Today, the cloud is no longer a choice for businesses but an essential way to reduce costs, ensuring availability and no downtime factors are all in one package. Cyber-criminals eye those data highways, whether it's cloud computing, APIs, mobile, you name it; hacks are happening left, right and center!
Cloud service providers are responsible for the physical security of their data centers, and they are also responsible for ensuring that their systems are secure from attack.
More sensitive data is being kept in the cloud as organizations move from on-premises to cloud networks, which means security must be at the forefront. This information must be secured, but the cloud also introduces new problems that make security difficult.
Best Practices for Cloud Security Network
Cloud security is evolving with time as new developments appear, but certain best practices have remained consistent in order to safeguard cloud environments.
Organizations that already have cloud services in place or plan to implement them should look at these suggestions and tools to ensure that critical applications and data do not fall into the wrong hands.
1) Understand Your Shared Responsibility Model
In a private data center, the company is solely responsible for any security concerns. Things are far more complicated in the public cloud. One of the ridiculous myths that cloud data is secure is due to a misunderstanding between the responsibilities of a service provider and the cloud tenant. Simply put, it is:
- The cloud provider is responsible for the security of the cloud.
- The tenant or organization client is responsible for security in the cloud.
A great way of understanding the cloud services shared model can be found in this explainer image:
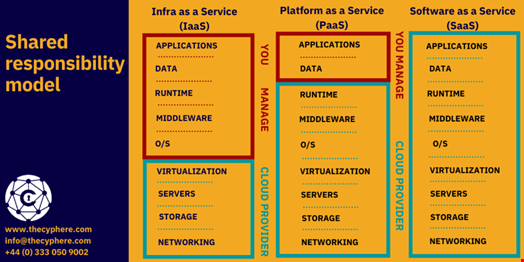
While the end-user is ultimately responsible for security, the cloud provider assumes responsibility for certain IT security components. The shared responsibility model is sometimes known as the buck stops with the cloud customer.
2) Ask Your Cloud Provider Detailed Security Questions
Organizations should also inquire about security measures and procedures that their public cloud vendors have in place when they engage with them.
It's easy to believe that the most popular vendors have security in hand, but security techniques and processes can vary significantly among vendors.
3) Deploy Identity and Access Management (IAM) Solutions
Unauthorized access was identified as the fourth most significant risk to public cloud security by CloudPassage's study (and increasing – 53%, up from 42% in 2020).
With different attacks, cyber-criminals' tactics for obtaining access to critical data becomes more sophisticated, such as utilizing cloud-based attack infrastructure, content delivery networks, domain fronting and other tricks. A high-quality IAM solution can assist defend against these dangers.
4) Train Your Staff
To prevent attackers from obtaining access credentials for cloud computing tools, organizations must teach all employees how to recognize cybersecurity dangers and how to respond.
Basic security knowledge, such as generating a strong password and identifying possible social engineering attacks, should be included in comprehensive training. In addition, topics like risk management should also be covered in the context of your organization.
5) Establish and Enforce Cloud Security Policies
Written rules that detail who has access to cloud services, how they may use them and what data can be stored in the cloud should be in place for all departments within an organization. They also need to spell out the specific security measures that staff must put in place to safeguard data and apps in the cloud.
Security personnel should be equipped with solutions like cloud access security brokers (CASB) to enforce cloud security policies to a granular level. In some instances, the cloud vendor may already include a policy enforcement tool that is sufficient for the organization's needs.
"Security personnel should be equipped with solutions like Cloud Access Security Brokers (CASB) to enforce cloud security policies to a granular level"
6) Secure Your Endpoints
Using a cloud service does not lessen the need for strong endpoint security; it increases it. New cloud computing projects provide an opportunity to re-examine existing cloud security strategies and ensure that current protections are sufficient to combat evolving dangers.
This is possible by asking for external/third-party validation to perform cloud penetration testing based on threat scenarios and assets, i.e., APIs, applications and infrastructure.
7) Encrypt Data in Motion and at Rest
Encryption is an important component of any cloud security plan. Not only should organizations encrypt all data in a public cloud storage service, but they should also ensure that data is encrypted throughout transit when it's most vulnerable to assaults.
8) Double Check Your Compliance Requirements
When it is about a customer's privacy and data security, organizations in sectors that handle personally identifiable information (PII), such as retail, healthcare and financial services, are subject to tight regulations. These could be as simple as Cyber Essentials or PCI DSS, GDPR, ISO 27001, geographic region or sector-specific requirements.
9) Conduct Audits and Penetration Testing
Whether an organization opts to work with a third-party security provider or keep security professionals in-house, experts recommend that all organizations execute penetration testing to see if existing cloud security measures are sufficient. Continuous vulnerability scans are equally important to keep an eye on changing threat surfaces.
10) Enable Security Logs
A good logging and monitoring system is the eyes and ears of a security team. Organizations should install logging capabilities in their cloud infrastructure. Logging allows all system administrators to keep track of which users are making changes to the environment, something that would be nearly impossible to achieve manually.
When an intruder gains access and modifies any settings or data, the logs will reveal everything they did so that it can be acted upon in the quickest possible time. Monitoring is equally important to ensure alerts are generated at the right moment in case of an unusual event.
One of the most common cloud security problems is misconfigurations, which can lead to a variety of issues. Effective log capturing capabilities will allow changes that resulted in a vulnerability to be connected and corrected, preventing future vulnerabilities.
Conclusion
The above list of security practices is not a done-all checklist to save your organization from cloud security risks. As they say – security never sleeps!
Therefore, it is important to identify your risks, analyze their metrics and act on them, continually improving your organization’s posture.
By conducting third-party validation exercises, a security team can provide the much-needed assurance to assess the gaps and mitigate risks aligned with the risk-focused approach.
Know your data, hack yourself, train yourself, secure your partners and vendors.
Rinse and repeat.
