
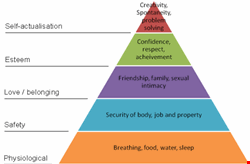
Abraham Maslow, a psychologist working in the mid-20th Century, neatly explained that success in life is built on layers of dependent needs, with physiological ones at the bottom and self-fulfilment at the top. This is illustrated in Figure 1.
In order to reach the dizzy heights of living a complete life, the previous layers of esteem, belonging and love, safety, and physical needs must be met.
So what are the parallels for security management? If a security service is working to its full potential, then what does that look like? I would like to use this psychological concept to explore various ways of slicing and dicing security principles. My goal is to give useful insight into how security can be understood and managed.
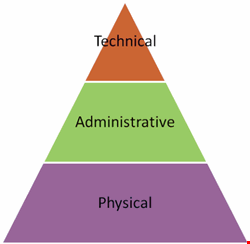
One simple idea is to layer physical, administrative and technical control types in order of dependency. For example, it could be argued that physical security is an absolute basic requirement for protecting corporate information. What’s the point of intrusion prevention systems for the network if the computer room door is left open? Layered thereon are the administrative policies, standards and procedures that oil the wheels of security management. Finally, technical controls sit upon the other two control types to complete the picture (see Fig. 2).
One benefit of using this approach is helping technically focussed security teams always consider the physical and administrative aspects of security first, before deploying technical solutions.
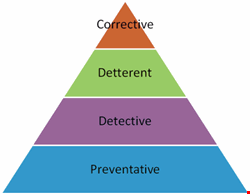
Another option is to design a hierarchy triangle for the control groups – preventative, detective, deterrent and corrective. It can be argued that a measure to stop a bad thing from happening is better than one that picks up the pieces after the event. Therefore, preventative controls, such as proximity cards, could be considered a basic need. Layered on top of this are detective controls that identify when bad things are happening (e.g., CCTV). Deterrent controls, such as a warning sign, complement the other controls but have a very limited effect if they are used in isolation. Finally, a corrective control (e.g., incident handling procedure) can help get things back to normal following a break-in (Fig. 3).
This model presents the different levels of strength for each control group – the bottom layer is the most effective, whereas the top layer only has a benefit when the layers beneath are evident.
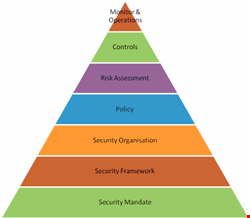
This is where I nail my colours to the mast and present ‘Clayton’s Hierarchy of Security’. This model can be applied to organisations of all shapes and sizes. However, each layer will be handled formally or informally depending on the nature and culture of each business (Fig. 4).
Security mandate
The first, most fundamental need of security is the mandate from senior management that security is important and will receive funding. Without this, security will not even get off the ground. This could be indicated by a formal board-level commitment in a large organisation, or via an email from the boss in a small company.
Security framework
The next layer up is to identify and work toward an appropriate security framework. This gives an organisation the blueprint to develop a complete security service. A small company may adopt general practice as their framework; that is, doing what everyone else does.
Security organisation
Third, a security organisation needs to be established to manage the security service. For a large company this usually includes roles such as board-level sponsor, CIO, CISO and other positions of responsibility across the business.
Policy
The first thing that this organisation will produce is the high-level information security policy. This details the overall aim, objectives and commitment of senior management, as well as identifying those roles with key responsibilities. This may be, informally, a quick email from the owner telling employees that company information must be kept confidential.
Risk assessment
With limited funds, resources and time, the security organisation then needs to understand what it needs to protect and what to defend against. This is where risk assessment comes in. It’s a very useful tool for understanding what bad things could happen, the chances of them happening, and what damage would be caused if they became reality. The two-man band may instinctively do a risk assessment to decide what protection to put in place. For example, it may decide that its intellectual property is the most important data it holds and, therefore, must be protected at all costs.
Controls
Once the risks have been suitably identified, the appropriate physical, administrative and technical security controls can be deployed to mitigate those risks. Larger organisations may have a documented security plan that details all the different types of controls and how they mitigate each identified risk.
Monitor and operations
Finally, when all the previous layers are in place, the security controls can be monitored and maintained to ensure that they are working as planned.
Managing security can be a complicated and difficult experience. Utilising ideas and concepts from other disciplines, such as psychology, can help security professionals understand the context in which they operate and provide illustrative tools to deliver appropriate and informed security management.
Alex Clayton, CISSP, is the security and continuity manager for private equity firm 3i. He has experience in the central government, financial services, and education sectors as both a security consultant and IT project manager.