Multi-factor authentication (MFA) is one of the recommended cybersecurity measures that is being championed during Cybersecurity Awareness Month. Despite this, experts warn that this security measure is no longer strong enough to protect users from cyber-attacks in 2023.
MFA requires users to provide two or more factors to verify their identity when logging in to an account or performing a sensitive action.
It is an evolution of two-factor authentication (2FA), which has been in existence since 1986 when RSA, a security company, introduced its first password-generating key fob. 2FA and MFA were used in fringe applications in the 1990s and early 2000s. It was only when smartphones became mainstream that MFA started taking off.
What Are the Four Types of MFA?
Most big tech companies, including Google, Microsoft and Apple, offer several MFA login options.
Amazon Web Services (AWS) has announced it would start mandating MFA for all privileged AWS accounts from mid-2024.
MFA can be based on several different factors that are divided into four categories:
- Knowledge factors: something the user knows, such as a password, PIN, or security question answer
- Possession factors: something the user has, such as a smartphone, security token, or smart card
- Inherence factors: something the user is, such as a fingerprint, facial scan, or voice recognition
- Location factors: in a zero-trust cybersecurity environment, your physical location can be an authentication factor
Speaking to Infosecurity, Roger Grimes, a data-driven defense evangelist at cybersecurity awareness company KnowBe4, recommends using MFA over passwords when possible: “It cuts down on around half of phishing attacks.”
Not All MFA Methods Are Phishing-Resistant
However, not all MFA methods are created equal, and many can still be hacked.
“Over 70% of MFA options are nearly as easy to hack with social engineering and phishing emails as using passwords,” Grimes said.
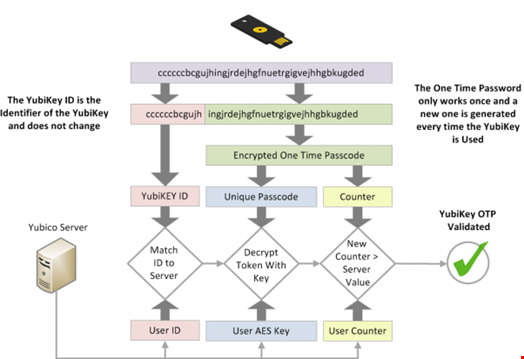
Push-based MFA, where the user receives a notification message to a secondary location to ‘Approve’ or ‘Deny’ whenever anyone tries to log on, SMS-based MFA and email-based MFA are all subject to being hacked.
These three techniques, which use one-time-passwords, are among the most common MFA methods.
However, they are vulnerable to basic phishing attacks involving techniques like business email compromise (BEC) or SIM-swapping.
“It doesn’t take a sophisticated hacker to hack these types of MFA; you just need to follow the steps of current phishing kits,” Grimes warns.
“That’s why the message the US Cybersecurity and Infrastructure Agency (CISA) and other cybersecurity organizations promote should be to use phishing-resistant MFA.”
Most phishing-resistant MFA options use Fast IDentity Online (FIDO) standard protocols.
FIDO standards are a set of open, standardized authentication protocols developed and maintained by the non-profit FIDO Alliance, created in 2013.
FIDO authentication is based on public key cryptography, which is more secure than password-based authentication and is more resistant to phishing and other attacks.
"Many vendors mention their product is 'FIDO2-enabled' when it's clearly not true."Roger Grimes, data-driven defense evangelist, KnowBe4
FIDO supports a variety of authentication methods, including:
- Biometrics: Fingerprint scanners, facial recognition, iris scanners, and voice recognition
- Security keys: Physical devices that plug into a computer or mobile device and can be used to authenticate the user
- Embedded Secure Elements (eSEs): Secure chips that are built into many smartphones and other devices
- Trusted Platform Modules (TPMs): Security chips that are built into many computers.
FIDO authentication is supported by a wide range of web browsers, operating systems, and devices. This makes it easy for users to adopt FIDO authentication without changing their hardware or software.
The latest FIDO protocol is FIDO2, jointly developed by the FIDO Alliance and the World Wide Web Consortium (W3C). FIDO Alliance offers a FIDO certification for vendors to verify their solutions are FIDO compliant.
“I’ve noticed that many vendors mention their product is ‘FIDO2-enabled’ when it’s clearly not true. I’d suggest anyone who wants to adopt a FIDO2-enabled MFA option to turn to a reputable company such as Yubico, Google, Duo or Microsoft,” Grimes argued.
Phishing-Resistant MFA Is Gaining Momentum
Other phishing-resistant MFA options exist outside FIDO, such as passkeys, smart cards or Microsoft Entra certificate-based authentication.
Grimes maintains an extensive list of phishing-resistant MFA options on LinkedIn.
“Whatever MFA option you pick, moving from passwords to MFA is long, difficult and costly. If you have a choice, pick a phishing-resistant MFA option from the beginning, so that you won’t have to change again in the future,” Grimes insisted.
Governments and cybersecurity organizations have been promoting MFA over passwords for a long time, without mentioning the need for phishing-resistant MFA.
This is changing. Many organizations, including CISA and Microsoft, are now pushing for the general adoption of phishing-resistant MFA. This effort is starting to bear fruits. According to the State of Global Enterprise Authentication Survey, published in September 2022 by Yubico, 68% of UK respondents in executive positions and 63% of directors agree that their organization needs to upgrade to modern phishing-resistant MFA.
“Lately, even the US government has added a specific mention to phishing-resistant MFA in the latest version of its Digital Identity Guidelines,” Grimes added.
What Are the Three Types of MFA Bypass?
No MFA is a silver bullet against hackers. “Companies like Microsoft will tell you that MFA cuts down on over 99% of phishing attacks. I don’t believe this figure is true today,” Grimes said.
He argued that, with MFA being pushed everywhere, including during Cybersecurity Awareness Month, many threat actors have started deploying MFA bypass hacking methods.
A position shared by Grimes’ colleague Stu Sjouwerman, founder and CEO of KnowBe4. “All MFA can be hacked,” he wrote in an Infosecurity article.
There are three main approaches to MFA bypass. These are:
- Leveraging MFA fatigue: many users will approve login prompts they didn’t approve, usually because of a lack of concentration that can be due to MFA fatigue. This tactic, called an MFA fatigue attack, has been observed in various intrusions, such as the high-profile breach that impacted Uber in 2022.
- Token theft, which consists of stealing authentication tokens, generally through infostealer malware or adversary-in-the-middle (AiTM) attacks, granted to users upon login and completion of their own MFA challenge. The threat group Lapsus$ used token theft among other techniques, to breach Okta systems in early 2022.
- Targeting MFA misconfigurations: poorly configured MFA methods can be exploited by hackers. In August 2023, software firm Retool announced that the accounts of 27 cloud customers were compromised after the attackers bypassed multiple security controls using SMS phishing and social engineering to compromise an IT employee's Okta account. The firm blamed the hack on a new feature in Google Authenticator that allows users to synchronize their 2FA codes with their Google account.
Read more: MFA Bypass - The Next Frontline for Security Pros
Three Tips to Counter MFA Fatigue Attacks
There are many measures organizations can take to mitigate risks posed by MFA fatigue, alongside providing more awareness training. Here are five ideas to consider:
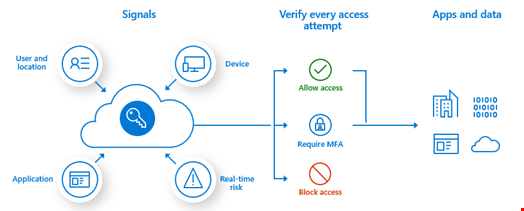
- Tighten authentication regimes: make sure your authentication regime takes into account all known user identity parameters
- Adopt double authentication or adopt a single sign-on (SSO) solution
- Add number matching to authentication requests: rather than just confirming a login attempt, require users to type in a two-digit code from the login screen to authenticate
Read more: Rising AI-Fueled Phishing Drives Demand for Password Alternatives

