Cloud apps are becoming the preferred choice of enterprise IT because they offer universal access, reduced costs, and support a variety of apps, thereby enhancing business productivity. And as cloud apps become more accessible, powerful and flexible, employees will continue to adopt them, often without sanction, for their ability to enable collaboration with anyone, anywhere, and on any device.
However, as with all new technologies, cloud apps pose their own unique set of security risks, and IT professionals are rightly concerned that sensitive corporate data remains susceptible to malicious insiders, sophisticated attackers, and even naive users.
A significant problem facing enterprises is shadow IT: unauthorized apps and devices in-use but not sanctioned by IT. Shadow IT can significantly expand the attack surface of the enterprise. A potentially greater risk is shadow data: the unknown sensitive content that may be lurking in both sanctioned and unsanctioned apps. The inappropriate sharing or leakage of shadow data to unauthorized parties could have devastating consequences.
Shadow IT and shadow data create an increased attack surface and risk of data exfiltration, so we refer to them collectively as the ‘dark cloud’.
The Rising Threat of the Dark Cloud
The main factor driving the rise of shadow IT is traditional IT’s ineffectiveness in addressing different use models and vulnerabilities in newer cloud technologies. One extreme is the BYO (bring your own) culture whereby employees walk in with their own devices, networks, and tools. With such high variation, monitoring data transfer is a nearly impossible challenge, pushing data once secured within the enterprise network perimeter into the dark cloud.
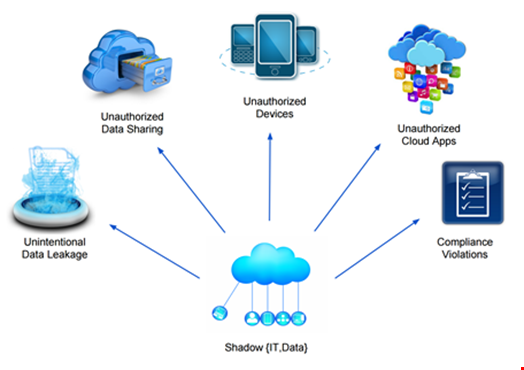
New and unsanctioned cloud apps introduced by employees pose a serious risk to enterprise data from a security and compliance standpoint. For example, if a sensitive document (containing, say, credit card payment information) is shared through an unsanctioned cloud app, it creates a potential exposure, with possible legal ramifications. Having only a public folder, the unsanctioned apps may lack proper sharing controls or, worse, be indexable by search engines (via a publish option). If the public exposure is left unmanaged, it may be assumed that the document will be leaked and reside permanently outside the control of the enterprise.
The feathery edge of the dark cloud even makes its way into the realm of sanctioned cloud apps and is a result of a lack of fine-grained visibility in the traditional security stack. For instance, consider a sanctioned file-sharing app that allows for public sharing. Next-generation firewalls can control access to specific apps on a device or user-by-user basis, and can provide insight into which apps a user accesses but not necessarily how they are using them.
Without fine-grained visibility into specific user actions, the only secure option to prevent public sharing is to block the app entirely, but the business value that cloud apps and services bring an organization increasingly precludes this option. This necessitates the development of new security technologies specifically designed for the cloud that are able to peer into specific user actions and set policies around them. Systems that can provide information about the data being accessed have the additional advantage of providing proactive protection against data exfiltration.
By comparison, traditional, on-premise software systems are either based around scanning traffic rooted in standards or signatures that are fixed or change slowly over time. Cloud apps, however, comprise a new class of systems capable of changing their traffic patterns, APIs, and feature sets at frequent intervals—really, at the speed of software sprints.
Penetrating and Securing the Dark Cloud
Cloud Access Security Brokers (CASBs) are addressing the challenge of securing the dark cloud through a variety of technologies and services such as discovery of shadow IT, classification of sensitive content, granular policy enforcement, detection of suspicious account behavior and so on. The key to penetrating the dark cloud, though, is gaining visibility and control, and this is where specific CASB security technologies are critical.
Before you can detect threats related to any specific technology, it is imperative to first detect the existence of that technology in the environment. This holds true for shadow IT where cloud app discovery and risk assessment are essential to identify all of the sanctioned and unsanctioned apps running in the organization.
In the absence of such an assessment, organizations will simply remain in the dark with regard to the risks associated with these apps and their potential exposure. It is also critical to establish visibility and control points so that cloud apps can be monitored in the environment. Furthermore, you need to deploy security policies and next-generation algorithms using data mining, machine learning, and natural language processing (NLP) techniques to detect and remediate data exposures when they occur.
The resultant next-generation security stack for cloud app security can identify malicious and anomalous behavior (analogous to what an IDS/IPS provides); detect undesirable content sharing (analogous to what a DLP solution provides); and apply behavior analytics and monitoring (analogous to what a network forensics tool provides).

Enterprise IT must educate employees to be aware of the potential dangers of the dark cloud and avoid the threats at the user level. In addition, policies such as a well-defined whitelist for sanctioned apps should be implemented to define the acceptable use policy for cloud apps.
Data should be secured via encryption while in motion or at rest as per requirements. Note, however, that encrypting data at rest might have unintended side effects of ‘breaking’ cloud apps and their integrations with other apps.
Finally, a mobile device management (MDM) solution should be adopted to implement strict control of the communication channels initiated through personal mobile devices. All the security measures discussed above provide a multi-layered security approach to subvert the risks mounted by the dark cloud.
Comprehensive CASB solutions can provide all of these services in the cloud. Just as cloud apps have improved the productivity of business services with reduced IT maintenance effort, cloud-based security operations can arm infosec teams with the latest up-to-date security features with no additional maintenance on the part of the enterprise. It also provides an infrastructure solution to ever-changing enterprise cloud apps—as such cloud apps are updated, CASBs are able to adapt quickly and accordingly to maintain fine-grained visibility without any intervention.
Mitigating Risk
The dark cloud encompasses both IT-sanctioned and unsanctioned cloud apps and the data resident in them. With the rise of cloud technology, the dark cloud is gathering around cloud services and apps. There is no doubt that cloud apps are more prone to accidental or malicious leakage of business-critical data, and the risk becomes much higher when these cloud apps are unsanctioned.
Overall, a multi-dimensional security approach and new security stack for the cloud are needed to penetrate the dark cloud and mitigate the risks that it poses.
