Leaked documents purportedly originating from a Chinese security company shed light on the nation's commercial cyber espionage industry. The leaked data constitutes an unprecedented opportunity for cyber threat intelligence (CTI) researchers.
Documents were uploaded to GitHub that had belonged to I-Soon (aka iSOON, Sichuan Anxun, Anxun Information), a security contractor of China’s Ministry of Public Security (MPS) registered in Chengdu, the capital city of the Chinese province of Sichuan.
PNG files of screenshotted documents, including call logs and presentation slides from employees of I-Soon, were included in the GitHub leak.
In a blog post, Aleksandar Milenkoski and Dakota Cary, threat researchers at SentinelOne, said, “The leak provides some of the most concrete details seen publicly to date, revealing the maturing nature of China’s cyber espionage ecosystem. It shows explicitly how government targeting requirements drive a competitive marketplace of independent contractor hackers-for-hire.”
Although many voices from the CTI community confirmed the data coincided with previous reporting, the legitimacy of the documents and the source remains unknown.
Timeline: From a Custom Email Address to the Leak Takedown
According to SnetinelOne’s Milenkoski and Cary, someone registered the i-soon@proton[dot]me email address on January 15, 2024.
On February 5, a spokesperson at the Chinese Embassy in Manila said, "The Chinese government all along firmly opposes and cracks down on all forms of cyber-attack in accordance with the law, allows no country or individual to engage in cyber-attack and other illegal activities on Chinese soil or using Chinese infrastructure."
Eleven days later, on February 16, an account associated with this email address began uploading content to GitHub, a Microsoft-owned website hosting repositories for the developers' community, under the name I-S00N.
The repository included dozens of documents associated with the hacker-for-hire branch of I-Soon, a company founded in Shanghai in 2010 with an office in Chengdu, Sichuan. The company is known as Anxun in China.
An analyst based in Taiwan, known on X under the handle @AzakaSekai_, found the document trove on GitHub and shared their findings on social media on February 18.
Many CTI analysts spent the following days trying to analyze the documents. This proved to be a difficult task, given that most of the text was in Mandarin.
On February 23, the I-S00N repository was taken down.
Are the Leaked Documents Legit or Fake?
The Data Looks Genuine
One of the primary questions that most CTI analysts asked while analyzing the data was whether these documents and their data were legitimate.
Speaking to Infosecurity, Will Thomas, a threat researcher at Equinix, said, “Based on the level of detail, leaked chat logs, amount of data, and corroboration from overlaps indicators of compromise (IOCs), I have medium-to-high confidence it is legit."
John Hultquist, chief analyst of Mandiant Intelligence at Google Cloud, also told Infosecurity: "We have every reason to believe this is the authentic data of a contractor supporting global and domestic cyber espionage operations out of China.”
A French cybersecurity consultant who asked to remain anonymous shared the same conclusion.
“It's complicated to estimate because there are many unknowns to cover. […] We're not safe from a honeypot either, there's a lot of information and misinformation circulating these days. But in view of the initial research and analyses that are being carried out, it's moving in the direction of confidence,” he told Infosecurity.
Journalists from the American press agency Associated Press said they received confirmation the data was legitimate from two I-Soon employees.
Speculation Surrounds the Origin of the I-Soon Leak
Although the source of the leak remains unknown, cybersecurity vendor Malwarebyte believes that it came from a disgruntled employee of I-Soon.
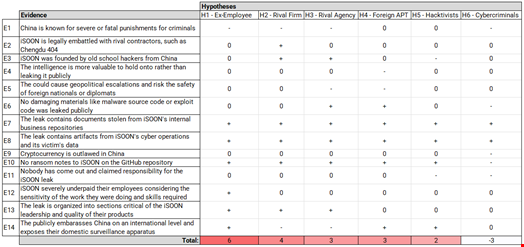
In a blog post, Equinix’s Thomas suggested a list of potential candidates, including:
- An I-Soon revengeful ex-employee
- A rival Chinese contractor
- A rival Chinese agency to the MPS
- A foreign intelligence agency
- An anti-CCP hacktivist
- A Chinese cybercriminal
He assessed that a revengeful ex-employee was the most likely to have leaked the documents. His conclusion was based on an analysis comparing the elements included in the data dump and the motives of each candidate – following a threat intelligence research method called ‘Analysis of Competing Hypothesis’ (ACH).
I-Soon has not confirmed whether the leak is genuine. It declined requests for comment from several press agencies, including Agence France Presse.
What Is in the I-S00N Repository?
Over 570 Documents
The I-S00N repository included 577 files in four different formats (txt, logs, md, and png), representing around 170MGB of data. Some appear to be dated as recently as 2022.
Among the files uploaded were dozens of marketing documents, business documents, thousands of WeChat messages between employees and clients of I-Soon, and what appears to be stolen victim data, such as credentials and even call detail records (CDRs) from hacked telecommunications companies. No source code was included.
I-Soon’s Hacking Offering and Business Practices
The leaked materials appear to show how a commercial entity developed cyber espionage tools in support of Chinese-affiliated threat actors.
According to a presentation in the leak, the structure of I-Soon includes three penetration teams, one security research team, and one basic support team, comprising around 70 people.
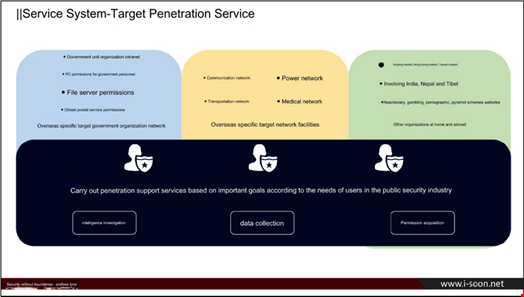
The business documents include pitches and presentation slides about the company’s services, including “penetration testing” – i.e., hacking tools – and surveillance operations.
These include:
- Custom remote access Trojans (RATs) designed to run on Windows, macOS, Linux, iOS and Android
- A platform to collect and analyze email data
- A platform to hack into Outlook accounts
- A Twitter monitoring platform
- A reconnaissance platform using open-source intelligence data
- Physical hardware devices used for tracking down WiFi devices and disrupting WiFi signals
- Communications equipment using a Tor-like network for agents working abroad
The selection of documents and chats also disclosed some business practices.
For instance, one document lists targeted organizations and the fees the company earned by hacking them.
“Collecting data from Vietnam’s Ministry of Economy paid out $55,000, other ministries were worth less,” SentinelOne researchers noted.
Another leaked message exchange showed an employee hacking into a university not on the target list, only for their supervisor to brush it off as an accident.
In some chats, I-Soon employees complained about low pay and hoped to get jobs at other companies.
I-Soon’s Targets
The company’s primary targets are countries in regions such as Central Asia, Southeast Asia, Hong Kong, Macao, and Taiwan.
“Notably, I-Soon featured in a slide deck their attacks on the Indian and Nepalese governments, targeting government departments such as the Ministry of Foreign Affairs, Defense, Home Affairs, Finance, and the Nepalese Presidential Palace,” Thomas commented in his blog post.
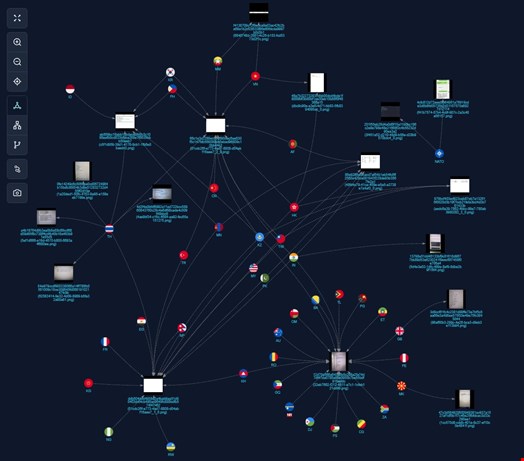
However, according to conversations and spreadsheets in the leak, analyzed by @AzakaSekai_, I-Soon also conducted hacking campaigns outside of Asia.
The security researcher found evidence of data exfiltration campaigns targeting government entities, telecommunications firms, medical organizations, and academic sectors of countries in Europe (France), Africa (Nigeria, Rwanda, Egypt) and the Middle East (Turkey).
Some business pitches also show I-Soon’s interest in landing surveillance contracts in China’s Xinjiang province, home of the country’s Uyghur Muslim minority, and in Tibet.
“In a bid to get work in Xinjiang, the company bragged about past counterterrorism work,” noted SentinelOne researchers.
Involvement of I-Soon in Nation-State Operations
Ironically, the leak included a slide deck advertising the company’s “APT Team,” referring to advanced persistent threat groups. APT is a term coined by the US cyber threat intelligence community to describe nation-state cyber adversaries.

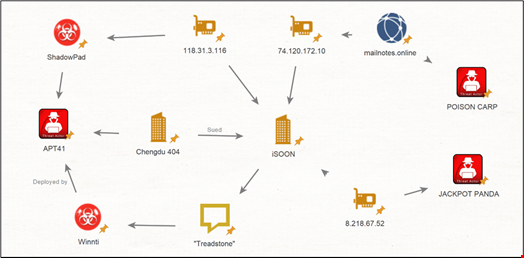
Before the leak, threat intelligence analysts had already revealed ties between I-Soon and Chinese nation-state groups, including Chengdu 404, linked to APT41 (aka Double Dragon, BARIUM, Axiom, Wicked Panda, Brass Typhoon).
The CEO of I-Soon, Wu Haibo (referred to as ‘Shutdown’ in the leaked chats), is a well-known hacker and an early member of Green Army, the first Chinese hacktivist group founded in 1997.
The data included in the I-Soon repository aligns with previous threat intelligence reports on several named threat groups. This adds further legitimacy to the validity of the leak, according to Thomas.
It also shows the involvement of I-Soon in other malicious campaigns, including:
- The 2019 Poison Carp Attack, in which attackers, attributed by the Citizen Lab to a Chinese threat group called Poison Carp, targeted Tibetan groups via multiple iOS and Android exploit
- A September 2022 supply chain attack on the Canadian software company Comm100
Conclusion: A Milestone in Open Source Cyber Threat Intelligence
If the I-S00N leak and its data are legitimate, it is one of the most significant cyber threat updates related to China in recent years.
It confirms many hypotheses and assessments made by threat intelligence analysts in the past about the firm’s involvement in Chinese-backed hacking operations.
It also offers valuable knowledge to the cyber threat intelligence community, including:
- Highlighting how both the Chinese MPS and Chinese Ministry of State Security (MSS) outsource their intelligence gathering to commercial surveillance vendors
- Confirming the intertwined relationships between APT groups and the private sector in China
- Offering a unique opportunity to reevaluate past attribution efforts and gain a deeper understanding of the complex Chinese threat landscape
According to Equinix’s Thomas, the I-S00N leak has revolutionized the open source intelligence (OSINT) community's general understanding of the Chinese MPS' cyber operations.
