eSoft researchers have been tracking a new campaign by cybercrooks, compromising and creating websites for use in SEO poisoning and malware distribution. Thousands of these sites have been detected that use elaborate techniques to trick search engines and are ready to serve malware in an instant.
At the forefront of this attack is the use of a website referrer, or user-agent, which enables the cybercriminals to effectively increase their search engine ranking while keeping their malicious intentions hidden. Google and other search engine bots will be served up SEO tailored content to manipulate search results and drive traffic. This content cleverly uses a mashup of text and images scraped from various sites.
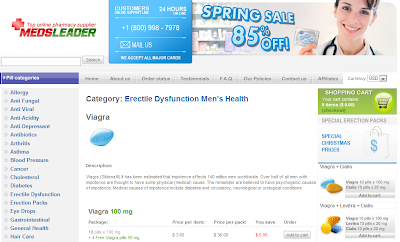
Danger lurks for users that visit these pages using Google search or other search engines. In the course of monitoring, eSoft has seen these pages deliver Rogue AV, redirect to fraudulent pharmacies, fake search pages and more.
At the time of writing, most of the sites involved in the campaign are currently hosting a Red Button flash file, as shown below. This file indicates a compromise. Clicking the red button currently does nothing malicious, but these pages serve as a placeholder for the attackers. These pages change their character depending on how they are referenced, and at any time these pages could infect the user with malware.
The Threat Prevention Team is keeping a close watch on these sites as they continue to multiply. There is a strong chance that these sites are currently establishing good reputations with security companies that will make future attacks through these sites more effective. eSoft is classifying these sites as Compromised to protect SiteFilter users from any future malicious payloads.