Every malicious campaign needs a robust supporting infrastructure, and attackers are constantly evolving new ways to improve availability and resilience.
Domain Generation Algorithms, Fast Flux Botnets, peer-to-peer protocols and anonymizers, are just few of the techniques that cyber-criminals have adopted to hide their command and control and malware distribution points. These techniques are all quite sophisticated, and add a level of complexity and operational overhead to any attack, bringing additional cost and eating into profits.
In addition, all complexity adds points of failure, and layered operational tasks are prone to errors. A final detraction for the malicious actor is the traces that these operational tasks leave, which can be used by security researchers to track the attackers.
Cybercrime is an industry, and like every business, it constantly looks for new ways to increase revenues and minimize costs and risks. So, what if the cyber-criminals could find a way to simplify the setup of their malicious infrastructures, using an available and resilient architecture that is able to bypass traditional on-premise security technologies, and is implicitly trusted by their victims?
Cloud Services; a Compelling Alternative to Host Malicious Infrastructures
Unfortunately, just as the good guys have embraced the huge benefits of cloud, the bad guys haven’t taken too long to realize that cloud services are also the ideal place to launch highly evasive malicious campaigns. Not only do they offer undeniable advantages in terms of simplified hosting, availability and resiliency, but they are also implicitly trusted by organizations and individuals, with the consequence that the same level of security enforced for traditional web traffic is not applied to many mainstream cloud services.
In fact, many organizations allow “trusted” cloud services to completely bypass traditional web security gateways. This sort of open door policy is completely inappropriate for cloud traffic which is both encrypted and nuanced (the same service can have multiple instances, for example a corporate and a personal account).
Cloud data analysis requires the ability to perform decryption at scale and an understanding of the context of the connection, and that’s exactly where legacy security solutions fall short because they were conceived for a web (where encryption was an exception) not driven by API.
Malicious actors are certainly aware of the holes in traditional security, and are working flat out to take advantage. Today, cloud apps account for 85% of enterprise web traffic, and 44% of cyber threats are now cloud-based, exploiting services like OneDrive, Google Drive Box, GitHub and Pastebin for criminal operations, both cybercrime and cyber espionage.
Recent Examples
Campaigns exploiting cloud services to distribute a malicious payload tend to adopt a hybrid approach, starting with a spear-phishing email that is used to deliver the link to the victim. This email sails through the email security gateway, and presents the user with a link to a familiar, apparently innocuous, service.
This technique was used in a recent cyber-espionage operation targeting Malaysian government officials. A state-sponsored actor used spear-phishing emails, sent from previously compromised addresses, containing a Google Drive link distributing the malicious payload.
A similar approach was adopted in another recent cyber-espionage campaign attributed to a politically motivated group, targeting organizations and individuals in the Palestinian territories. In this attack well-known services including Dropbox were used to deliver the malware, along with Egnyte, a less common collaboration and sharing tool which has recently joined the rogue’s gallery of weaponized cloud services.
Malware distribution is not the only way to exploit a cloud service. A recently exposed threat actor dubbed DRBControl has been targeting gambling companies since the Summer of 2019. This operation also used a spear-phishing link as the initial attack vector, but also used a cloud service (once again Dropbox) for its command and control (hence the name DRBControl, a shortening of DRopBoxControl).
If there has to be a top dog, however, cloud phishing is probably the most common example of how a familiar cloud app can be turned into an attack tool. In a cloud phishing attack, the SaaS (or IaaS) service is used to host a phishing page, tricking the user with both a legitimate domain and a legitimate certificate.
Office 365 and G-Suite are the preferred hosts for cloud phishing, probably because they offer multiple services. In case of Microsoft, we have seen examples of campaigns exploiting OneNote, Sway, SharePoint, and even Azure.
Cloud services let the criminals easily modify their payload during the operation (one of the advantages of simplified hosting), and are flexible enough to be used in multiple stages of the kill chain for both opportunistic campaigns and targeted operations.
Hacker humor, arrogance and contempt is not absent from these attacks. A recent example used a Google Form to mimic an Office 365 login page.
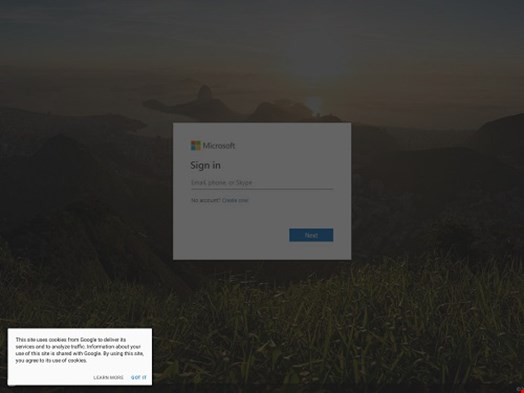
Cloud services are increasingly abused by cyber-criminals at multiple stages of the kill chain. They are cheap, easy to setup, reliable, and highly available.
Additionally, they are mistakenly implicitly trusted and often not subject to the same security policies of traditional web traffic. In order to cope with this new, cloud-native threat landscape, security technologies require a context-aware approach able to decrypt cloud traffic at scale, decode specific APIs, and enforce granular policies at both instance and activity levels.
