The situation translates to a smorgasbord of opportunity for a hungry information-hijacker, but one which could soon turn into an all-you-can-eat buffet. The study, carried out by Emedia and provided to Infosecurity on an exclusive basis, investigated a wide range of businesses from 25 through to 5000+ PC users. The study found that while about half (52%) of those surveyed were currently using SharePoint, the other half planned to adopt the application once its social networking enhancements were live.
“This is a data leakage time bomb,” said security specialist and UK Accounting Standards Board member Steve Bailey. “SharePoint is a very widely-used medium, and it’s growing fast, so it is remarkable that IT-savvy users are disregarding the security implications. This could be down to complacency, confusion as to where the responsibility for developing such a policy lies, or simply lack of awareness.”
Whatever the root cause, he noted that in many organizations, SharePoint use has grown organically to “become part of the fabric of the business without being subject to mainstream security controls.”
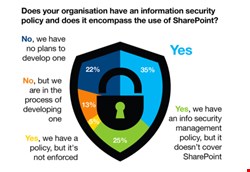
The employees themselves are part of the problem, but how to implement an IT policy that makes sense is a conundrum for many IT professionals – contributing to the lack of IT policy.
“Banning data sharing is not the solution – that’s both impractical and undesirable,” said Martin Sugden, CEO at Boldon James, which sponsored the study. “In fact, refusing to share data is inefficient and potentially dangerous. What’s important is striking the balance between the need to protect information and the need to share it.”
The survey concluded that a protective marking solution for labeling the data's level of sensitivity needs to be implemented. Many government agencies use protective marking to minimize inadvertent disclosure of confidential information, while commercial organizations employ protective marking to control intellectual property or information containing customer data.
By clearly identifying sensitive information using a classification solution, it becomes easier to ensure that access control methodology is correctly connecting the right users to the right data, Sugden noted.
Yet the study discovered that 65% of respondents are not yet marking any of their data. A very low 9% of respondents said they protectively mark all emails, and the same percentage said they do the same for all documents. Only 17% of respondents said they mark all email and documents.
“When you consider that hundreds – and even thousands – of users could be accessing your SharePoint server, it makes sense to have a solid SharePoint security policy in place,” added Sugden. “[SharePoint] is a superb tool for creating routes into your data, but you can’t let your user group have unfettered access to data without giving them some method of understanding how sensitive it is – that’s why you have to label.
Steve Bailey warned, “Any business that relies on SharePoint to store sensitive or confidential data should always ensure that its users understand their responsibilities for the safe handling of that information. With the advent of BYOD this extends to employees and associates.”
He cautioned that recent high-profile breaches should serve as object lessons. “Otherwise we’ll have more examples such as the Police email that, according to the [UK's] Information Commissioner's Office (ICO) ‘contained 863 pieces of personal information’. Police accidentally sent the email containing the results of 10,000 checks with the Criminal Records Bureau (CRB) to a reporter when a staff member copied the wrong person into a message.”
| This article has been revised and corrected since oringially published. |