Since the COVID-19 pandemic started approximately one year ago, the world has changed dramatically in many ways. In the business community, companies and their IT teams had to adapt quickly to cope with the new challenges and keep their operations moving.
First, there was the transition to enabling remote work. Even organizations that were most resistant to letting employees work from home were forced to fast-track their adoption. In a global survey that Acronis conducted during the summer, the majority of companies (54.7%) reported that their biggest struggle during the pandemic was enabling the remote workers.
The second part of that equation was securing those remote workers because – as expected – cyber-criminals quickly tried to leverage the fear and desire for information about the pandemic for their own benefits. The work collaboration tools companies relied on like Zoom and Microsoft Teams received a lot of attention from researchers and attackers alike. Of the companies surveyed by Acronis, 39% reported they had already experienced videoconferencing attacks, with Canada, the UK and Switzerland topping the list of most affected countries.
Many of the challenges facing organizations in the wake of the pandemic will remain long after this coronavirus outbreak is brought under control. So what can we learn from the changes made to address IT risks during 2020 that help us understand what organizations need to tackle in the coming year?
Based on the trends and data we’ve collected at our global network of Acronis Cyber Protection Operation Centers, here are three predictions of IT risks that we believe organizations will face in 2021.
1. Attacks Against Remote Workers and Exposed Services Will Continue
We have to acknowledge that attacks against employees working from home will continue to be elevated in the future. The interest in collaboration tools is still elevated, as the recent published remote code execution (RCE) vulnerability in Microsoft Teams shows. This vulnerability does not require any user interaction in order to compromise the victim’s computer, and could be misused by malware to propagate through a company autonomously. A similar RCE exploit for Zoom was offered for $500,000 during the lockdown.
The concept of working from home is not new and there are best practices available from various sources including the National Cyber Security Center (NCSC). Yet for many SMEs, the transition had to be implemented too quickly, and their limited resources and expertise meant they could not achieve a sufficient security level on their own. Many SMEs recognized their limits and turned to managed security service providers (MSSPs), while others did the best they could.
Closing any gaps and reviewing the solutions selected in haste to ensure they are secure needs to be addressed. Only then can organizations ensure the long-term viability of their work from anywhere capabilities.
2. Double Ransomware Extortion to Grow Further
In 2020, targeted ransomware groups shifted to a double extortion strategy – which involves stealing proprietary or embarrassing data and threatening to publish it – as this approach can maximize their profits. As of today, more than 1000 companies had their data already stolen and leaked by ransomware attacks.
The Maze group was responsible for about half of these breaches in the first half of the year before they announced that they are retiring. Unfortunately, with Egregor, Conti and DoppelPaymer, there is no shortage of ransomware gangs looking to fill this gap in 2021.
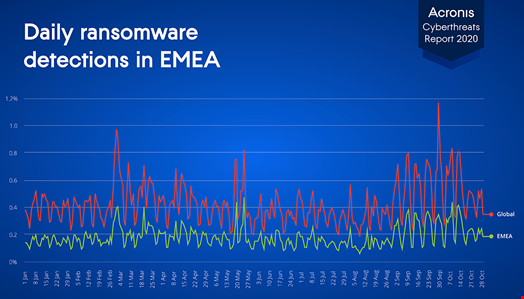
According to Acronis’ threat telemetry, the UK ranks fourth in EMEA, with 7.4% of all blocked ransomware cases in Q3 2020 occurring in the UK, right after Germany, France and Italy. The security predications are that the data extortion attacks as part of ransomware attacks will continue to grow and even expand to cloud and OT in 2021.
3. The Cloud is the New Attack Field
Attacks against unprotected cloud data storage buckets were already happening, but with so many businesses quickly adopting and transforming to the cloud during the pandemic, the surge caught the attention of cyber-criminals.
Thousands of Amazon AWS S3 buckets are still misconfigured so that anyone can download and alter the data in them, leading to large data breaches. The same applies to online databases, such as the French newspaper Le Figaro, which accidentally had 7.8 billion user records exposed to the public for several months inside an Elasticsearch database.
We expect this trend to grow even more in the coming year. Attackers will increasingly apply ransomware methods to online databases and cloud services. Cyber-criminals will hijack containers and cloud APIs to roll out malware – even if it’s simply to host threats online and bypass traditional URL filtering by co-opting the trust in the cloud domains from Amazon, Microsoft and Google.
Forecasting 2021 Cyber-Threats
It was no surprise that cyber-criminals used the COVID-19 pandemic to increase their attacks. They did not use groundbreaking new methods, but rather automated existing techniques to increase the frequency of their attacks.
As we detail in the Acronis Cyber-Threats Report 2020, it is expected that cyber-criminals will increase their attacks against employees working from home, since they can enhance their precision and frequency with the help of AI and automation. The adoption of double-extortion attacks will continue to spread, replacing encryption as the primary ransomware tactic, and in an effort to maximize the impact of their attacks, some ransomware groups will turn their focus on new fields such as cloud infrastructure, going after data buckets, serverless apps and containers.
The lessons learned from 2020 are providing a clear vision for the threats that lie ahead in the New Year. The question is how organizations will now prepare for 2021.

