As 5th generation telecommunication infrastructure continues to rollout in trial and steady-state phases globally, there has been a growing focus on new cybersecurity risks that are being introduced into operator environments. Compared to legacy telecom systems, the 5G backbone will rely heavily on Network Function Virtualization (NFV) and Software-Defined Networking (SDN) to enable greater flexibility for management of services.
NFV can be described as a technology that allows traditionally hardware-based processes to run and be configured in virtual machines—reducing reliance on single-purpose physical equipment. SDN, on the other hand, enables high-level and centralized control over this virtual environment, where control and data planes are operated and administered separately. While significant operational and cost benefits are offered by this NFV-SDN utilization, telecom providers must also consider new firewall configuration challenges and the rapidly evolving threat of malicious code propagation across the network control plane.
Firewall Configuration Challenges
In a distributed 5G environment, core network resources will need to peer into deployed customer premise equipment to collect real-time information. This allows operators and control tools to properly utilize the flexibility of a virtual architecture. However, a presentation by researchers at Clemson University and Arizona State University highlight how firewall configurations in an SDN-NFV environment are posing unique risks. The presentation notes that since a centralized SDN firewall enforces policies at the environment’s controller, limitations for managing granular and partial violations emerge as packets traverse a network.
For example, according to SolarWinds Inc., networks with a centralized SDN firewall may lean towards using a stateless configuration to reduce the compute resources needed at the control layer. Compared to a stateful solution, a stateless approach utilizes static port source/destination data and basic connection information. This is not without drawback, however, as a stateless tool is more susceptible to an attacker conducting a multi-hop attack. It is also possible for an attacker to evade firewall restrictions via crafted packets aiming to reach internal network components that iptables or access control lists should deny. This technique has been proven in the wild, seen with CVE 2012-2663.
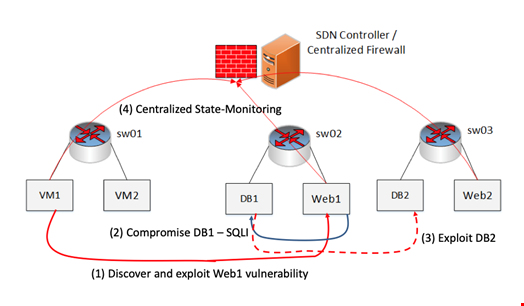
Alternatively, if the telecom provider decides to provision a stateful firewall solution for a customer’s environment at the control layer, there is a real risk of network resources becoming quickly overwhelmed. A paper published with Xplore research database highlights how centralized and virtualized functions at the control layer, including firewalls, can be susceptible to a type of DoS attack called a control plane saturation attack. Since stateful processing will utilize Deep Packet Inspection (DPI) or end-to-end traffic stage analysis, an attacker can drive IT resources away from business processes at a significant rate or slow the overall target network’s performance—shown in the image below. In short, while stateful firewalls in an SDN-NFV environment are better at identifying unauthorized and forged communications, they may reduce control layer relay efficiency and create other security risks.
Malicious Code Propagation at the Control Layer
If there is improper isolation between hypervisors and NFV components, an attacker can feasibly access the underlying hypervisor management API that is supporting the OS instance. In practice, this could occur if an attacker sent crafted network packets to exploit a buffer overflow vulnerability, resulting in the execution of malicious code on the hypervisor. The attacker can then escalate operations on the host or traverse to a different virtual instance also interacting with the same hypervisor.
A paper published from the 2016 Network Softwarization workshop hosted by the Institute of Electrical and Electronics Engineers (IEEE) reveals that there are numerous proof-of-concepts for remote code execution on hosts via malicious virtual machines. A real-world implementation of this scenario was published as a Microsoft Security Bulletin, MS15-068. The vulnerabilities outlined in MS15-068 could allow remote code execution where a specially crafted application is run by an attacker masking as a privileged user on a machine hosted by Hyper-V. The bulletin notes that, “Systems where Windows Hyper-V is installed are primarily at risk,” and that other network components integrated with Hyper-V’s hardware virtualization instances are at risk as well. Rapid7, a security software company, notes that as recently as April 2019 remote code execution vulnerabilities were discovered in Hyper-V—with that report referring to failed server-side vSMB packet data validation.
The malware and firewall examples demonstrate how attackers can target and exploit key software components specifically at the control layer of a virtualized telecom network. 5G service providers must implement new capabilities to defend against these attack vectors and prevent systems disruption or data theft. While many other security challenges exist, the two presented in this article highlight how the deployment of 5G communications—and subsequently a greater reliance on NFV and SDN technologies—will at the very least coincide with an evolving cybersecurity landscape with new mitigation gaps.
