The 28th United Nations Climate Change Conference (COP 28), held in Dubai at the end of 2023, sparked an “unprecedented surge” in distributed denial of service (DDoS) attacks against environmental services.
In its DDoS Threat Report for 2023 Q4, content delivery provider Cloudflare found a 61,839% spike in HTTP DDoS attack traffic targeting environmental services’ websites in the last quarter of 2023 compared with the same period in 2022.
These attacks marked a shift from the previous domination of cryptocurrency-related DDoS attacks.
DDoS attacks targeting environmental websites constituted half of all observed DDoS during that quarter.
Cloudflare observed a similar trend during the COP26 and COP27 summits and other UN-related environmental events and publications.
“In February and March 2023, significant environmental events like the UN's resolution on climate justice and the launch of United Nations Environment Programme’s Freshwater Challenge potentially heightened the profile of environmental websites, possibly correlating with an increase in attacks on these sites,” reads the report.
“This recurring pattern underscores the growing intersection between environmental issues and cyber security, a nexus that is increasingly becoming a focal point for attackers in the digital age.”
What is an HTTP DDoS Attack?
A DDoS attack is a type of cyber-attack that aims to disrupt websites and online services for users, making them unavailable by overwhelming them with more traffic than they can handle.
“They are similar to car gridlocks that jam roads, preventing drivers from getting to their destination,” Cloudflare researchers wrote.
Sometimes, threat actors use networks of devices, called botnets, programmed to automatically send requests to the same website to conduct DDoS attacks.
In the report, Cloudflare identified three main types of DDoS attacks:
- HTTP request intensive DDoS attacks: they aim to overwhelm HTTP servers with more requests than they can handle to cause a denial-of-service event
- IP packet-intensive DDoS attacks: they aim to overwhelm in-line appliances such as routers, firewalls, and servers with more packets than they can handle
- Bit-intensive attacks: they aim to saturate and clog the Internet link, causing a ‘gridlock’
2023 DDoS in Numbers
Globally, DDoS attacks have been thriving in 2023, according to Cloudflare.
The content delivery provider said the Internet community faced a persistent and deliberately engineered campaign of thousands of hyper-volumetric DDoS attacks at never-before-seen rates.
In 2023, Cloudflare said it mitigated over 5.2 million HTTP DDoS attacks consisting of over 26 trillion requests.
“Despite these astronomical figures, the amount of HTTP DDoS attack requests actually declined by 20% compared to 2022,” Cloudflare wrote.
On the other hand, the network-layer DDoS attacks – comprising of IP packet-intensive and bit-intensive attacks – surged.
“Our automated defenses mitigated 8.7 million network-layer DDoS attacks in 2023. This represents an 85% increase compared to 2022.”
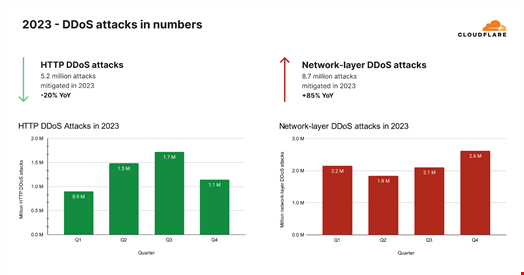
In Q4, Cloudflare observed a 117% year-over-year increase in network-layer DDoS attacks, with specific targeting of retail, shipment and public relations websites during and around Black Friday and the holiday season.
The largest-ever DDoS attack occurred during the third quarter of 2023, with 201 million requests per second (rps) –almost eight times more significant than the previous record of 26 million rps, reported in 2022.
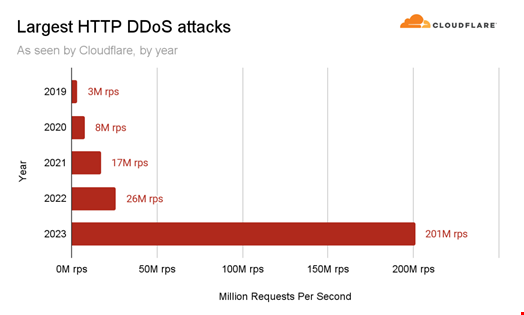
Additionally, the sophistication of DDoS attacks in 2023 was unprecedented, with some exploiting vulnerabilities in the HTTP/2 protocol, the second major version of the standard protocol for data communication on the web.
Rise in Israel-Palestine and Taiwan-Related DDoS Attacks
Other findings from Cloudflare’s DDoS attack report include:
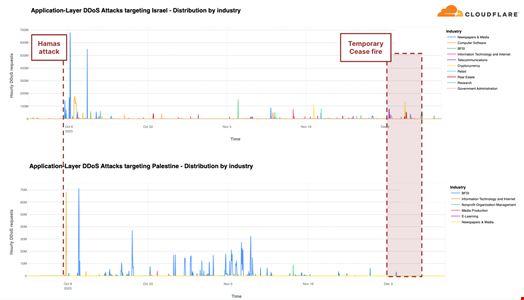
- An increase in DDoS attack activity related to the Israel-Hamas war, with DDoS attack traffic targeting Israeli websites growing by 27% quarter-over-quarter, and by p 1,126% quarter-over-quarter for the traffic targeting Palestinian websites.
- An increase in DDoS attacks targeting Taiwan-related websites, with Q4 2023 registering a 3,370% growth compared to Q4 2022
To put together quarterly data on DDoS attacks, Cloudflare automatically surveys each attacked customer on the nature of the attack and the success of the mitigation.
Over the past two years, Cloudflare collected 164 responses per quarter on average.
