Zero-day exploits are at an all-time high. After what some called a “hot zero-day summer,” which saw a frenzy of security patches follow a torrent of newly discovered software vulnerabilities, the month of September 2023 was no quieter: Google Threat Analysis Group (TAG) observed 12 single zero-day vulnerabilities exploited in the wild for this month alone.
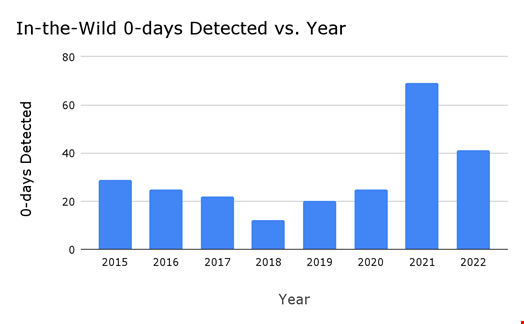
With 69 disclosed zero-days so far, 2023 is on track to set a new record, currently held by a pandemic high of 88 zero-days in 2021.
Used by state-sponsored groups and cybercriminals alike, zero-day exploits have become threat actors’ new Holy Grail for the lucrative results they yield from it, according to John Hultquist, chief analyst at Mandiant Intelligence.
“Yes, zero-days cost a lot of money, but the pay-out is just so big – tens of millions of dollars – that it’s worth it for them,” he told Infosecurity during the latest Mandiant mWISE conference.
What Does Zero Day Mean?
A zero-day (also known as a 0-day) vulnerability is a software issue unknown to the software vendor which an attacker can leverage to gain unauthorized access to a network, move laterally within it, steal data or compromise part of the system.
The name zero day comes from the fact that those vulnerabilities leave no time to fix them before they're exploited. This means that no patch or workaround is available to fix the vulnerability, making it very dangerous.
Zero-day vulnerabilities can affect any piece of software on a device – including operating systems, applications and web browsers.
They are often discovered by security researchers or attackers themselves. Once a zero-day vulnerability is discovered, it is important for security researchers to keep it confidential until a patch is available. Otherwise, attackers can exploit the vulnerability to attack exposed systems.
Sometimes, a vulnerability that is known by the vendor but does not have a patch yet – or cannot be patched – is also called a zero-day.
Google Project Zero, an initiative gathering a team of security analysts employed by Google tasked with finding zero-day vulnerabilities, distinguishes zero-day vulnerabilities with “zero-day exploits in the wild,” which refer to zero-day vulnerabilities already used in cyber-attacks.
Of the 69 zero-days disclosed in 2023, 44 have been used in the wild from January to September, according to Google's Threat Analysis Group. In 2022, Google observed 41 zero days exploited in the wild.
Why Are Zero-Day Exploits on the Rise?
Since zero-days have been used by different types of threat actors, there are multiple reasons why they’ve become prominent tools of cyber intrusion.
First, Chinese state-sponsored threat actors have been heavily relying on zero-days for gaining initial access since at least the COVID period.
Ben Read, head of cyber espionage analysis at Mandiant, said during mWISE that Chinese hackers have been the top state-sponsored threat actors regarding zero-day usage over the past three years and are responsible for most of the exploited zero-days in 2023.
"The 50% year-on-year increase in ransomware is in large part due to the deployment of zero-days."
According to Sandra Joyce, Mandiant’s head of global intelligence, this is the result of a recent reorganization of the People's Liberation Army (PLA) and the Chinese Ministry of State Security (MSS), meaning that China has put a greater focus on using cyber as an asymmetric capability.
“Some of them have reached a level of sophistication that allows them to exploit a zero-day vulnerability in a few hours without getting detected – and sometimes it takes us, defenders, a long time to figure out how they did it,” she added.
Other cybercriminals have also recently increased their use of zero-days.
During mWISE, Jacqueline Burns Koven, head of cyber threat intelligence at Chainalysis, partly attributed the rise of ransomware attacks to zero-days: “We certainly see an increase in the use of zero-days by ransomware actors. This year has seen nearly $500m worth of ransomware payments – a 50% year-on-year increase – which is in large part due to the deployment of zero-days in ransomware attacks.”
Read more: Why Zero Days Are Set for Highest Year on Record
Where Do Zero-Day Vulnerabilities Come From?
The Big Tech companies, which develop nearly all the operating systems used worldwide (Windows, Android, iOS and MacOS) are generally the leading ‘purveyors’ of zero-day vulnerabilities – unintentionally, of course.
In 2022, nearly 70% of all zero-days came from Microsoft, Google and Apple products and services, according to Mandiant.
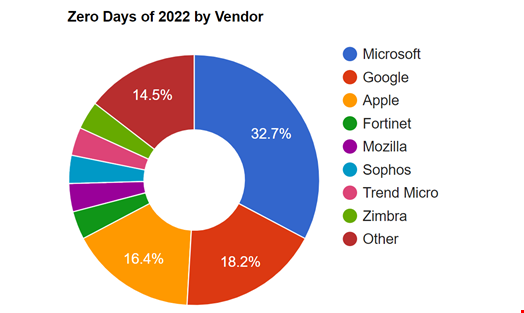
In its 2022 annual report, Google Project Zero also observed that zero days in browsers had significantly decreased while new trends had started appearing, such as the emergence of 0-click exploits, particularly used for deploying spyware.
They also found that over 40% of the zero days discovered were variants of previously reported vulnerabilities.
While we’re still awaiting substantial granular reports on 2023 zero-day data, Microsoft, Google and Apple were among those concerned by the June 2023 wave of disclosed 0-days – the now so-called “hot zero-day summer” – alongside Firefox browser maker Mozilla and enterprise software providers, including Oracle, Citrix, Salesforce and SAP.
The underground zero-day market is a complex ecosystem where cybercriminals and state-sponsored actors can buy full or partial zero-day exploits – in which case they are called “half-days” – with cryptocurrencies.
Why Should Zero Days Matter to End-Users?
Although the rise of zero-day exploits may sound concerning, experts like Google’s Maddie Stone and Patrick Garrity, a cybersecurity researcher at Nucleus Security, argue that the impact of zero-day attacks is much more important than the sheer volume.
They mean that a single zero-day exploit can have a much more significant impact than a series of zero-days in another, depending on the criticality level of the vulnerability and the time the vendor took to patch it or release workarounds.
Joyce commented: “[For instance], UNC4841, a Chinese threat group responsible for targeting the Barracuda email security gateway (ESG) appliances by exploiting a zero-day in April 2023, compromised hundreds of organizations around the world.”
Another 2023 supply chain attack, the MOVEit campaign, has affected 2120 organizations and over 62 million individuals worldwide, according to Emsisoft data.
How to Mitigate the Zero-Day Threat:
End-users are very vulnerable to zero-day threats since they rely on the vendors to patch them or release a workaround.
However, Google Project Zero’s 2022 report outlines three mitigation measures organizations should deploy to prevent their systems from being compromised:
- Comprehensive and timely patching to address the use of variants and n-days as 0-days.
- More platforms following browsers’ lead in releasing broader mitigations to make whole classes of vulnerabilities less exploitable.
- Continued growth of transparency and collaboration between vendors and security defenders to share technical details and work together to detect exploits.
Read more: US Government Ordered to Urgently Patch Apple Zero-Day Bugs
