In a previous blog post, Room For Improvement, I showed that, in order to improve their confidence in data security, organizations should invest in user education, advanced technologies, and the ability to co-ordinate both security policy and incident response. This is all well and good, but what does it achieve, other than helping an organization prove it can meet various regulatory requirements?
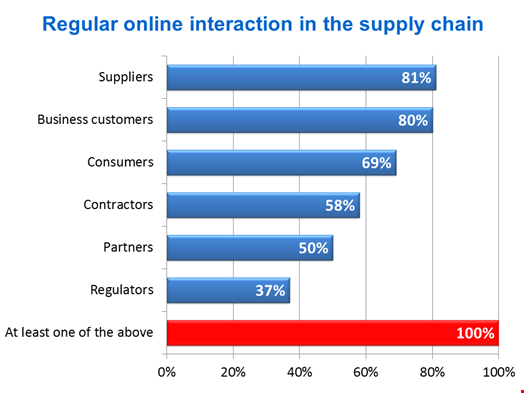
The research reports behind this series of blogs also looked at the impact of confidence in security on information supply chains. Manufacturers and retailers in particular have extensive physical supply chains to move goods around. However, all organizations now share data with external users across public networks through information supply chains and all can exploit these better if they improve their confidence in information security.
The complexity of these information supply chains varies. They are more complex when overlaying an extensive physical supply chain, in larger organizations, and when the individuals and organizations involved cover a broad geographic area. More complexity provides more motivation to invest in the measures that improve confidence in data security. The investments made vary depending on the types of data involved.
In retail, distribution and transport, payment card data is by far the greatest concern. In response there is more likely to be investment in: next generation firewalls (that help deal with the PCI DSS requirement to secure applications); policy-based access rights to cloud resources; and locking down user end-points, for example through configuration change controls and mobile app management.
Financial services firms also worry about payment card data. However, personally identifiable data (PID) comes a close second. To protect PID, similar technologies are favored; however, the degree to which a given organization is more likely than average to invest is considerably higher than it is for payment card data.
The reason for this is that the security of payment card data can be outsourced to payment gateway providers, whilst the ultimate responsibility for PID always remains with the data controller (the business that owns the data) regardless of where it is stored.
When it comes to intellectual property (a big concern for manufacturers), data loss prevention (DLP) and digital rights management (DRM) are high on the list of technologies that are more likely than average to be deployed. Even higher on the list are ways to monitor user behavior in the cloud and on endpoints.
Effective information security is not just about ticking boxes to meet the expectations of regulators (although that is necessary), it is about providing the confidence to safely share information far and wide through the increasingly complex information supply chains that enable business processes. Those which fail to do this will lose the confidence of customers and partners. Losing that will probably damage your business faster than any regulator can.
Quocirca’s report, Weak Links, sponsored by Digital Guardian (a supplier of data protection products), is free to download here.