Google Chrome has long been a popular web browser, but since the introduction of the headless mode functionality, the browser has grow in popularity not only among software engineers and testers but also with attackers, according to Imperva.
According to recently published research, "Headless Chrome: DevOps Love It, So Do Hackers, Here’s Why," the headless technique has grown more popular, particularly since Chrome introduced the functionality last year. Additionally, malicious actors are using the technique to target specific sites and exploit newly released vulnerabilities.
When Chrome is running without its “head," or GUI, the latest full version of the Chrome browser is executed with the added perk of being able to control it programmatically on servers without dedicated graphics or display.
“In headless mode, it’s possible to run large scale web application tests, navigate from page to page without human intervention, confirm JavaScript functionality and generate reports,” wrote Imperva’s Dima Beckerman.
While DevOps appreciates the ability to benignly run large scale tests, attackers are able to leverage the same functionality for malicious purposes by evaluating JavaScript or emulating browser functionality.
“We observe more than 10K unique IP addresses daily performing scraping, sniping, carding, blackhat SEO and other types of malicious activity where JavaScript evaluation is necessary to perform the attack,” Beckerman said.
While automation in web browsers isn’t exclusive to Chrome, said Beckerman, “in comparison to other headless browsers and automation frameworks, Headless Chrome overtook the previous leader, PhantomJS, within a year of its release.”
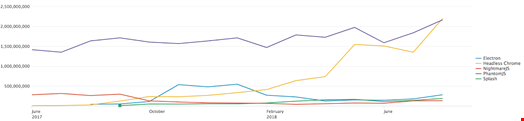
In addition to Chrome constantly adding new features and introducing new trends in web development, Headless Chrome has also become popular because of its support for a wide range of operating systems. DevOps appreciates Chrome’s convenient development tools and features, according to Imperva.
However, as much as DevOps has embraced Headless Chrome, “Chrome occupies the top of the 'attackers’ podium,' with half of the malicious traffic divided evenly between execution in headless and non-headless mode,” Beckerman wrote.
Because Headless Chrome is used for both malicious and legitimate purposes, Beckerman said blocking the automated browser should be done on a case-by-case basis, depending on the intent and behavior of each individual IP address.
