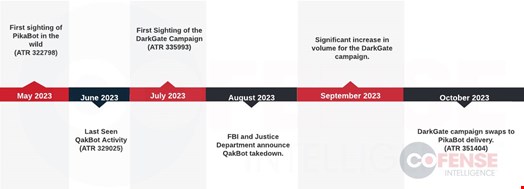
Successors to the QakBot malware have emerged despite the disruption to QakBot infrastructure by an international law enforcement operation led by the FBI in August 2023.
Cofense, a phishing detection solution provider, has observed new phishing campaigns that use the same infection tactics QakBot was known to deploy. However, these recent campaigns deliver two new malware families, DarkGate and PikaBot.
One phishing campaign began spreading DarkGate malware in September and has grown to become one of the most advanced phishing campaigns active in the threat landscape, according to a report by Cofense. The campaign has evolved to use evasive tactics and anti-analysis techniques to continue distributing DarkGate and, more recently, PikaBot.
Typical QakBot tactics observed in the DarkGate and PikaBot campaigns included:
- Hijacked email threads as the initial infection
- URLs with unique patterns that limit user access
- An infection chain nearly identical to QakBot delivery
Cofense researchers believe that some previous QakBot users have shifted to using DarkGate and/or PikaBot.
Some of these campaigns are “undoubtedly high-level threat[s] due to the tactics, techniques, and procedures (TTPs) that enable the phishing emails to reach intended targets as well as the advanced capabilities of the malware being delivered,” added the report.
Most of the post-QakBot takedown campaigns involve different infection chains.
“Almost as if the threat actors were testing different malware delivery options,” Cofense said.
However, the most used infection chain shows many similarities with some QakBot campaigns conducted in May 2023.
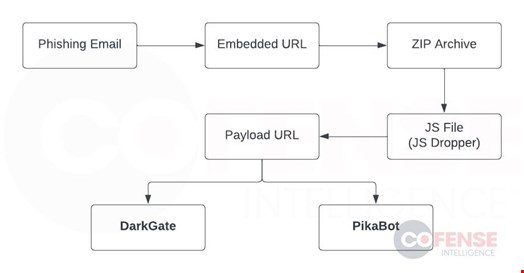
“The campaign begins with a hijacked email thread to bait users into interacting with a URL that has added layers that limit access to the malicious payload only to users that meet specific requirements set by the threat actors (location and internet browser),” outlined Cofense researchers.
“This URL downloads a ZIP archive that contains a JS file that is a JS Dropper, which is a JavaScript application used to reach out to another URL to download and run malware. At this stage, a user has been successfully infected with either the DarkGate or PikaBot malware.”
Some of these newly observed campaigns disseminated a high volume of emails to a wide range of industries, putting targets at risk of more sophisticated threats like reconnaissance malware and ransomware.
Read more: FBI-Led Operation Duck Hunt Shuts Down QakBot Malware
What are the DarkGate and PikaBot Malware Families?
DarkGate and PikaBot are both considered advanced malware with loader capabilities and anti-analysis behavior.
DarkGate is a versatile malware toolset, typically spread through spam email attachments or malicious links, that has been active since 2017. It is equipped with various capabilities, including data stealing, cryptocurrency mining and remote control of infected systems.
Once installed, DarkGate can steal a variety of sensitive information, including passwords, credit card numbers and personal documents. It can also mine for cryptocurrency, which can use the victim's computer resources to generate money for the attackers.
In addition, DarkGate can allow attackers to remotely control the infected system, which could be used to install other malware, steal data or launch attacks against other systems.
PikaBot is a new malware family first observed in 2023. It is classified as a loader due to its ability to deliver additional malware payloads. It contains several evasive techniques to avoid sandboxes, virtual machines and other debugging techniques.
PikaBot is typically spread through phishing attacks or by exploiting vulnerabilities in software. Once installed, PikaBot can be controlled by attackers remotely.
It has been observed to exclude infecting machines in Commonwealth of Independent States (CIS) countries – all members of the former Soviet Union.
How Was QakBot’s Infrastructure Taken Down?
In August, the FBI led Operation Duck Hunt, a multinational law enforcement operation that allegedly dismantled QakBot.
To do this, the FBI gained access to QakBot’s admin computers, which helped law enforcement map out the server infrastructure used in the botnet's operation. It then seized 52 servers, which it said would “permanently dismantle” the botnet, and redirected QakBot’s traffic to servers controlled by the Bureau, pointing victims to download an uninstaller.
In an additional announcement, the US Department of Justice (DoJ) said the FBI had identified over 700,000 infected computers worldwide, including more than 200,000 in the US.
The DoJ also announced it seized over $8.6m in cryptocurrency from the QakBot cybercriminal organization. This money will be returned to the victims.
While the cybersecurity community has generally praised Operation Duck Hunt, voices doubted the real impact of the takedown.
The possibility that threat actors would be moving to use other malware families to deploy the same type of malicious campaigns was one of the criticisms about the efficacy of such an operation.
Read more: FBI's QakBot Takedown Raises Questions: 'Dismantled' or Just a Temporary Setback?

