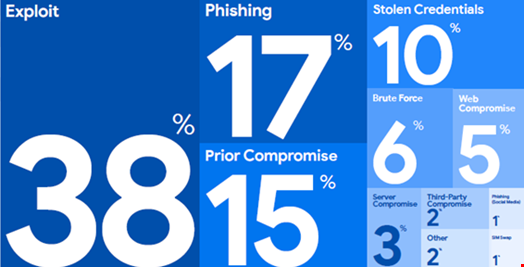
In a move away from traditional phishing scams, attackers are increasingly exploiting vulnerabilities in computer systems to gain initial network access, according to Mandiant’s M-Trends 2024 Report.
In 2023, attackers gained initial access through exploiting vulnerabilities in 38% of intrusions, a 6% increase from the previous year.
Mandiant also found phishing’s prevalence declined from 22% of intrusions in 2022 to 17% in 2023. However, it was still the second most common initial access vector assessed by Mandiant.
Zero-Day Vulnerabilities Actively Exploited
Researchers observed 97 unique zero-day vulnerabilities exploited in the wild in 2023, up by 56% compared to 2022.
Chinese cyber espionage groups were the most prolific attackers to exploit zero-days, primarily for the purposes of intelligence gathering and strategic advantage. Vulnerabilities that are unknown to software vendors can provide long term access to systems and sensitive data.
Additionally, financially motivated cybercriminals continued to utilize zero-days to infiltrate systems and steal financial data. This includes a group tracked as FIN11, which frequently targets file transfer applications that can provide fast access to large amounts of sensitive data.
The most frequently targeted vulnerability observed by Mandiant in 2023 was CVE-2023-34362, a high-risk SQL injection vulnerability in MOVEit Transfer.
This was followed by CVE-2022-21587, a critical unauthenticated file upload vulnerability in Oracle E-Business Suite.
In third place was CVE-2023-2868, a critical command injection vulnerability in Barracuda Email Security Gateways.
Stuart McKenzie, EMEA Consulting MD at Mandiant, a subsidiary of Google, noted phishing is now often used to steal credentials for later credential-based attacks rather than to deploy malware.
This is partly a result of improved security tooling that protects users from receiving malicious email messages.
The shift towards software vulnerability exploitation requires a more sophisticated approach by attackers compared to traditional “spray and hope” phishing attacks.
Zero day and n-day vulnerabilities, which are either not discovered or patched, allow attackers to pick and choose how they target organizations at their leisure.
McKenzie said: “If you’ve got time on your side, you’re able to deploy those against any organizations when you want to.”
Ransomware Drives Down Dwell Time
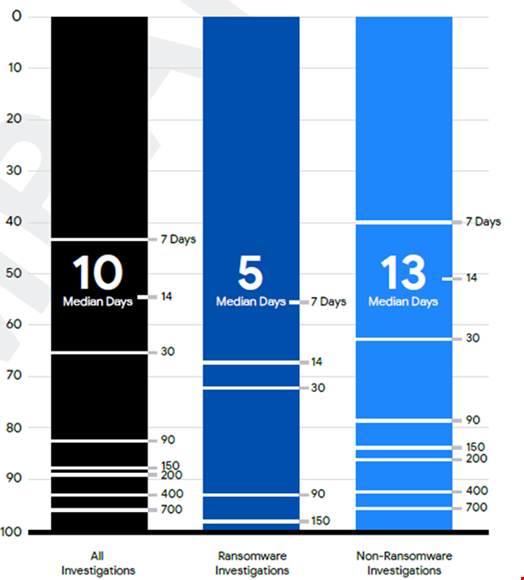
Attacker dwell time – the period from compromise to detection – fell to just 10 days in 2023 from 16 in 2022, Mandiant found.
While this demonstrates advancements in detection capabilities, Mandiant cautioned that the growth in ransomware attacks in 2023 helped drive down dwell time as the threat actors wanted their presence to be known to launch extortion negotiations.
For example, for ransomware-related intrusions, 70% of organizations were externally notified, mostly by the attackers.
McKenzie explained: “We see a lot more cybercriminals interested in ransomware. For a ransomware attack to be successful, they need to organization to know.”
The median global dwell time for ransomware intrusions was five days in 2023, which compares to 13 days for non-ransomware intrusions.
The proportion of global investigations involving ransomware increased by five percentage points to 23% last year compared to the 2023 M-Trends report.
Despite this, Mandiant found many attackers are focusing on evasion to maintain persistence on networks for as long as possible. This is particularly the case for those targeting data theft or nation-state groups.
McKenzie noted threat actors are moving away from targeting endpoints due to significant improvements in endpoint detection and response (EDR). Therefore, they are increasingly targeting edge devices, such as routers and email gateways.
“Not many companies have detection capabilities there, so the attackers move to where they can be most successful,” said McKenzie.
Over 4000 Threat Groups Tracked by Mandiant
Mandiant revealed that it tracks more than 4000 threat groups, 719 of which were newly tracked in 2023.
A high proportion of the groups tracked are designated as uncategorized (UNC). UNC means that new threat activity encountered cannot confidently be linked to an existing group.
Over half (52%) of the groups tracked by Mandiant in 2023 were primarily motivated by financial gain, up from 48% in 2022, while 10% principally pursued espionage activities.
Just 2% were judged to be operating for hacktivist motivations. In 36% of threat groups, a specific motivation could not be determined.
The increase in financially motivated groups is partially explained by the growth in ransomware-related activity, the researchers said. Of all financially motivated intrusions tracked by Mandiant, ransomware made up almost two-thirds of cases.
McKenzie observed that attributing attacks to particular groups is becoming harder due to the complex cybercrime ecosystem, with many incidents now involving multiple actors.
“We’ve seen such a change in the lifecycle between the initial access, onto the access brokers, onto the criminal group – it’s no longer a single flow,” he noted.
Ransomware-as-a-service (RaaS) groups also have a number of affiliates using their tooling, further complicating the picture for threat researchers, McKenzie added.
In a separate report published on April 17, Mandiant announced it had upgraded the Russian state group known as Sandworm into a named Advanced Persistent Threat (APT) group, APT44.
This is due to the scale of the group’s cyber activities targeting Ukraine since Russia invaded the region in 2022.
