A surge of fake or stolen X (Twitter) Gold accounts has been flooding marketplaces and forums both on the surface web and the dark web over the past year, according to CloudSEK.
Threat actors have used multiple techniques to forge or steal X Gold accounts since Elon Musk’s firm introduced its new verified accounts program in December 2022.
This is according to a new report published by CloudSEK: Gold Rush on the Dark Web: Threat Actors Target X (Twitter) Gold Accounts.
Twitter Gold, later X Gold, labels the account of a verified organization on the social media platform.
It was introduced alongside Twitter Blue, now X Blue, a checkmark that can be bought by any user to certify their account is premium, and Twitter Grey, now X Grey, to identify public organizations and NGOs.
How Do Threat Actors Get Hold of Fake Accounts?
CloudSEK identified the first advertisement for a Gold account on dark web marketplaces in March 2023.
Since then, the firm has observed a flood of X Gold account ads on the dark web, alongside fake or stolen Facebook, Instagram, Yahoo, and TikTok accounts.
Cybercriminals selling those accounts use several methods to acquire them, including:
- Manually creating fake accounts: the advertisers manually make accounts, get them verified, and are ‘ready to use’ for their buyers. This is ideal for criminals who need pseudo-identity and do not want to be attributed to their actions, according to CloudSEK.
- Brute-forcing existing accounts: cybercriminals take over an existing account by users using a generic username and password combo list. The tools used to do this include Open Bullet, SilverBullet, and SentryMBA.
- Using malware to harvest credentials and steal accounts: infostealers have a centralized botnet network where credentials from infected devices are harvested. These credentials are then further validated according to buyers' requirements, such as individual or corporate accounts, number of followers, region-specific accounts, etc.
Up to $500 per Fake Gold Account
Prices for fake or stolen accounts ranged from around $0.30 for a new X account without a checkmark to around $500 for a Gold account.
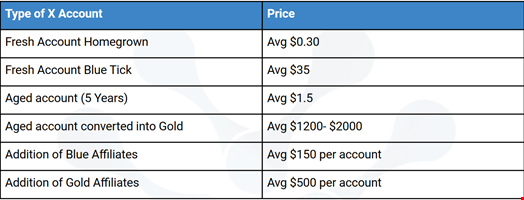
All purchases are conducted through a middleman, who ensures the genuineness of the accounts from sellers and funds from the purchaser.
“Such advertisements also allow multiple opportunities for cybercriminals to become a guarantor of the deals since large amounts are involved. Additionally, such accounts are resellable, enabling a whole reseller market behind compromised accounts,” CloudSEK researchers wrote.
Risk of Phishing and Reputation Damage
A hacked or compromised social media account can be exploited to spread phishing campaigns. It also can be used to damage the reputation of the owner of the original account.
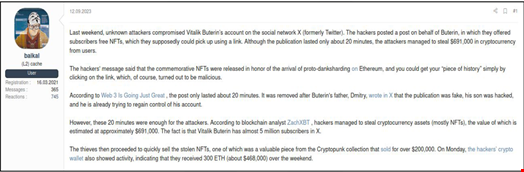
In its report, CloudSEK provided the example of the Ethereum blockchain and cryptocurrency co-founder, Vitalik Buterin, whose X account was compromised in September 2023.
The perpetrators seized control of Buterin's profile and exploited his large following by posting a deceptive message offering free non-fungible tokens (NFTs) to unsuspecting users.
The malicious link embedded in the tweet directed users to a fake website designed to drain cryptocurrency from their wallets. Despite being active for just 20 minutes, hackers managed to siphon off a staggering $691,000 digital assets before the fraudulent post was removed.
CloudSEK’s Recommended Mitigation Measures
According to CloudSEK, there are two ways in which organizations can ensure that the X Gold account campaign does not impact them:
- Ensuring that the dormant accounts are closed if they have been inactive for an extended time period
- Having an alerting system in order to be warned of stolen corporate social media account credentials and password protection practices
“Typically, credentials are stolen by malware due to the employees' lack of best security practices. Employees should be trained and educated on workplace cybersecurity practices. Password policies should be updated, such as replenishing the account passwords regularly. Employees should be educated against the use of cracked software and its dangers,” CloudSEK concluded.

