
Most 22-year-olds aren’t overly preoccupied with their health, but Jerome Radcliffe had good reason for concern. He had lost 40 lbs in two months, and was plagued by an insatiable thirst. He visited the doctor, who diagnosed diabetes and prescribed insulin. Radcliffe was given an insulin pump to dispense drugs into his body seven times a day. With his body taken care of, the security researcher began exercising his mind.
The system was wireless, enabling data to be entered from an external blood glucose device, and relayed to another external monitor. Radcliffe joked about a hacker breaking into his pump and messing with his glucose levels. Then, like any good hacker would, he decided to test it out.
“I discovered insecurities in the pump”, he recalls. “There were wireless features being used, unencrypted. I could do things to the pump that surprised me, such as turning it off.” At the Black Hat conference in 2011, he did just that, from a distance of 100 feet.
Hacking medical devices is becoming more plausible, and several experts are deeply concerned about the ramifications.
“I do think this is a problem”, says Lisa Gallagher, senior director of privacy and security for Healthcare Information and Management Systems (HIMSS). Her non-profit organization explores how to use IT systems to better manage healthcare. “These devices have software and in many cases actual operating systems loaded on them”, Gallagher observes. “In many cases, they will have vulnerabilities on them.”
There have been other examples of medical device hacking. In 2008, a team at the University of Washington hacked an implantable defibrillator, proving that it could be made to give up sensitive patient data in clear text; it could also be programmed to perpetually communicate with an unauthorized wireless device, in what could be turned into a denial-of-service attack.
Barnaby Jack, director of embedded device security at security firm IOActive, also hacked an insulin pump, forcing it to dispense its entire load from a distance of 300 feet – and then he went a bit further. In 2012, working with a team at IOActive, he developed test software that would wirelessly scan for new-model pacemakers and implantable cardioverter-defibrillators (ICDs). The tool enabled the attacker to rewrite the software on the devices, modify their settings, and in the case of ICDs, deliver high-voltage shocks.
“With the recent attack we demonstrated, it is possible to read all data off an implantable device”, Jack relayed at the time. “You could not only retrieve the software from the device, but you could also pull patient data. The patient data includes personal information as well as any recent cardiac conditions, and individual programming settings for the device.”
Government Involvement
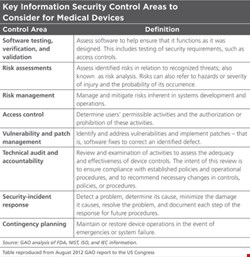
The dangers are severe enough to warrant government interest. In August 2012, the US Government Accountability Office released a report exploring the Food and Drug Administration’s role in evaluating the information security of medical devices. It identified security challenges (see Table) including possible remote access to devices and poor authentication, unencrypted data transfer, untested firmware or software, and an inability to patch it. Another issue for implanted devices was their limited battery life, which may make it difficult to introduce power-consuming security features, the report added.
The FDA told the GAO that while it considered unintentional risks to medical devices, such as electromagnetic interference, it didn’t consider malicious exploits in its review process at the time the report was written. It would re-evaluate its approach, it added.
“The FDA is taking steps that will help identify and address potential threats and other cybersecurity risks during our review of devices, as well as improving our postmarket surveillance of devices already on the market and in use”, said FDA spokesperson Michelle Bolek. These included evaluating its cybersecurity risk analysis procedures for software in medical devices, and “adopting consensus standards related to the integration of medical devices and information technology systems”.
The FDA also contributed to an international standard, ANSI/AAMI/IEC 80001-1:2010, which deals with the integration of medical devices and IT networks.
Security on the Ward
The risks exist in various classes of devices, and not just those implanted or attached to patients, Lisa Gallagher warns. Some devices, such as drug dispensers and monitoring equipment, are connected to a hospital’s traditional IT network. “So they must be considered for risk assessment in the enterprise. That may be missed, because the IT folks may not be aware of what the medical staff are connecting to the network”,
she cautions.
What could that mean, in reality? “You’re hooked to an infusion pump that’s full of morphine, and the hospital says you get 0.2 milliliters every hour”, Radcliffe postulates, laying out one scenario. “If a bad guy came in and said that it should deliver 20 milliliters per hour, that would be a fatal dose.” What if this kind of attack could be executed remotely, from half a world away? It’s a plausible threat, he says.
One of the dangers with non-implantable medical devices in a clinical environment is that they can often use commercial off-the-shelf software (COTS), explains Tim Gee, principal at Medical Collectivity Consulting, which focuses on workflow automation within medical devices and information systems.
“Most of the time, these are Windows-based systems”, he comments. “The approach that hospitals have taken with these systems is to route their networks in a way that exposes them to the internet.” This makes it possible for medical device systems to be contaminated by malicious software introduced on the network via, for example, an email attachment.
Telemedicine
The potential dangers open up even further as the industry moves into telemedicine. The healthcare industry recognizes the benefits of reducing outpatient visits using home monitoring and diagnostics devices. The ideal scenario involves patients who can use mobile devices and applications to monitor and report on their medical status, automatically sending the information to a central data store, where it can be analyzed by medical staff.
However, that introduces more links in the chain of communication, which could potentially be targeted by hackers. “If we look at mobile as a communications mechanism, there are devices being developed for attachment to mobile smartphones that the FDA is considering for categorization as medical devices”, Gallagher says.
A mobile device connecting to a central data store would use an internet connection managed by a communications provider. It may use an off-the-shelf smartphone system to gather the data. “You’d be looking at the types of vulnerability that would be introduced when you’re connected to those platforms”, she continues.
It is important not to over-exaggerate the current risk. The attacks demonstrated thus far have been theoretical; as both the GAO and FDA point out, there have been no known cybersecurity-related attacks on medical devices in the wild. After his Black Hat presentation in Las Vegas, and the onslaught of publicity, Radcliffe received hundreds of emails from parents and seniors worried about device security. “The reality is that these devices are very safe, and the risk to an individual is exceptionally low”, he points out.
One of the biggest barriers to entry for an attacker is the highly specialized nature of the hardware. As Radcliffe observes, you can’t pick up an MRI scanner from Best Buy, and in many cases access to medical devices is highly regulated. This alone will make it difficult for the average attacker to target such devices. Nevertheless, we should work to secure them, just as we lock our apartment doors when not expecting burglars.
Let’s Shut the Stable Door with the Horse Still in It
What can be done to make medical devices more secure? Ideally, all stakeholders in the healthcare value chain would be involved in the discussion. These include the patients, the healthcare providers, regulatory bodies, and the manufacturers of the hardware. The software vendors should be involved, as well as smartphone vendors when those devices are used to relay information in a telemedicine environment. Cellular network providers should also be included in the discussion, Gallagher contends.
“But primarily, I would provide tools and resources to healthcare providers”, she says. “They’re connecting devices to patients. What I would say is that this is part of their normal risk management process. We should be doing that, and not overlooking it.”
We have a lot to learn from the IT industry, Radcliffe asserts. In the bad old days, many large software vendors would be slow to address known security vulnerabilities, but he argues that things are changing. Many vendors now not only take reported security flaws seriously, but will even pay money for them in a bid to make their products secure.
What is the ultimate goal? Today, the feedback loop for medical devices is largely non-existent. Radcliffe would like to see a more positive environment, mirroring what we’ve seen in the IT world. Imagine walking into a physician’s office and having the doctor offer you a software update for your implanted device. “We need to look at something like that, and the FDA needs to encourage that kind of thing”, he concludes.
We are at the cusp of a major developmental period in healthcare technology, when electronic health records, advanced telemedicine technologies, and mobile devices all coincide to create new innovations in healthcare. As with any other industry, rapid innovation should not happen at the expense of security. The risks may be minimal right now – keeping them low as things develop is a priority. Security is one pill we can’t afford not to swallow.