
Have you ever considered taking a role as the most senior person for information security working at a large corporation? If so, then you must be prepared to understand the key principles of information security – and how they really apply to life and business.
The myths of the CIA triage
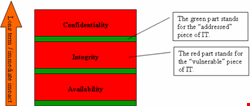
Yes, we all understand the typical C-I-A triage (written in this sequence because it’s so easy to remember with the three-letter agency acronym), where C stands for confidentiality, I for integrity, and A for availability. However, what I have realized and seen among many people during my professional life – people who are well-educated about security and who are really committed to keeping secure the information of the company they are working for – is that many overstate the importance of confidentiality.
Sure, I don’t need to tell you that confidentiality is, in fact, important. But, if you really think about it, then what is the true business impact if some confidential information leaks? It certainly depends on the specific circumstances. Has intellectual property been compromised? Have marketing plans been shared with another sales department? Or even price lists? Has a major planned acquisition become public knowledge, and suddenly the stock price of the acquisition target has gone through the roof?
Maybe you will have to deny any such plans, wait until the stock price has normalized, and perform the acquisition at a later date. Perhaps your organization will sue the thief who stole and/or used your intellectual property. Will you take a leap of faith and make your clients aware of unfair business practices by your competitor, which is using the price information. Regardless, the immediate (please note the emphasis) business impact in most cases is not as high as you may have thought.
Even after a competitor has gained the extra knowledge that may take away your competitive edge (and there are, in fact, fair-playing competitors that might give it back to you without using a copy of it), until this arrives into your balance sheets, months and years can go by, and you will have time to respond and act.
But now, imagine a change in your perspective and realize why IT is used today in almost all businesses, industries, and organizations of any size. And keep in mind that the availability of your IT systems and data is of utmost importance. Let’s say your major ERP system goes down for a day or two, or even for a week. What kind of outcry would there be from the business? Would there be any board room attention, and would guaranteed extra money be available to fix the issue immediately?
It is this kind of ‘breach’ that has an immediate, measurable, and direct loss, which impacts – or in the worst case interrupts – a companies’ ability to make money. You will be amazed that suddenly there is no more RO(S)I discussion or budget restrictions. Everyone up to the board level will immediately understand that this kind of loss needs action, because it is a direct function of a company’s stability and, even, existence. There is enough material publicly available on the internet proving this fact that I don’t need to repeat it here.
Once you have tended to the availability needs of your system, the next most important security parameter is integrity. Yes, the systems and data must not only be available, they must, in fact, store and produce reliable and integer data that allows for good business decision making, correct financial reporting (Sarbanes-Oxley 404 etc.), and proper forecasts.
A single integrity fault is not as bad, and it will be (under typical circumstances) quickly recognized. Your company should have procedures in place to verify and ‘guarantee’ integrity. However, going back to the previously described model, you realize that any impact on your data and system integrity will have an effect within the near term, at the latest during your next SOX audit (or SEC trial for that matter), but it can be as early as your next sales proposal getting rejected because of wrong price information or bad contact data. Several integrity faults (following the Gaussian error propagation rule) will create an even bigger and (time-wise) earlier business problem, so I think we can agree on the point that the integrity parameter becomes number 2 on the immediate business impact scale.
Number 3, as mentioned, is confidentiality. And don’t think it is not important – there are enough cases out there that prove this assumption wrong. GLBA, PCI, HIPAA and other regulations and standards all provide for security, including confidentiality or ‘privacy’. Recent data breaches and the growing publicity due to adopted rules in almost all of the states and several other countries, which require ‘going public’ (where it hurts companies the most), have all shown that it is good practice for corporations to secure confidentiality. To do so would be in their own best interest.
The best you can do is to understand that all three of these parameters are in fact important, and you should address them all by building your information security system from the ground up (see image).
The exponentially growing threat surface
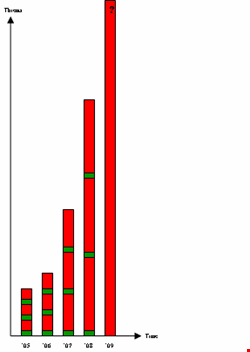
Now let’s make this a bit more complicated and recognize that the threat space (call it vulnerabilities if you’d like) is growing almost exponentially every year, for more than the last 20 years. (Remember the internet [or Morris/MIT] worm of 1988?) This means we deal with a ‘moving target’ – a continuously growing attack space without an increase in the green space (see image).
Recent industry studies from leading providers such as McAfee, Symantec, and Verizon clearly show this picture. For those who think this is all sales and marketing rumor, the number of actual data breaches is very much in sync with this increase in attack space. The latest numbers for 2008 show that more than 290 million records were breached. Why is this? Why can’t this problem be easily solved? And why do more and more companies struggle with the problem of data breaches?
The magic triangle of information security
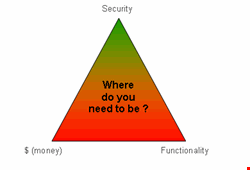
We all know (or should know) the magic triangle of the financial world – the one that shows there is a difference between liquidity, security (of assets), and profitability of an investment. You cannot accomplish all of these aspects but have to instead decide what your goals are (cash, gold, or gain). So here is my advice, based on more than 20 years of experience in the IT and security world:
There is a similar, inherent structure for information security, as shown in the triangle (see image). In the ‘pre-data breach era’ of IT, the normal discussions between IT and the business side went along the (one-dimensional) line between desired functionality and the required money/investment to achieve the stated goals. Security was almost never part of the decision-making process, and vendors and software companies are guilty of not addressing this properly. Although a lot of effort is put into this area, simply look at the amount of security patches alone for the large vendors in the field. It will take years, if not longer, until we will see a real paradigm shift, and only if IT security professionals ask the necessary questions before we purchase something: Is this thing providing the right quality (security)? Is my company or personal data secure when I use this stuff?
Now, we have to add another dimension to the equation, and that is simply: security. In many if not all cases, security is opposite to over-boarding functionality/convenience. You have to go the extra miles of: assigning roles and access rights; limiting the broad functionality options to just those who ‘need to know/have’; defining unique IDs; taking away administrative rights from those who don’t have a very solid reason to have them; blocking the large majority of attachments from emails; reducing internet access/restricting website access and time; adding antivirus software (anti-spy, anti-malware); doing backups; DR/BCP; creating firewall rule bases (with ‘deny all [other]’ approaches); requiring complex and long passwords (people really appreciate your efforts here); and doing similar stuff that’s not necessarily convenient.
Security efforts often require resources, people, time, and leadership. Who wants to spend money on something they can’t see and that has not happened (yet)? All that wonderful security infrastructure (outsourced, hosted, managed, or operated in house, regardless) comes with a big price tag, and the question is: How much security is enough? To answer this question, you must talk with the business owners – those who make the money decisions. Make them aware of all the dimensions inherent within any information security operation, and get a commitment as to what kind of risk they are willing to accept. Remember, you don’t want to be the most secure place on earth – you just want to be secure enough to make others a more attractive target. Hackers are smart, but also lazy. They strive for the easy prey in most cases. You want your organization’s systems to remain in business; otherwise, your security model stinks.
Michael S. Oberlaender, MS, CISSP, ACSE, GSNA, is a former global senior IT and security manager with more than 20 years of experience and education in physics, math, and computer science. He has worked for large international corporations in the US, including FMC Technologies and Heidelberg Americas, as well as Suedzucker AG and several others in Germany. Oberlaender most recently served as CISO of FMC Technologies.