We need a shared threat actor taxonomy. There is an excessive influx of distinct threat actor taxonomies within the cybersecurity field, prioritizing pride, humor and competition among vendors over the ease and usability for end users.
Vendors argue that multiple naming taxonomies are necessary to “maintain accurate threat tracking and defense procedures.” However, their arguments fall short of the proof of benefit that single taxonomies provide. If they were to look at the entirety of their world and even their own humanity, they would find a single taxonomy to refer to, which has only yielded scientific discovery ease, understanding and innovation.
By considering historical lessons, I propose two recommendations: a taxonomy frame that serves greater utility to end-users than the pride of vendors and an evidence frame to support threat actor classification.
A Page from History: Biological Taxonomy
Human-made taxonomy has a rich global history. As early as 3000BC in China under Shen Nung, an Emperor of China, categorized various minerals, plants and animals. In 1500 BCE, Egyptian taxonomists categorized medicinal plants, and in 300 BCE, Aristotle, a Greek philosopher, made significant contributions in classifying organisms into plants and animals based on attributes.
Hundreds of years later, Medieval thinkers would take these separate systems and explore a more philosophical classification which would lend its hand to the revolution that took place in the 18th century under Carl Linnaeus, a Swedish taxonomist who created the Linnean system, a binomial naming system that we know today. The Linnean system brought order to the field of biological taxonomy by replacing subjective and ambiguous elements with a simple combination of genus and species. For example, the honeybee, which had previously been called Apis pubescens, thorace subgriseo, etc., became Apis mellifera – a simple combination of genus and species. Carl Linnaeus’s work brought structure to the chaotic world of classification and is a prime example of how a single taxonomy is beneficial.
Fundamental Taxonomy Models
The Linnean system uses a hierarchical model to classify the biological system. There are two kinds of taxonomies: hierarchical and faceted.
A hierarchical model (as displayed below) moves from the point of origin into more specific groups until one branch yields a single species. From hierarchical systems, we can derive parent-child, associative and equivalence relationships that connect concepts semantically. Hierarchical systems are only as helpful as viewing relationships from one singular ‘lens’ or organizing principle. A practical example is a family tree.
Faceted taxonomies, on the other hand, separate facets or attributes and clusters under them relevant taxonomies. This type of taxonomy allows for combinations of characteristics that are very detailed. A practical example can be applied to the facets of dresses. While a general category of dresses may sit at the center of the model, different facets, including sleeve length, general length, color, fabric and size, may branch from this category to produce further relevant facets.
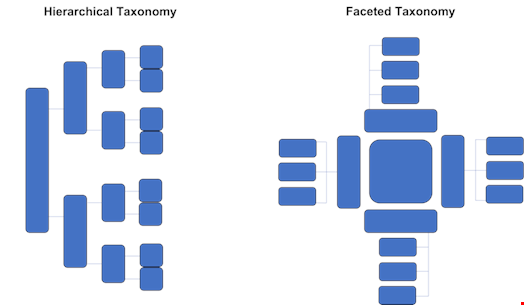
Cybersecurity vendors currently employ a mix of hierarchical and faceted taxonomies. They use faceted taxonomies during their evidence-collection processes. The confluence of factors in a hierarchical taxonomy serves as the grounds upon which they name their threat actors. After naming a threat actor, they use hierarchical taxonomies to study a single threat actor.
Several systems are already in play to lead intelligence teams on their findings journey:
- The Cyber Kill Chain (Lockheed Martin): frames intelligence and evidence collection logic
- The Diamond Model of Intrusion Analysis (U.S. Department of Defense): serves as intelligence gathering methodology
- MITRE ATT&CK Framework (MITRE): serves TTP and technical attack mapping
Combined, these systems can be beneficial to map evidence within a faceted taxonomy, of which I drew a high-level example below:
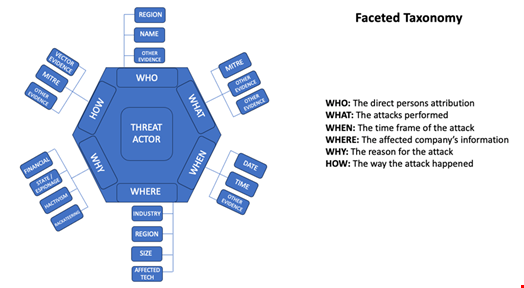
There is room for improvement in my model. This model is meant to serve as the evidence frame from which vendors and threat analysts can organize their conclusions. Please revise and/or enrich this model with your own input.
A Way Forward
Most vendors use a binomial naming system which only includes threat actor motivation and origin. The naming structure I propose is an enriched version of this binomial system. My proposed taxonomy has full utility and no filler words, which lack economy. I also suggest the system consider threat actor impact grade, global reach and activity level.
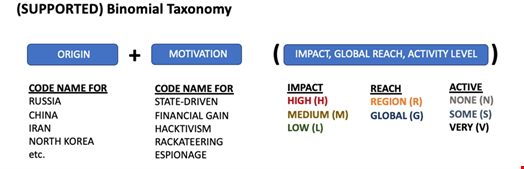
Threat intelligence end users care about the origin, reason, proximity and potential of any threat to their organization. In the model above, I maintain the origin and motivation aspects of the binomial naming structure that most vendors have, though I urge for a single code to apply to origin and motivation. I refuse to reinvent the wheel because revisions in taxonomy create legacy issues. Once tracking systems have threat actor data classified and tagged for tracking, changes in taxonomy structures (apart from adding terms) without rendering existing nodes in systems make threat actors harder to find. Editing existing data is a massive headache. For those pre-existing threat actors tagged, a formalized and unified system would only need a thesaurus data structure applied to build an associative relationship or equivalence relationship among the terms. This is the easiest way for my proposed change to be implemented.
As for the considerations I make in the parenthesis, these terms would be denoted with a one-letter abbreviation for the applicable grade of each consideration. Impact is a sum of financial losses and damaged systems that the threat actor has accrued. Reach gives end users an understanding of how globally prolific these threat actors are and helps researchers understand the limitations or limited focus of any one threat actor for face value. Activity level helps end-users understand if a threat actor has been retired for either disbanding, joining another force or is otherwise just sporadically active.
Parting Words
It’s time to foster a collaborative and ethical spirit about attribution that serves the cybersecurity discipline in a more mature, refined, and helpful regard. To vendors: the value is not in the façade but in the utility of your finding(s).
