claims.
Startups should also be sure to embed the ‘Secure By Design’, ‘Secure In Build’ and ‘Secure In Operation’ principles into their product development from the start. They should consider privacy early on and be prepared for the client to insist on third party validation by penetration testing and other verification means, to ensure that no new risks are introduced into their environments. Essentially, they need to practice what they preach!
There is no doubt in my mind that we need innovation to solve the more intractable challenges facing the cyber defenders. Not all of that innovation should be in the technology arena and it has been encouraging to see more startups addressing the human factors of the people/process/technology triangle.
However, a common challenge for all startups is getting those first few sales to prove their claims. Addressing the need for assurance early is time well-spent, in my view at least.
This is part of a blog series provided by CyLon, who find, grow and invest in the world’s best emerging cyber businesses, via its tailored acceleration programs in London and Singapore. Since 2015 CyLon has supported more than 80 companies and has a portfolio of international companies valued at more than £400m.
