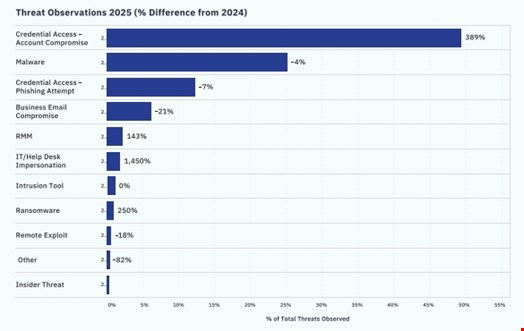
Cyber threat actors went all in on credential theft in 2025, with eSentire reporting a 389% year-over-year rise in account compromise, making up 55% of all attacks observed by the cybersecurity firm.
The firm’s 2025 Year in Review & 2026 Threat Landscape Outlook Report, published on January 15, 2026, showed that credential access represented 75% of the malicious activity observed in the wild by its Threat Response Unit (TRU) over the reported period.
Two-thirds of it was aimed at conducting account takeovers and another third to deliver phishing campaigns. Microsoft 365 accounts were prime targets, noted eSentire
Meanwhile, malware continued to be a prime threat, accounting for 25% of threats observed in the wild, but declined by four percentage points compared to 2024 data.
PHaaS Fueled Business Email Compromise
The use of valid credentials to spread email-based malicious campaigns was the top initial access vector among incidents experienced by over 2000 of eSentire customers, rising from 37% to 55% of total security incidents year-over-year.
Most of these attacks stemmed from operations enabled by phishing-as-a-service (PhaaS) kits, which accounted for 63% of all account compromise incidents.
Additionally, the report noted that threat actors use PhaaS operations like Tycoon2FA, FlowerStorm and EvilProxy to carry out business email compromise (BEC) attacks.
Spence Hutchinson, senior manager of TRU and lead investigator for the report, highlighted the sophistication of some PHaaS kits. “These PhaaS kits are not made up of simple templates; they are comprehensive, continuously updated offerings, designed to bypass modern security controls, such as multifactor authentication (MFA). It is the widespread availability and continuous evolution of these PhaaS kits that are fueling the account takeover epidemic that is impacting businesses."
While BEC represented less than 10% of malicious activity observed in 2025 – a 21-percentage point decline compared to 2024 – it continued to be a top threat for companies, the TRU researchers said.
“The hackers can initiate BEC actions, such as creating inbox forwarding rules in as little as 14 minutes, after they have captured a target’s corporate login credentials and session token and successfully entered the target’s IT network,” reads the report.
Companies in real estate, finance, retail and construction are the sectors most targeted by BEC attacks.
Key Highlights from eSentire’s 2025 Threat Report
Other key highlights from the eSentire report included:
- A 14 times increase of security incidents involving the combination of email bombing and IT Help Desk impersonation attacks, with companies in the legal industry most targeted
- A 300% spike of the ClickFix lure, representing over 30% of all malware delivery cases
- The software industry experiencing the largest numbers of security incidents in 2025 (+15% compared to 2024), followed by manufacturing, which saw a 32% year-over-year increase, and business services with an 8% increase from last year
- The construction industry and the hospitality and legal sectors benefiting from a decrease in cyber incidents in 2025
Read now: ClickFix Social Engineering Sparks Rise of CastleLoader Attacks
