A Microsoft developer has found a backdoor in a software package of a compression library widely used in Linux systems that could have resulted in a massive software supply chain attack.
The author of the backdoor was a maintainer of the open source library and had spent years developing the software compromise.
How the XZ Utils Backdoor Was Found
On March 28, Andres Freund, a principal software engineer at Microsoft and one of the developers of PostgreSQL, found a vulnerability in liblzma, a software package part of XZ Utils, a library for compressing and decompressing files on computers, especially in Linux systems.
Freund noticed failing Secure Shell (SSH) logins using a substantial amount of Computing Processing Unit (CPU), along with a longer than usual delay of 500ms on his SSH session.
This led him to realize that a significant amount of CPU time was being consumed by liblzma. Upon further investigation, he found a remote code execution (RCE) vulnerability in the liblzma software package.
This backdoor allowed remote attackers to bypass SSHD authentication and gain complete access to an affected system.
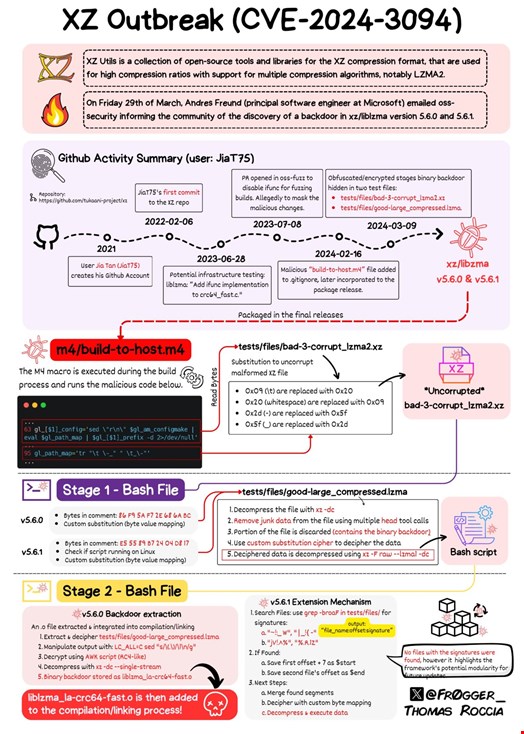
Freund quickly shared his findings with the open source community, including via messages to maintainers of Linux distribution Debian and the open source mailing list oss-security@openwall. He also posted the news on social media.
A Supply Chain Catastrophe Averted
The XZ Utils library is used on almost all Linux and other Unix-like operating system installations. It acts like a data zipper, shrinking files to save storage space and bandwidth.
According to a report by crowdsourced security provider Bugcrowd, all users of operating systems running XZ Utils versions 5.6.0 and 5.6.1 are impacted. This includes:
- Linux distributions that have adopted these newer releases, including Fedora 41 and Rawhide, and possibly some macOS versions
- Debian’s testing, unstable, and experimental branches
- Kali Linux users who updated their OS between March 26 and March 29, 2024
Other unstable Linux-based systems, such as open SUSE and Arch Linux, could also be affected.
Some Linux distributions have already indicated they are not affected. These include:
- Ubuntu
- Alpine Linux
- Amazon Linux
- Red Hat Enterprise Linux
- Gentoo
- Linux Mint
The discovery was made just weeks before the backdoor was included in the latest version of Debian and Red Hat, the two biggest distributions of Linux.
Following Freund’s warning, Red Hat registered the vulnerability as CVE-2024-3094 and assessed it as a maximum severity risk score (CVSS 10).
The US Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory that urged organizations using affected Linux distributions to downgrade their XZ Utils to an earlier version and report any potential activity related to the backdoor.
Debian rolled back its upcoming version (5.6.1) and introduced version 5.6.1+, which is based on version 5.4.5.
“XZ Utils users should downgrade to an older version of the utility immediately (i.e., any version before 5.6.0) and update their installations and packages according to distribution maintainer directions,” warned security firm Rapid7 in a report.
A Backdoor Implanted by a Trusted Maintainer
The news of the XZ Utils backdoor came as a shock to most within the open source community.
In a blog post, JFrog researchers said, “XZ Utils was considered a trusted and scrutinized project."
According to security researcher Evan Boehs, the backdoor was implanted a long time ago by a trusted maintainer of XZ Utils, known by the moniker JiaT75 (or Jia Tan).
Active on GitHub since 2021 and contributing to XZ Utils since at least 2022, the person behind the Jia Tan persona has allegedly been planning this scheme for several years.
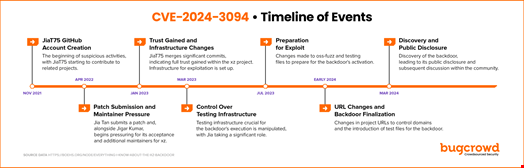
A complete timeline of events related to the XZ Utils backdoor can be found here.
