The scale of Common Vulnerabilities and Exposures (CVE) reporting has grown exponentially during 2025, making it another record year in the domain.
According to Jerry Gamblin, principal engineer at Cisco Threat Detection & Response, 45,777 CVEs have been publicly reported to date – an average of 130.4 CVE reported every day this year – which represents a 19% growth compared with 2024.
The vulnerability expert forecasts a total of 46,407 CVEs reported at the end of 2025, which would reflect a 16.2% growth rate compared to 2024.
However, despite agreeing on these record-high numbers, Patrick Garrity, vulnerability researcher at VulnCheck, noted in a blog post that reporting of both critical and high-severity CVEs was down from 2024.
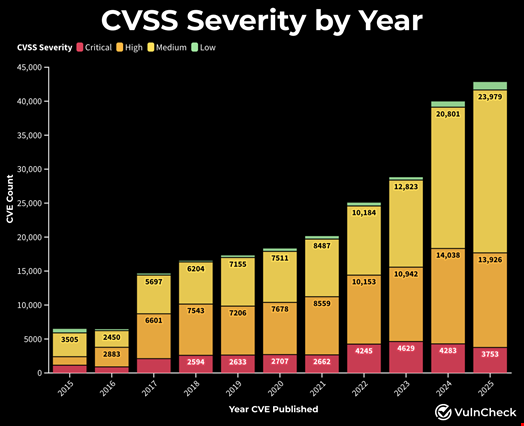
While this trend could come from the introduction of a new version of the Common Vulnerability Scoring System (CVSS v4.0), this is something that will need to be monitored in the future.
Nevertheless, 2025 was certainly marked by some significant high-severity and critical vulnerabilities whose exploitation by cybercriminals and nation-state groups caused major software supply chain incidents.
In this article, Infosecurity has set out five of the most significant vulnerability exploitation campaigns of 2025 that led to major software supply chain incidents. These have been decided based on factors such as the severity of the vulnerabilities, the scope of the organizations and individuals impacted and wider geopolitical implications.
The vulnerability exploits have been listed from the most recently reported incident to the oldest.
React2Shell: A Critical Flaw in React.js Exploited by Nation-State Groups
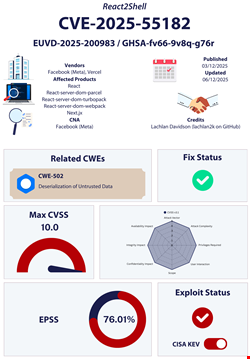
On November 29, security researcher Lachlan Davidson responsibly disclosed to Meta a critical remote code execution (RCE) vulnerability in React.js, a JavaScript library for building fast, interactive user interfaces (UIs) using reusable components.
Officially tracked as CVE-2025-55182, the flaw has been dubbed React2Shell, a not-so-subtle nod the Log4Shell vulnerability which was discovered in 2021.
React2Shell is a pre-authentication remote code execution (RCE) vulnerability which exists in React Server Components versions 19.0.0, 19.1.0, 19.1.1, and 19.2.0. React issued a security advisory with the relevant patches and updates on December 3.
Separately, Vercel’s the Next.js team published a security advisory and reported their own CVE, CVE-2025-66478, on December 3. However, the NVD rejected this CVE as a duplicate of CVE-2025-55182.
React and Next.js are JavaScript frameworks that are used in many modern web applications, their widespread use is cause for concern.
Successful exploitation of React2Shell could provide an attacker with the ability to run arbitrary code and assume control of the victim server. This could lead to broad compromise of sensitive data.
Just days after the disclosure of the vulnerability, Amazon Web Services (AWS) confirmed that threat groups including Earth Lamia and Jackpot Panda, both linked to Chinese state interests, are among those launching exploitation attempts.
Meanwhile, the Shadowserver Foundation identified over 77,000 vulnerable IPs following a scan of exposed HTTP services across a wide variety of exposed edge devices and other applications.
Other threat actors were also observed exploiting React2Shell, including opportunistic actors installing cryptocurrency miners (primarily XMRig) and credential harvesters targeting AWS configuration files and environment variables.
In early December, the Sysdig Threat Research Team (TRT) said they had discovered a novel implant from a compromised Next.js application that delivers EtherRAT. Their analysis revealed significant overlap with tooling from North Korea-linked campaign cluster dubbed ‘Contagious Interview.’ This suggests either North Korean actors have pivoted to exploiting React2Shell or that sophisticated tool-sharing is occurring between nation-state groups.
Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2025-66478 to its Known Exploited Vulnerabilities (KEV) list on December 17 and requested US government agencies to apply the patch by December 24.
Shai Hulud 2.0: The Worm That Poisons Thousands of Npm Packages
On November 24, Charlie Eriksen, a security researcher at Aikido Security, first discovered the wave of trojanized npm packages linked to the worm Shai Hulud 2.0. Other security firms like ReversingLabs, Wiz, Trend Micro and GitLab also quickly identified the threat and published their own analyses and guidance.
The Shai Hulud 2.0 campaign exploited compromised npm maintainer accounts to launch a sophisticated software supply chain attack between November 21 and 23.
Attackers used stolen credentials to push trojanized versions of legitimate npm packages, including those from Zapier, ENS Domains, PostHog and Postman, embedding malicious payloads and abusive preinstall lifecycle scripts.
These scripts executed immediately upon dependency installation, bypassing typical testing and software composition analysis (SCA) checks. The attack’s first signs appeared on November 24, when GitHub Archive telemetry revealed attacker-created repositories designed to exfiltrate stolen secrets, followed hours later by the initial malicious npm uploads.
Once installed, the payload fingerprinted the environment, distinguishing between CI runners and developer workstations, then harvested credentials from local config files, environment variables, and cloud metadata services (AWS, Azure, GCP). Stolen secrets—including GitHub personal access tokens and cloud keys—were dumped into files like cloud.json and truffleSecrets.json and exfiltrated to attacker-controlled GitHub repositories, often with descriptions referencing ‘Shai Hulud’ or ‘The Second Coming.’ Cross-victim exfiltration meant one organization’s data frequently appeared in another’s compromised repository, amplifying the breach’s impact.
In the second phase, attackers leveraged stolen GitHub tokens to hijack GitHub Actions and self-hosted runners, registering compromised machines as runners named "SHA1HULUD." They deployed backdoored "formatter" workflows capable of exfiltrating GitHub’s entire secret store via toJSON(secrets) and enabling remote command execution through malicious discussion.yaml files, effectively turning CI infrastructure into a persistent backdoor. The attack demonstrated how GitHub’s automation features could be weaponized for lateral movement and long-term access.
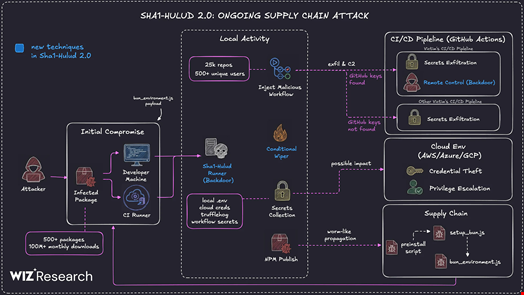
By late November, Wiz estimated more than 25,000 repositories across roughly 500 GitHub users had been created or hijacked as part of Shai‑Hulud 2.0, with around 700 npm packages implicated – making this second wave substantially larger than the original September 2025 Shai‑Hulud worm.
Oracle E-Business Suite Flaw: Clop Exploits Zero Day Vulnerability
In early October 2025, Oracle advised customers that hackers may be exploiting vulnerabilities in unpatched instances of its E-Business Suite (EBS).
This warning came after Google Threat Intelligence Group (GTIG) reported that an individual or group of hackers were sending extortion emails to executives in several companies, claiming to have stolen sensitive data from the EBS.
The exploit campaign was attributed to the Clop group, a notorious Russian-speaking ransomware-as-a-service (RaaS) cybercrime gang first identified back in 2019.
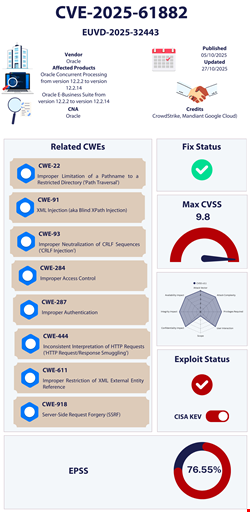
The vulnerability exploited in the EBS campaign, CVE-2025-61882, was a critical zero-day with a CVSS 3.1 rating of 9.8. Oracle released a patch in an emergency update on October 5.
When successfully exploited, CVE-2025-61882 results in RCE. CISA added the vulnerability to its KEV list on October 6 and requested US government agencies to apply the patch by October 27.
GTIG said it was exploited by Clop hackers alongside other flaws for which Oracle released patches in its July 2025 Critical Patch Update.
A large number of organizations are believed to have been targeted, including, Barts Health, a London-based NHS trust, Japanese photography giant Canon, GlobalLogic, a US-headquartered software company owned by Japanese conglomerate Hitachi, US Autoparts Maker LKQ, Logitech and Mazda.
ToolShell: On-Prem SharePoint Customers Targeted in Chained Exploit
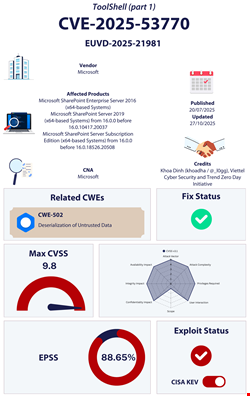
In late July 2025, Microsoft warned that attackers were actively exploiting SharePoint vulnerabilities in campaign targeting SharePoint on-premises servers and impacting critical sectors like government and healthcare.
The attack campaigns chained two critical and high-severity vulnerabilities, CVE-2025-53770 and CVE-2025-53771, in internet-facing SharePoint servers. The chained exploitation of these two flaws was dubbed ‘ToolShell’ by the cybersecurity community.
CVE-2025-53771 is a variant of CVE-2025-49706, while CVE-2025-53770 is a variant of CVE-2025-49704, two previously disclosed vulnerabilities.
While Microsoft released a patch for these vulnerabilities in July, Dutch cybersecurity company Eye Security confirmed that a total of 396 SharePoint systems has been compromised.
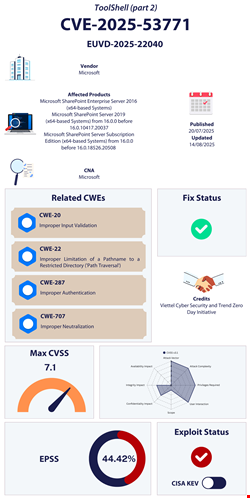
CISA added CVE-2025-49706 and CVE-2025-53771 to its KEV list on July 22, urging US government agencies to apply the patches by the next day.
Some of the first threat groups behind the ToolShell exploitation were rapidly identified as Linen Typhoon (APT27) and Violet Typhoon (APT31), two Chinese-aligned advanced persistent threat groups as well as Storm-2603, a more hybrid group as it is known for deploying ransomware but believed by Microsoft researchers to be based in China.
Other reporting suggested that the notorious Chinese hacking group Salt Typhoon may also have attempted to target government entities with the ToolShell exploit.
Within a few months, the chained exploits were allegedly attempted by numerous threat actors, with almost 40% of Cisco Talos Incident Response (Talos IR) engagements recorded in late October targeting the exploitation of public-facing SharePoint servers.
Attackers typically exploit these flaws to deploy web shells, steal sensitive data or pivot deeper into targeted networks, making it a potent tool for espionage, ransomware deployment and persistent access in high-value sectors like government, healthcare and critical infrastructure.
CitrixBleed 2: Another Revenant Affecting Citrix Appliances
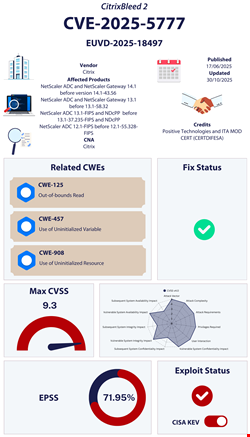
At the end of June, a new critical vulnerability in Citrix NetScaler ADC and Gateway devices, bearing similarities to the notorious CitrixBleed flaw of 2023, was reportedly being exploited in the wild.
Dubbed CitrixBleed 2 by independent security researcher Kevin Beaumont, this out-of-bounds read could allow attackers to bypass authentication mechanisms, including multifactor authentication (MFA), and hijack user sessions.
The flaw, officially tracked as CVE-2025-5777, was disclosed by Citrix on June 17 alongside CVE-2025-5349, an access control issue. The former has a severity score (CVSS v4.0) of 9.3 and the latter 8.7.
A June 26 report by ReliaQuest claimed “with medium confidence” that attackers are actively exploiting CVE-2025-5777 to gain initial access to targeted environments. According to the researchers, while CitrixBleed 2 mirrors the original CitrixBleed in its ability to bypass authentication and facilitate session hijacking, this new flaw introduces new risks by targeting session tokens instead of session cookies.
Additionally, Citrix disclosed a third vulnerability affecting NetScaler ADC and Gateway devices on June 25.
In early July, researchers from WatchTowr published technical details of a detection script which can be used to identify exploitation of the CitrixBleed 2 vulnerability.
CISA added CVE-2025-5777 to its KEV list on July 10, urging US government agencies to apply the patch by the next day.
