It’s not a question of if but when – as a CISO, you will be called to brief the board of directors on cybersecurity performance - and with growing pressure from the board, this day is probably coming sooner than expected.
The meeting will probably come with a short time window to tell your story. Like any good presenter, the first rule should be “Know Your Audience.”
Many CISOs come from audit or IT backgrounds and haven’t had to think in board-level terms. Their focus is primarily tactical, with a never-ending battle to secure the organization from cyber threats and stay in compliance with frameworks and regulatory requirements.
A board’s point of view is different: it is their responsibility to provide oversight of risks and make sure the company is equipped to handle them. Cyber risk has emerged as one of the top risks to the enterprise so CISOs are being asked to report more frequently to the board. Questions you can expect to hear from the board are:
- How much risk do we have?
- What are our top risks?
- How is our risk posture trending – improving or degrading?
- Are we spending too much or too little?
- What is the cyber risk associated with a new business initiative?
Then comes the second key point to knowing the audience of the board. The typical profile of a director is a former business executive who has led a variety of operational functions and has an orientation toward financial metrics. In rare exceptions, a company may have a board member with a more technical background to add to the skill set around the table – but don’t count on it. That’s the bottom-line focus for reporting to the board: risk-based and financially expressed.
Let’s be candid. Typical CISOs can’t answer the questions above in financial terms. Discussions of the status of threats and vulnerabilities are technical talk disconnected from business impacts—they might imply that risk is reduced by better controls but that’s just guesswork. The same goes for answering the question about how much to spend on security—looking to industry norms for spending levels just guarantees meeting industry norms, not a return on investment in demonstrable risk reduction.
So how do CISOs explain the impact of cyber events on the bottom line as well as the effectiveness of their cybersecurity initiatives? Cyber risk quantification is enabling a completely new way of communicating and reporting on risk.
Using the financial data that’s available from inside your organization on, like the value of assets or the costs of response/remediation and your security data on frequency of attempted and successful attacks, you can conduct a quantitative risk analysis and articulate risk in financial terms, a language that board members understand well.
Chart 1 (Risk reduction comparison. Source: RiskLens)
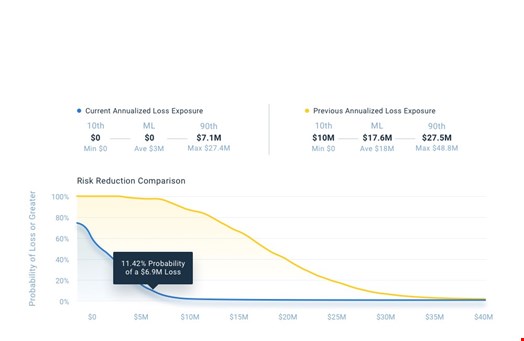
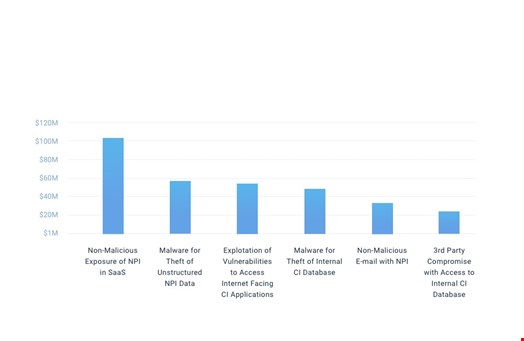
The output of quantified cyber risk analysis can be expressed as a bell-curve or a loss exceedance curve, showing the probability of incurring certain amounts of losses, given the threats the organization faces and the current controls (see chart 1). If you take the most likely figures for your top risk scenarios, you can display your top risks side by side and explain where cyber risk is concentrated and where more attention is needed (see chart 2).
Chart 2 (Top Risk Report. Source: RiskLens)
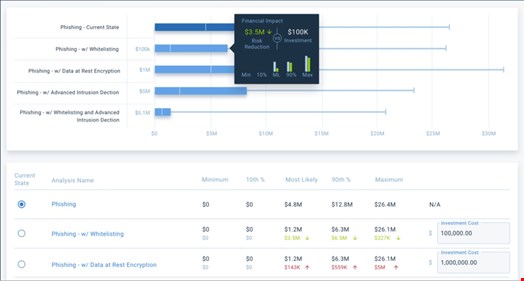
Where it becomes even more interesting for a board audience, is to show the likely reduction of risk following the implementation of a CISO's security strategy or of a particular control. It becomes most exciting if the CISO can factor in the cost of the cybersecurity investments and show the possible ROI (see chart 3).
At that point, CISOs can compare multiple risk mitigations and recommend the best cost-benefit option. That's a language that the board and the business understand.
Chart 3 (Cost-benefit report. Source: RiskLens)
Cyber risk quantification also supports an important board function, helping directors in their risk oversight role, which includes setting and approving clear, quantitative and actionable risk appetite statements for the various forms of loss and then assessing how well the organization is managing risk against those objectives.
The most sophisticated cyber risk management teams are beginning to inform their boards with dashboards that track key risk indicators. Having established which are the top cybersecurity risks to the organization in financial terms, analysts can run simulated scenarios that tweak the inputs to identify the key factors that contribute relatively more to risk.
For instance, how does our risk posture stand if the volume of attacks goes up or we fall behind on software security updates? The dashboard can visually show the board how security is trending vs. risk appetite.
Dashboards, key risk indicators, ROI on security projects – this is a different level of communication than CISOs have been able to offer boards before. Cyber risk quantification empowers boards to be an integral part of strategic decision-making for cybersecurity and allows CISOs to make their support case in the bottom-line language the board wants to hear.
