Security experts are observing attempts to exploit the remote code execution (RCE) vulnerability CVE-2023-22527 affecting outdated Atlassian Confluence servers.
The company disclosed the flaw last week, specifying its impact on Confluence versions released before December 5 2023. It also provided a patch for versions 8.5.4 (LTS) and later.
The critical severity flaw allows unauthenticated, remote attackers to execute code on vulnerable Confluence Data Center and Server endpoints (versions 8.0.x to 8.5.3).
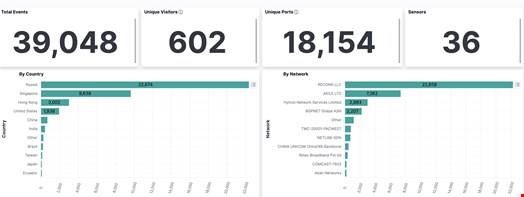
Writing yesterday on X (formerly Twitter), security experts at Shadowserver reported over 39,000 exploitation attempts originating from 600 unique IP addresses, primarily Russian.
Attackers would be executing the ‘whoami’ command for access and privilege information. The total number of accessible Confluence instances is 11,100, but not all run a vulnerable version.
“The method of exploitation is noteworthy, as malicious actors can weaponize various channels, such as emails, URLs or social media posts, to deliver the exploit,” explained Sarah Jones, cyber threat intelligence research analyst at Critical Start.
“The simplicity of the attack vector means that a single click from an unsuspecting user is all it takes to introduce harmful code into the system. Compounding the issue is the availability of exploits online since January 2024, making them accessible even to less skilled attackers.”
For context, Atlassian Confluence vulnerabilities are commonly exploited by various attackers, including state-sponsored and ransomware groups.
“Confluence Data Center and Confluence Server endpoints are used by organizations that have sensitive content they don’t trust in the cloud, which can include code, secrets, architecture diagrams and the like,” commented John Bambenek, president at Bambenek Consulting.
“If I wanted to see the building blocks of architecture for organizations to plan out crippling ransomware attacks, Confluence is my first stop. What makes this more impactful is that as a result of the hybrid workforce, many of these instances are internet-facing, allowing employees to work from home for organizations without a hard VPN access requirement.”
Read more about similar attacks: Critical Atlassian Bug Exploited in Ransomware Attacks
In its advisory, Atlassian confirmed it could not provide specific indicators of compromise for CVE-2023-22527. Regardless, administrators should update Confluence instances released before December 5 2023 and treat outdated ones as potentially compromised, conducting thorough cleanup and updating to a secure version.
