APTs are running circles around most organizations’ defenses. The good news is that anticipatory active defenses can be remarkably effective in compensating for our weaknesses as we wage battle
Today’s nation-state actors have virtually unlimited funding (courtesy of tax payers); armies of people; direct access to the internet backbone; government sponsored/mandated backdoors in critical systems dating back decades; and supply chain infiltration dating back to at least the 80s.
Their tentacles entwine the global telecommunications infrastructure. They have almost incomprehensible computing power; a seemingly never-ending supply of zero-day exploits to gain privileged remote access; key loggers; and RAM-scrapers that scrape decryption keys and passwords directly from memory.
They ‘pass-the-hash’ and ‘pass-the-ticket’ to bypass passwords entirely. They impersonate our Windows Active Directory security access tokens (SATs) to bypass even the strongest of authentication methods. They wield the most advanced malware in existence, designed to handily bypass endpoint security solutions; and they control our systems and exfiltrate our secrets via covert command-and-control channels specifically engineered to bypass next-gen perimeters.
Often viewed as heroes by their countrymen, they are in many ways mere criminals and thieves, operating above the law, obscured behind force fields constructed by the same governments who employ them, with virtually no risk of direct consequences for their crimes.
We IT pros often commiserate about our struggles to implement effective security within our organizations, but APTs have no sympathy for our challenges and frustrations. They know we struggle; they’re counting on it. They know application whitelisting in full lockdown is hard to implement. They know passwords are the bane of security. They know most organizations aren’t even close to fully implementing the Critical Security Controls, and they know social engineering works. So they relentlessly and methodically seek out our weaknesses and exploit them without mercy. If we fail, they win. It’s that simple.
I have spent over 20 years studying how hackers do these things. I am fascinated by it. I have traveled the world emulating these techniques on real-world production systems in huge organizations to see how well their defenses actually work. I have written about it. I have spoken at dozens of conferences about it. I have written courses about it. I have taught thousands of IT professionals about it.
So what have I learned? In a few words, they are going to get in and they are going to hunt your administrators. Plan on it.
Organizations need anticipatory, active defenses designed to frustrate, annoy and deceive advanced adversaries (and insiders) who have already achieved access to their innermost sanctums.
This may sound like yet another unattainable goal, but herein lies the real power of active defenses. They are often remarkably simple, they are often easy to implement, they are often free, they often cause little to no impact to production systems, they often require very little support from leadership and other staff, and most importantly – they can be incredibly effective.
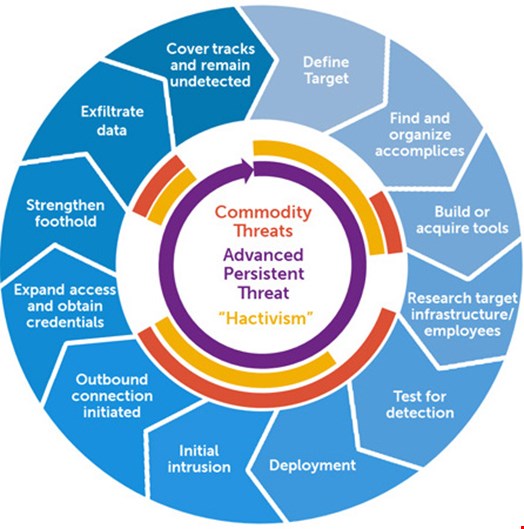
How can this be? The key to active defense is understanding how APTs operate and what they are targeting. They are not ghosts. They are going to have to do certain things once they’ve gained a foothold. They are after certain things. The APT attack cycle diagram (above) is an excellent high-level overview that provides us a framework of actions we can anticipate and work to deliberately disrupt with active defenses.
Here are a few very simple examples:
- Honey Hostnames – Create simple DNS records with interesting hostnames (eg jumpbox01, admintools, research, accounting, contracts, zeus, sharepoint, etc) Get creative and watch them come. When they resolve it, you get alerted.
- Honey Accounts – Create interesting accounts in Windows Active Directory, on Unix servers, routers, switches, virtual machine consoles, cloud services, and other systems that have no production purpose but that would attract an attacker’s attention. When they attempt to login, you get alerted.
- Honey Hashes – Knowing that attackers scrape hashes out of RAM to use in pass-the-hash attacks, we can load fake hashes into memory using the RunAs command or PowerShell and alert when anyone attempts to login with the account anywhere in our environment.
- Honey Password Manager – Encrypted password manager files are big APT targets. Work with your admins to create fake password manager files. Place them on admins’ desktops and tell them never to open these files. Configure alerting and you’ll know if someone’s on their workstation that shouldn’t be, even if they’re operating within the admin’s user context.
- Honey Docs – Place interesting files in just the right places and watch for access attempts. This is a simple yet incredibly effective alerting mechanism for APTs and insiders looking where they shouldn’t be looking.
Disrupting APTs with anticipatory active defenses might just be the missing link in your defensive strategy.
About the Author
Bryce Galbraith is a principal instructor and author for the SANS Institute. He teaches several of SANS’ most popular courses and is the lead instructor for the SANS SEC550: Active Defense, Offensive Countermeasures and Cyber Deception course. He has taught thousands of IT professionals around the globe.
